Daily News Update: Wednesday, March 26, 2025 (Australia/Melbourne)


EncryptHub Linked to MMC Zero-Day Attacks on Windows Systems

Trend Micro have linked the threat actor EncryptHub to attacks exploiting a zero-day vulnerability in Microsoft Management Console (MMC) vulnerability dubbed 'MSC EvilTwin' (CVE-2025-26633), as far back as April 2024.
The vulnerability allows attackers to bypass Windows file reputation protections and execute code without warning the user.
EncryptHub (a.k.a. Water Gamayun, Larva-208) used the zero-day to execute malicious code and exfiltrate data from compromised systems, deploying payloads including the EncryptHub stealer, DarkWisp backdoor, SilentPrism backdoor, Stealc, Rhadamanthys stealer, and the PowerShell-based MSC EvilTwin trojan loader.
Bleeping Computer | "EncryptHub linked to MMC zero-day attacks on Windows systems"
Windows Zero-Day Leaks NTLM Hashes, Unofficial Patch Released

A new Windows zero-day vulnerability allows remote attackers to steal NTLM credentials by tricking targets into viewing malicious files in Windows Explorer. The stolen credentials can then used in the wild to perform NTLM relay and pass-the-hash attacks to gain unauthorized access to sensitive data.
"The vulnerability allows an attacker to obtain user's NTLM credentials by having the user view a malicious file in Windows Explorer - e.g., by opening a shared folder or USB disk with such file, or viewing the Downloads folder where such file was previously automatically downloaded from attacker's web page" - ACROS Security CEO Mitja Kolsek
The vulnerability, which hasn't been assigned a CVE yet, affects all versions of Windows from Windows 7 to the latest Windows 11 releases. ACROS Security is providing free and unofficial security patches through its 0Patch micropatching service until Microsoft releases an official fix.
Bleeping Computer | "New Windows zero-day leaks NTLM hashes, gets unofficial patch"
HaveIBeenPwned HasBeenPwned

Infosec veteran Troy Hunt of HaveIBeenPwned notified approximately 16,000 people after falling victim to a sophisticated Mailchimp phishing attack.
The attackers gained access to his Mailchimp mailing list by using a well-crafted phishing email that created a sense of urgency.
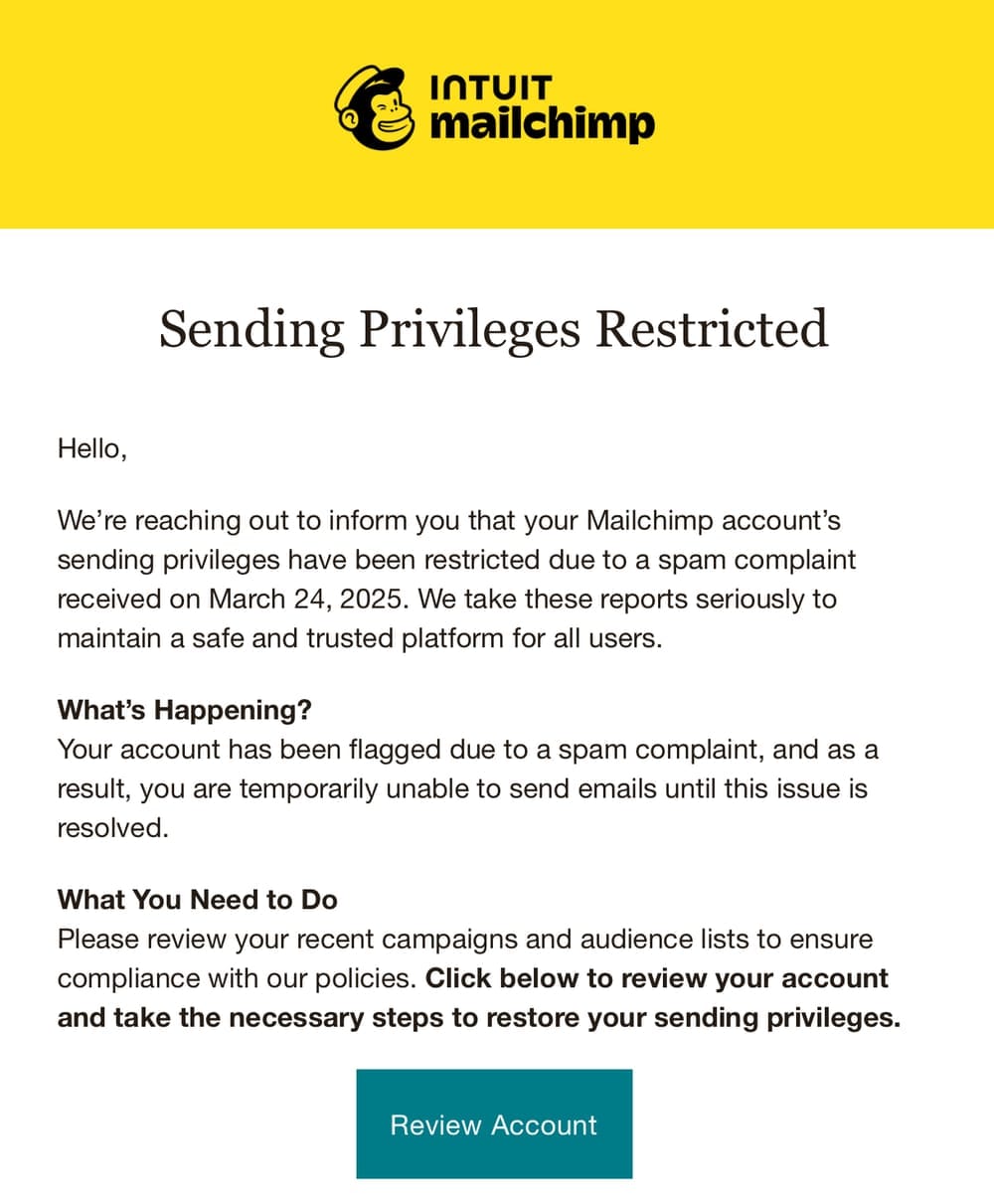
Hunt entered his credentials and one-time passcode (OTP), leading to the export of his mailing list in under two minutes, despite him resetting his password immediately upon realising his mistake.
"This was obviously highly automated and designed to immediately export the list before the victim could take preventative measures."
He noted that Mailchimp's use of OTPs, rather than phishing-resistant 2FA methods, made him vulnerable to the automated attack. Hunt also highlighted the importance of monitoring whether password managers auto-fill credentials on websites as an indicator of phishing sites.
Troy Hunt | "A Sneaky Phish Just Grabbed my Mailchimp Mailing List"
The Register | "Infosec pro Troy Hunt HasBeenPwned in Mailchimp phish"
Customers Confirm Data Legitimacy of Oracle Breach

Oracle Cloud's denial of a security breach is looking increasingly like a premature and misinformed/misleading response, as several customers confirm that the leaked data is genuine.
Alon Gal, co-founder and CTO at Hudson Rock received a sample of the data from the perpetrator of the alleged hack, and confirmed that multiple Hudson Rock customers verified the data as legitimate and originating from Oracle Cloud's internal systems.
CloudSEK also received the sample and corroborated its authenticity, noting the difficulty in fabricating such detailed information. If the data is genuine, it could enable cybercriminals to carry out supply chain and ransomware attacks. Experts advise affected organizations to rotate SSO and LDAP credentials and implement strong password policies and MFA.
"There has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data." -Oracle
The Register | "There are perhaps 10,000 reasons to doubt Oracle Cloud's security breach denial"
Cyberattack Causes $1 Million Loss for South Africa’s Astral Foods

Astral Foods, South Africa’s largest chicken producer, suffered a cyberattack on March 16, resulting in a $1 million loss due to delivery delays and operational downtime.
The company implemented its disaster recovery protocols, and all business units are now operating normally. Astral Foods confirmed that no confidential customer, supplier, or stakeholder data was compromised.
The incident is expected to significantly decrease earnings per share for the current financial period. The company did not disclose the type of attack or the responsible parties.
The Record | "Cyberattack causes delays for South Africa’s largest chicken producer"
New Android Malware Uses .NET MAUI to Evade Detection

New Android malware campaigns use Microsoft's cross-platform framework .NET MAUI to evade detection. The malware disguises itself as legitimate services and stores malicious code inside binary blob files, which are not typically scanned by Android security tools.
McAfee's Mobile Research Team observed these campaigns targeting users in China and India. The malware uses multi-layered encryption (XOR + AES), staged execution, and TCP sockets for command-and-control (C2) communications.
The malware typically masquerades as banking, communication, dating, and social media apps. To minimize the risk of infection, users should avoid downloading Android APKs from third-party app stores and ensure Google Play Protect is active.
Bleeping Computer | "New Android malware uses Microsoft’s .NET MAUI to evade detection"
Browser-in-the-Browser Attacks Target CS2 Players' Steam Accounts

A new phishing campaign targets Counter-Strike 2 players using Browser-in-the-Browser (BitB) attacks to steal Steam accounts.
The attackers impersonate the Ukrainian e-sports team Navi to lure victims to phishing sites promising free CS2 loot cases. These sites use the BitB technique to display a realistic-looking Steam login page within the browser, tricking users into entering their credentials. The stolen accounts are then resold on grey markets.
To protect Steam accounts, users are advised to activate multi-factor authentication, enable 'Steam Guard Mobile Authenticator,' and regularly review login activity for suspicious sign-ins.
Bleeping Computer | "Browser-in-the-Browser attacks target CS2 players' Steam accounts"
Broadcom Warns of Authentication Bypass in VMware Tools

Broadcom released security updates to fix a high-severity authentication bypass vulnerability (CVE-2025-22230) in VMware Tools for Windows.
The vulnerability, caused by an improper access control weakness, allows local attackers with low privileges to escalate privileges on vulnerable VMs through a low-complexity attack.
Bleeping Computer | "Broadcom warns of authentication bypass in VMware Windows Tools"
CrushFTP Warns Users to Patch Unauthenticated Access Flaw

CrushFTP warned customers of an unauthenticated HTTP(S) port access vulnerability impacting v10 and v11 versions, which would allow attackers to gain unauthenticated access to unpatched servers exposed on the Internet.
"The bottom line of this vulnerability is that an exposed HTTP(S) port could lead to unauthenticated access. The vulnerability is mitigated If you have the DMZ feature of CrushFTP in place."
According to Shodan, over 3,400 CrushFTP instances have their web interface exposed online to attacks, although BleepingComputer couldn't determine how many have already been patched.

Bleeping Computer | "CrushFTP warns users to patch unauthenticated access flaw immediately"
Kubernetes Ingress-Nginx Flaw Exposes Clusters to Takeover

Wiz researchers discovered critical vulnerabilities in the admission controller component of Ingress-Nginx Controller, potentially allowing complete takeover of Kubernetes clusters.
The vulnerabilities, collectively dubbed IngressNightmare, involve injecting arbitrary Nginx configurations by sending malicious ingress objects to the admission controller. This can lead to remote code execution (RCE) on the Ingress-Nginx Controller’s pod, granting access to all cluster secrets across namespaces.
Wiz estimates that over 6,500 publicly accessible Kubernetes installations are at risk.
Fixes for five CVEs were released on March 10 in Nginx Controller versions 1.12.1 and 1.11.5. Wiz recommends upgrading immediately or, if that's not possible, enforcing strict network policies and temporarily disabling the admission controller component.
The Register | "Public-facing Kubernetes clusters at risk of takeover thanks to Ingress-Nginx flaw"
Trump Officials' Signal SNAFU Exposes Classified Yemen Airstrike Plans

Senior Trump administration officials accidentally invited The Atlantic editor Jeffrey Goldberg to a Signal group where they discussed classified plans to attack Houthi rebels in Yemen.
Participants included US National Security Advisor Michael Waltz, Vice President JD Vance, Secretary of Defense Pete Hegseth, Secretary of State Marco Rubio, Director of National Intelligence Tulsi Gabbard, and Homeland Security Advisor Stephen Miller.
The officials shared highly classified information, including details of planned attacks, weapons to be used, and strategies for public communication.
Military analyst Mick Ryan described the use of Signal for such sensitive issues as “appalling,” questioning why more secure government-assured communication tools were not used. Senator Adam Schiff has called for an immediate investigation into the incident.
“By using Signal for such a sensitive issue, the participants demonstrate a cavalier attitude to operational security,”
The Register | "Top Trump officials text classified Yemen airstrike plans to journo in Signal SNAFU"
FCC Investigates Huawei and Other Chinese Telecoms

The FCC is scrutinising Chinese manufacturers on its "Covered List," including Huawei, to determine if they are circumventing US regulations. The investigation involves formal inquiries and subpoenas to entities suspected of operating in the US despite being deemed national security risks.
FCC boss Brendan Carr stated that the FCC is working to identify and close loopholes that allow "untrustworthy, foreign adversary state-backed actors" to skirt the rules.
The probe extends to companies like Hytera Communications, Hangzhou Hikvision Digital Technology, Dahua Technology, China Mobile International USA, Pacifica Networks, and China Unicom (Americas).
The Register | "FCC on the prowl for Huawei and other blocked Chinese makers in America"
Privacy-Boosting Tech Could Prevent Breaches with Government Aid

A report by New America’s Open Technology Institute recommends that governments prioritize the use of privacy-enhancing technologies (PETs) like encryption, de-identification, and hashing to prevent breaches and data misuse.
The report suggests governments incentivize the advancement of these technologies through procurement policies, guidelines, and grants.
PETs include encryption and synthetic data, which reflects properties of real-world data without containing authentic personal information. The report emphasizes the need for a privacy-first approach to data sharing to safeguard against unauthorized access.
CyberScoop | "Privacy-boosting tech could prevent breaches, data misuse with government aid, report says"