Infosec News of the Day
28/06/2022

Threat Actor Reporting
Black Basta claim nearly 50 victims in two months
Source: The Hacker News
The Black Basta ransomware operation were cited alongside Karakurt and BlackByte as one of three operations former Conti affiliates had splintered into, following their apparent disbanding just weeks ago.
The highly skilled operators have clearly gotten straight to work, racking up nearly 50 scalps in a number of industries, throughout the US, UK, Australia, Canada and New Zealand.
This group is one to keep an eye on. In particular, take note of their use of Qakbot for initial access, and fondness of popping Linux servers running VMWare ESXi to achieve their objectives.
Lockbit continue to innovate the ransomware production line
Lockbit - a group credited with conducting 40% of all ransomware attacks in May this year - have released v3.0 of their ransomware. While the technical enhancements have not yet been assessed, what’s as - if not more - interesting are the changes they’ve made to their monetisation workflow.
Bug Bounty for bad guys: Got an idea for how to improve their tooling? Found issues in their infrastructure or code, or just want to dox someone of interest? Lockbit will pay between $1k and $1 million for your input;
zCash as payment: While Bitcoin and Monero have been accepted by Lockbit for some time now, Bitcoin has proven traceable and Monero isn’t widely available for purchase in the US. zCash is the best of both worlds - a privacy coin available for purchase on Coinbase.
Simplified transactions: Lockbit’s leak site has been modified to allow the option for anyone to pay to either extend the countdown timer by 24 hours, or to purchase or destroy all stolen data.
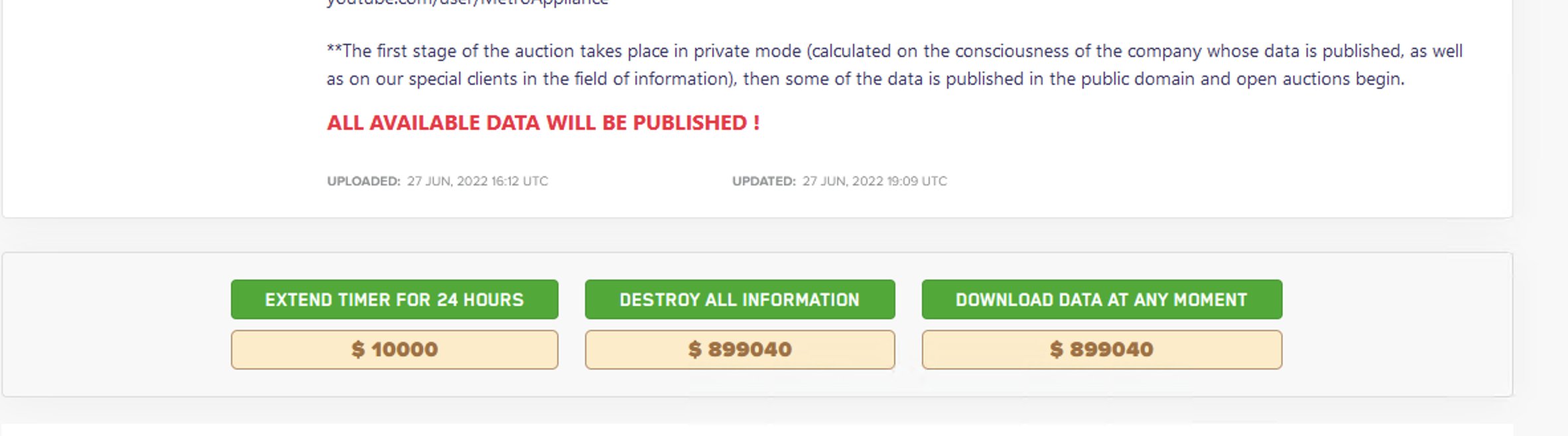
These changes mark the latest attempt by ransomware actors to improve the monetisation of their ransomware attacks. With ransomware-specific legislation being rolled out across the world and law-enforcement action taking down former heavyweights such as Trickbot, REvil and the FluBot Android botnet, cyber crims are cluing on to the fact they need to work both harder, and smarter, to stay ahead of the game.
Eternity Malware-as-a-Service sold on Telegram for as little as $90
Various modules for a new MaaS offering dubbed the “Eternity Project” are being offered for sale on Telegram, with prices ranging from $90 for a coin miner to $490 for access to their ransomware.
While the code has been assessed to have been largely repurposed from Github repositories - as you’d expect for the price - that’s not the main takeaway here.
Offensive tooling is widely available and accessible, for cheap. The ecosystem will continue to grow and diversify, so it’s more important than ever to not fixate on chasing the latest threat to hit the shelves, but look for common TTPs and detection points that can be used to amplify your detection coverage.
TTP Updates
Qakbot
Prominent malware, spread via malspam and email thread hijacking to enable initial access. Recently identified used during BlackBasta (apparent Conti Ransomware successor) campaign.
TA570/TR01 (AA)
CHANGE: Use of Javascript downloader for dll file instead of direct from lnk - url > .zip > .lnk > .js > .dll
Execution: lnk > cmd > curl (js) & wscript (js) > ping (sleep) > regsvr32 (dll)
TA577 (obama194)
UNCHANGED: html smuggling > .zip > .lnk > .dll (signed by FLY BETTER s.r.o.)
Execution: lnk > curl (dat > jpg) > regsvr32 (jpg)
BumbleBee
First identified mid-March 2022, a malware enabling initial access that is spread via malspam and email thread hijacking. It appears to be the successor to the BazarLoader malware based on increase in volume as BazarLoader has decreased. Google TAG attribute this to an Initial Access Broker for the former Conti ransomware group, tracked as EXOTICLILY.
- UNCHANGED: .zip > .iso > .lnk > .dll
Vulnerabilities
Active Exploitation: Atlassian Confluence Server and Data Center vulnerability
CVE-2022-26134 is continuing to be hammered by threat actors including by ransomware operators seeking to drop AvosLocker and Cerber2021/CerberImposter ransomware payloads.
The vulnerability allows for Remote Code Execution and a Proof-of-Concept exploit has been released - given this, it was inevitable that we’d see the wide-scale exploitation currently under way.
If you have an vulnerable, internet exposed instance that you haven’t patched yet - consider it compromised and take steps to secure and scan your network to identify and evict any potential infections.
Awaiting Patch Release: OpenSSL Code Execution vulnerability
The latest release of OpenSSL - 3.0.4 - has been diagnosed with a bug that could enable code execution and information disclosure, just one week after it was released to address a separate command-injection vulnerability (CVE-2022-2068).
While some publications have seized on the researcher’s - rather pointless - speculation that it could be worse than Heartbleed despite no evidence of it being remotely exploitable, the scope for impact is incredibly limited.
- The vulnerable version has only been released for a week, and is unlikely to have been applied at any meaningful scale;
- Many orgs and applications still use the 1.1.1 release tree of OpenSSL;
- It only affects x64 running Intel's Advanced Vector Extensions 512 (AVX512) - only present on certain chips released between 2016 and 2022.
All this is to say - be alert, not alarmed. The scope is limited; it doesn’t appear to be remotely exploitable, and bug has been fixed and is awaiting release in the next patch.
Tradecraft
Part 2 of @kostatsale’s series on Threat Hunting:
Core competencies and a ton of great resources included down the bottom to help get you up to speed
A fantastic thread with useful resources for all your Sentinel and KQL query crafting needs!
The Center for Threat-Informed Defense and Fujitsu have worked together to create the ATT&CK Powered Suit Chrome extension that allows you to easily search ATT&CK TTPs, without having to open another tab or leave your browser - check out!
The WiFi Exploitation Framework (WEF) with support for most modern WiFi attacks, including automated hash cracking, bluetooth hacking and more
The Cutter reversing framework has been updated with a bunch of new features including auto-detection of common library functions, a YARA plugin to quickly create and test signatures, and more