Infosec News of the Day
29/06/2022

Threat Actor Reporting
RansomHouse add AMD to data leak site
RansomHouse - a data extorsion group that partners with ransomware groups to obtain and leverage stolen victims data to extract payment - has listed semiconductor manufacturer AMD on their data leak site, claiming to have stolen ~450GB of data.
The group claim this includes research and financial information, but haven’t reached out to AMD as their “partners” consider it to be a “waste of time” and are instead opting to sell the data.
AMD are currently investigating, but there are currently no further details on means of intrusion or payment demand being made by RansomHouse.
RansomHouse first emerged in December 2021, and have since amassed a tally of just six victims, including AMD. While they are nowhere near as prolific as operations such as Conti or Lockbit, they appear to be highly selective in their victims.
The fact they appear to be effectively offering monetisation-as-a-service to ransomware groups is noteworthy, as is the fact they’ve stated they’d rather sell the victim’s data instead of negotiating with them.
If you want to read more on them, Catalin has you covered with links to relevant resources here
Evilnum APT pivot from FinTech to…migration services?
zScaler have released a report on their analysis of an intrusion observed in March where the Evilnum APT group breached an intergovernmental organisation dealing in international migration services. zScaler note that the timeline and target coincided with the Russia-Ukraine conflict, though refrained from taking that final step to pointing the finger at any one nation/entity.
The report notes that the actors made use of macro-enabled documents that employed VBA code stomping to mitigate analysis and reversing, before going on to use obfuscated JavaScript and scheduled tasks to establish persistence.
The actor further “registered multiple domain names using specific keywords related to the industry vertical targeted”, with multiple domains undetected by security vendors, implying the group was capable of operating undetected for some time.
Evilnum have a long history, with the malware first observed in 2018 and undergoing many iterations in the time since then. Their experience and success in infiltrating FinTech companies is clearly coming in handy as the chess pieces are moved on in the cyber domain of the war in Ukraine.
AvosLocker adopt Sliver & commercial scanners in recent campaign
Source: Cisco Talos
A write-up of a recent IR activity responding to an AvosLocker intrusion highlighted the ransomware’s adoption of both CobaltStrike and the open source Sliver framework to maintain a presence on victim networks, as well as use of the commercially available SoftPerfect Network Scanner.
Not a whole lot to unpack here, though it does reinforce the need to monitor for PUPs in your network, and is a timely reminder of the increasing adoption of Sliver by several threat groups in rotation.
Raccoon Stealer v2.0 hits the shelves
After Raccoon Stealer went on hiatus for several months with the apparent death of key developer in the war in Ukraine back in March this year, the popular infostealer is back with a new version.
Advertised in their dedicated Telegram channel, the developers claimed it had “improved software, back-end and front-end […] with a focus on performance and efficiency.”
Core features such as credential/cookie theft; file downloading, loading and exfiltration, are all still available.
Raccoon Stealer enjoyed a moderate spike in success upon its release, with large scale operations such as TA570 seen adopting it in their malspam campaigns for a while, as well as the well-known RIG Exploit Kit. Unfortunately, the latter has swapped Raccoon Stealer out for Dridex in recently observed campaigns - time will tell if this new update will bring its’ developers back to their glory days, but it’s one to watch.
New tricks uncover TOR server’s public footprint
Source: Cisco Talos
Researchers from Cisco Talos have used TLS Certificate attributes and website favicons to uncover the true public IP addresses of several TOR servers used by ransomware groups including DarkAngels, Snatch, Quantum, and Nokoyawa.
Correlation based on TLS Certificates is actually quite straightforward - plugging the Certificate Serial Number from the group’s TOR server into Shodan highlighted an internet-joined server using a matching certificate that belonged to the same group.
Favicon correlation is also possible through Shodan, all it takes is plugging in the favicon hash for a favicon hosted on the actor’s TOR infrastructure, and any publicly addressed infrastructure will be revealed
Some interesting research from Cisco Talos, offering a very straightforward way for hosting providers to discover and take down malicious infrastructure. I wonder if this would scale better with JARM/JA3S hashes to potentially provide a more flexible fingerprint than Certificate Signatures?
TTP Updates
Qakbot
Prominent malware, spread via malspam and email thread hijacking to enable initial access. Recently identified used during BlackBasta (apparent Conti Ransomware successor) campaign.
TA577 (obama195)
UNCHANGED: html smuggling > .zip > .lnk > .dll (signed by Power Save Systems s.r.o.)
Execution: lnk > curl (dat > rtf) > regsvr32 (rtf)
BumbleBee
First identified mid-March 2022, a malware enabling initial access that is spread via malspam and email thread hijacking. It appears to be the successor to the BazarLoader malware based on increase in volume as BazarLoader has decreased. Google TAG attribute this to an Initial Access Broker for the former Conti ransomware group, tracked as EXOTICLILY.
CHANGED: email > url > WeTransfer landing > WeTransfer zip > 2 IMGs > .lnk > .rsp > .dll
The use of WeTransfer and IMGs containing lnk files is not new, but what is noteworthy is the use of rsp files, invoked through odbcconf.exe
RSP - Windows Response File containing the regsvr parameter to invoke a dll
odbcconf.exe - command-line tool for configuring ODBC drivers and data source names
While this breaks detections built on the expected lnk > dll invocation and/or direct use of regsvr32, @kostastsale notes use of the odbcconf.exe binary is uncommon, and makes a decent starting point for hunt/detection efforts.
Worth noting the detection for the zip, IMG and lnk files are low, at 4, 4 and 1 respectively on VT. The DLL remains reasonably well detected though, with 20 vendor detections.
h/t to Kelsey for her continued great work in tracking this threat and keeping us all across changes in its campaigns and TTPs!
Vulnerabilities
FabricScape bug impacts Azure Service Fabric Linux Workloads
Researchers from Palo Alto’s Unit 42 have reported a new vulnerability - CVE-2022-30137 - which could enable attackers to elevate permissions and seize control of all notes in a cluster deployed on Microsoft Azure’s Service Fabric.
The bug only impacts Linux workloads due to the need to create symbolic links as part of a “symlink race” performed during exploitation.
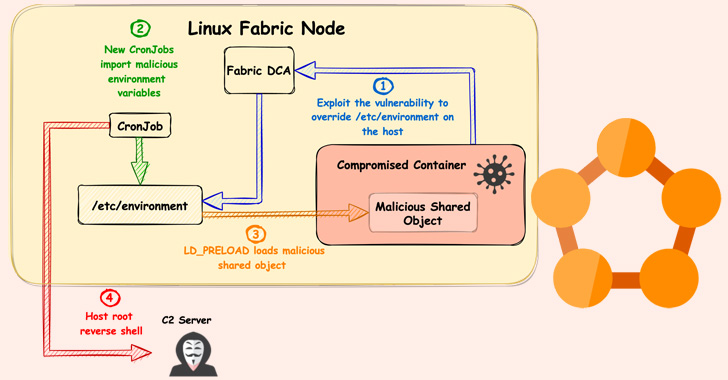
While there is no evidence of the vulnerability being exploited in-the-wild, it’s worth investigating and patching as soon as possible if your enterprise makes use of Azure Service Fabric.





