SOC Goulash: Weekend Wrap-Up
23/01/2023 - 29/01/2023

Malvertising enables ransomware, theft of Master Passwords
The phenomenon of Malvertising and SEO-Poisoning has become an unwelcome fixture of 2023, and is already being added to ransomware infection chains and abused in campaigns aiming to unlock credential vaults for password management solutions.
What else but ransomware
Security researcher Germán Fernández has this week highlighted two campaigns linked to actors distributing Royal ransomware and CLOP ransomware - both of which leveraged malicious Google Ads to distribute their first-stage malware.
He linked the first to DEV-0569, a threat group that was delivering Ursnif and the Redline infostealer via fake Google Ads for a screenshot software called LightShot.
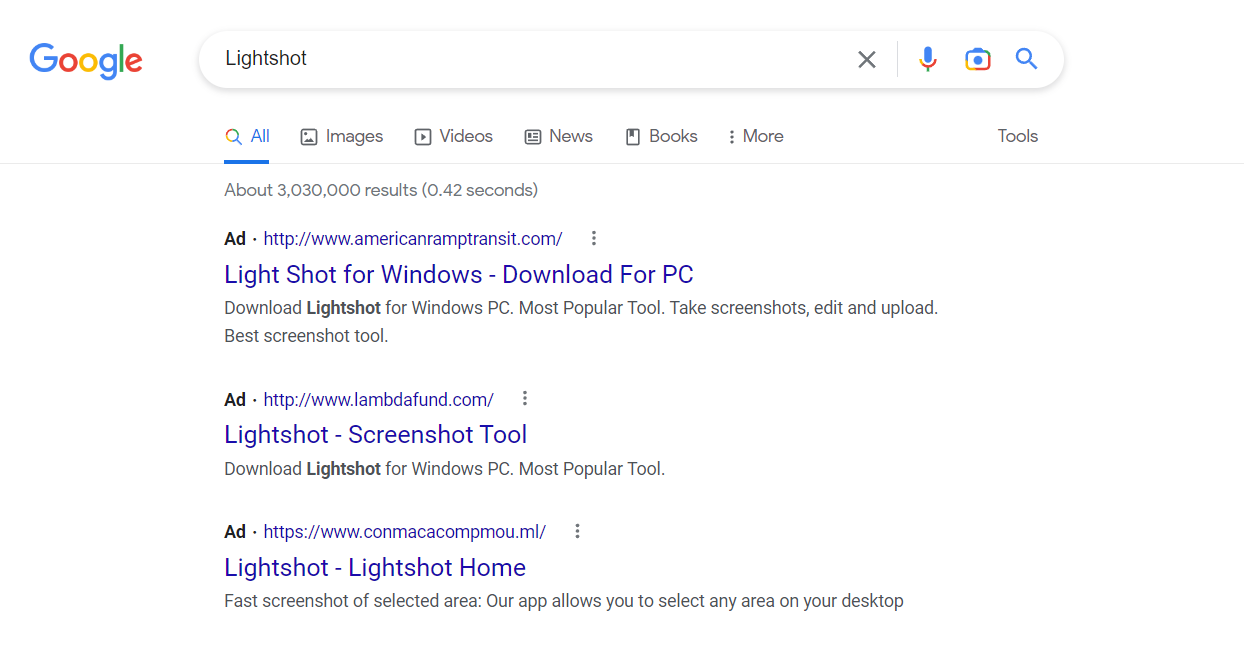
The Ursnif and Redline payloads were found to have been downloaded approximately 2.5k times each as of the 18th of January, and given previous activity and reporting, is believed to potentially result in follow-on activity with Cobalt Strike and the eventual deployment of Royal ransomware.
The second campaign flagged by German leveraged fake Ads pretending to serve up installers for AnyDesk, Zoom, TeamViewer, Slack, and more. Given historical ownership of a domain used to deliver the 2nd-stage payload, this was tentatively linked to TA505 - a threat group which is known to conduct attacks which culminate in the execution of CLOP ransomware.
Trust me, I’m not a clone
Furthermore, Password managers are a natural bottleneck for attackers seeking credentials, and have unsurprisingly been targeted in the broader uptake of Malvertising. Fake Ads for solutions such as Bitwarden and 1Password have been observed in-the-wild, pointing unsuspecting users to cloned sites that attempt to harvest master passwords which can be used to unlock their victims’ credential vaults.
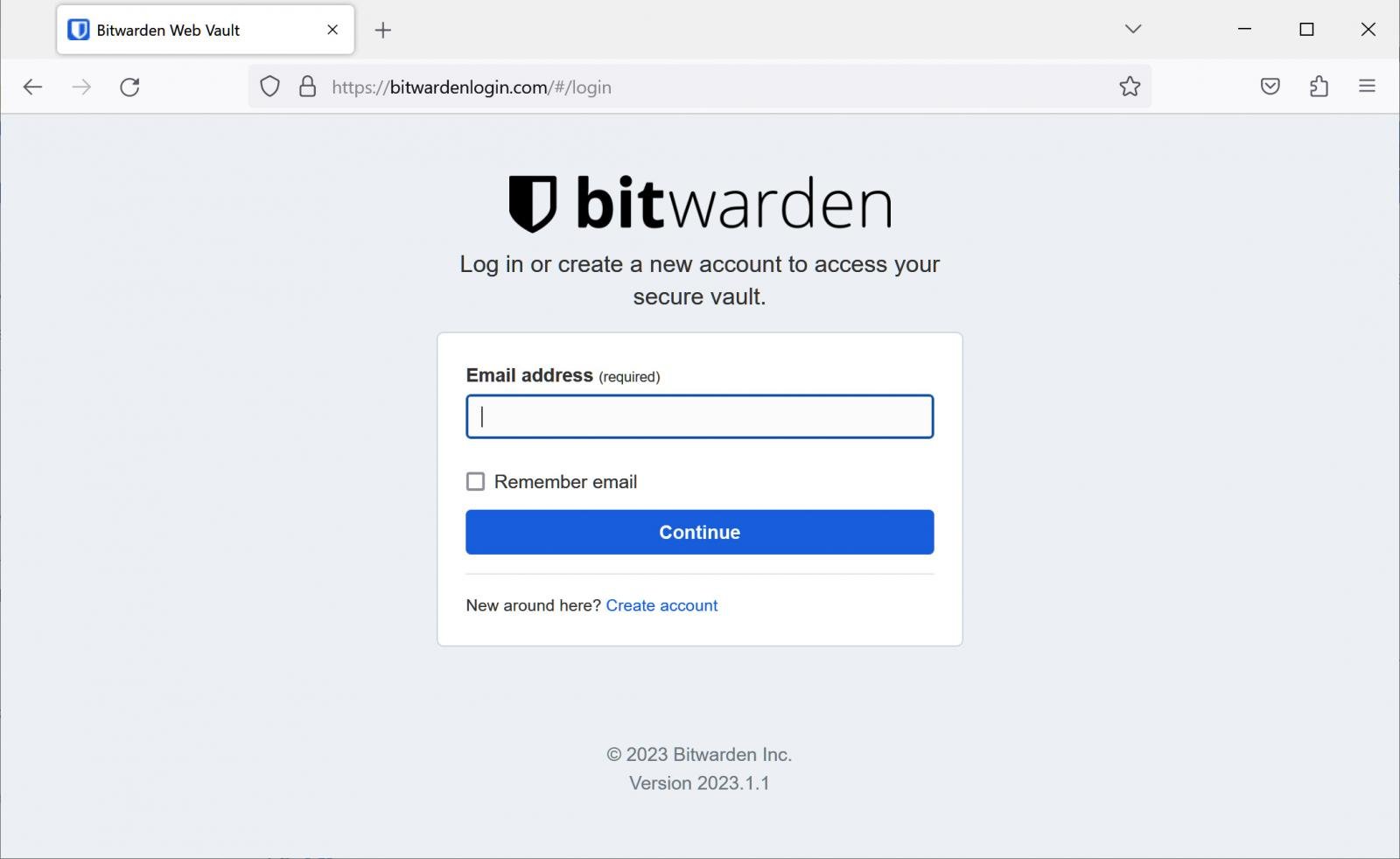
The uptake of Malvertising is well and truly underway and is being leveraged by highly capable threat groups such as DEV-0569 and TA505.
For those in charge of defending enterprise networks - ensure users are aware of the threat this poses, and get Ad Blockers installed on every networked device you can get your hands on.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber.
Hive ransomware disrupted, put on notice
You love to see it - law enforcement not only taking down the infrastructure of a ransomware group, but adding that they loitered in their systems for six months to gather information, and caused the group to lose out on approximately $130 million in ransomware payments.
That was the punchline of a joint statement issued earlier this week by the US DOJ and Europol, with Hive ransomware the apparent target of their operation.

The FBI were able to gain access to the ransomware gang’s infrastructure in July 2022, and leveraged this to steal over 1,300 decryption keys for active or historical victims, as well as “records of Hive communications, malware file hash values, information on Hive’s 250 affiliates, and victim information.”
The stolen decryption keys allowed the FBI to prevent payment of approximately $130 million in payments - a significant sum for a group that the FBI reported had earned approximately $100 million in attacks of over 1,300 companies worldwide, in the period between June 2021 and November 2022.
Sadly, Hive’s ransomware compatriots have been less than sympathetic to their plight:
Ransomware group comment to the HIVE take down:
— vx-underground (@vxunderground) 4:38 AM ∙ Jan 27, 2023
ALPHV: This would not work on us, we have too strong security and we do not store anything on our servers
BianLian: Too bad. I think they will be restored under a new name
Lockbit: Nice news. I love when FBI pwn my competitors
Oh no, we’re not done yet
The US Department of State followed up on the takedown by offering a $10 million reward for any information linking Hive or other cyber actors targeting US Critical Infrastructure to a foreign government.
FBI disrupts the Dark Web site of the Hive ransomware group.
— Rewards for Justice (@RFJ_USA) 5:15 PM ∙ Jan 26, 2023
If you have information that links Hive or any other malicious cyber actors targeting U.S. critical infrastructure to a foreign government, send us your tip via our Tor tip line. You could be eligible for a reward.
If the “wanted” poster isn’t enough to put the operators and affiliates of Hive ransomware on edge, the fact that the communications and information on 250 of Hive’s affiliates is in the hands of law enforcement is sure to have them reconsidering that next holiday to Thailand.
Law enforcement are likely already busy sifting through and analysing the stolen data, connecting the dots and building cases to further prosecute the group and its members.
Hive now know that they have the attention of the authorities, but given the patient and methodical approach to information-gathering taken during the takedown operation - the disruption of their infrastructure may be just the start of their troubles.

North Korean actors quick to adapt to cyber crime landscape
Proofpoint researchers have shared a report that highlights the agile operations of TA444 - a financially-motivated, state-sponsored North Korean threat group that overlaps with APT38/BlueNoroff activity. TA444 is tasked with generating revenue for the heavily-sanctioned hermit kingdom, and have switched from targeting banks to pilfering cryptocurrency wallets and infrastructure since at least 2017.
As many cyber crime actors began experimenting with alternate payload delivery methods in 2022, TA444 was observed to largely mirror these developments as they took place. The group delivered payloads in the form of MSI installers, disk image files to bypass Mark-of-the-Web restrictions (e.g. .vhd and .iso), and HTML Smuggling via compiled HTML files (.chm).
Their attention to detail in crafting convincing and targeted lures and personas continued, though Proofpoint noted an unusual and significant diversification in delivered payloads - a likely indicator of dedicated, and possibly embedded malware development workforce that is supporting the threat group in their endeavours.
Proofpoint’s analysis of TA444’s recent activity is a timely reminder of the significant capability that underpins North Korea’s cyber workforce.
Organisations operating in the cryptocurrency and DeFi space should be wary of this threat group, which the FBI just attributed as having conducted the $100 million heist of the Harmony Horizon Bridge in June 2022 - a haul which unbelievably makes up just 10% of the $1 billion stolen in 2022 altogether.
Found this useful? Why not share it!
Other Reporting
- Federal US Civilian Agencies have been the subject of a “widespread, financially motivated” campaign which saw actors employing Call-back Phishing attacks to gain access to agency networks. The lures impersonated brands such as Microsoft and PayPal, and delivered Remote Monitoring & Management software such as AnyDesk and ScreenConnect as 2nd-stage payloads;
- The NCSC have warned of an increase in spear-phishing attacks from the Russian SEABORGIUM/TA446 threat group and Iran’s APT42/TA453. The attackers invest time in creating convincing lures and personas, before enticing the victim to click a malicious link to harvest their login credentials and using mail forwarding rules to effectively tap the victim’s email account;
- This report by Trend Micro has some fantastic information on Vice Society, including a breakdown of last year’s targeting by sector and country; a chronology of their use of various ransomware strains, and a listing of some of their typical TTPs to help defenders;
- The ACSC has published a ransomware profile for Royal ransomware, operated by the threat group DEV-0569;
- Trellix has shared their technical analysis of an ongoing GuLoader campaign, including its use of executables generated using the Nullsoft Scriptable Install System (NSIS);
- From one loader to another - Mandiant have this detailed technical analysis of the evolution of the GootLoader malware and infection chain;
- Trend Micro have produced another great report, this time with an overview of a new ransomware variant called Mimic. The ransomware appears to be built on leaked Conti source code, and makes use of a 3rd-party Windows search engine called “Everything” in order to search for valuable files to encrypt.

Sneaky PlugX variant spreads via USB
Palo Alto’s Unit42 has uncovered a novel PlugX variant capable of spreading via infected USB drives, and hiding its malicious contents from inspection with the use of a Unicode whitespace character.
The find came as the team were responding to a Black Basta ransomware infection, where they also discovered GootLoader malware and the Brute Ratel C4 red-team framework - though these aren’t believed to be related to the PlugX sample found in their investigations.
Side-loading still in use
The actor distributing the PlugX sample used the 32-bit version of the legitimate x64dbg debugging application in their attack. Executing it on the victim will result in the side-loading of an attacker-supplied, malicious module called x32bridge.dll.
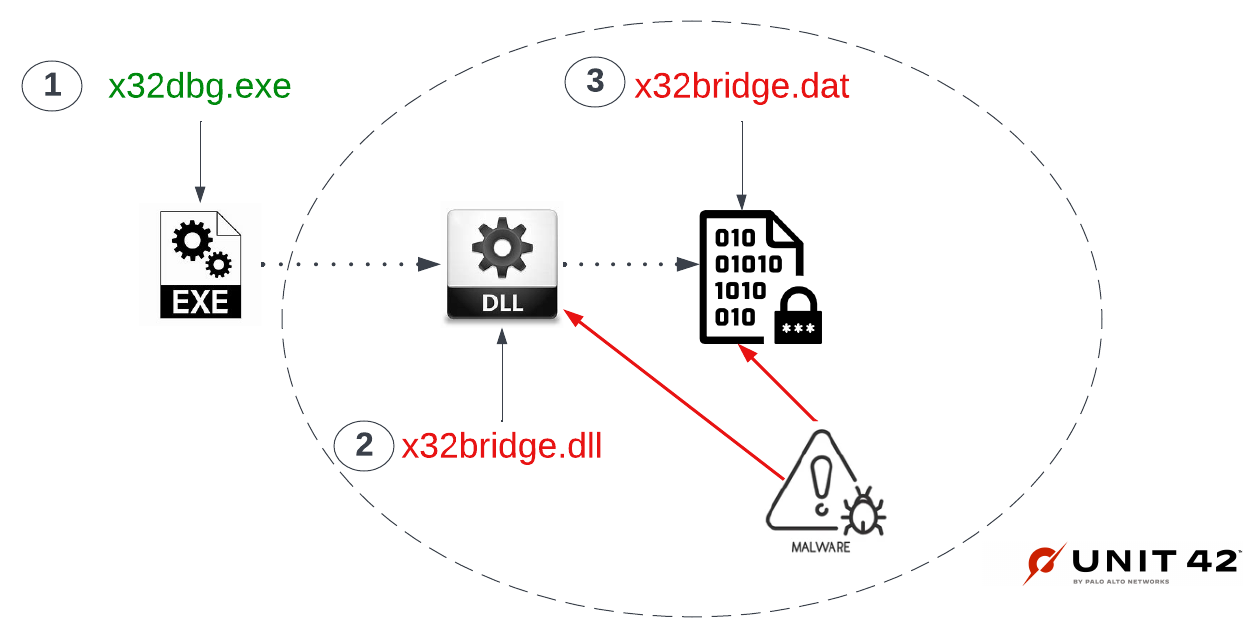
The technique, and even the use of x64dbg, is nothing new for PlugX infections, with Sophos researchers having flagged it back in 2020.
Infections via USB
A target who inserts an infected USB drive into their system will only see this:
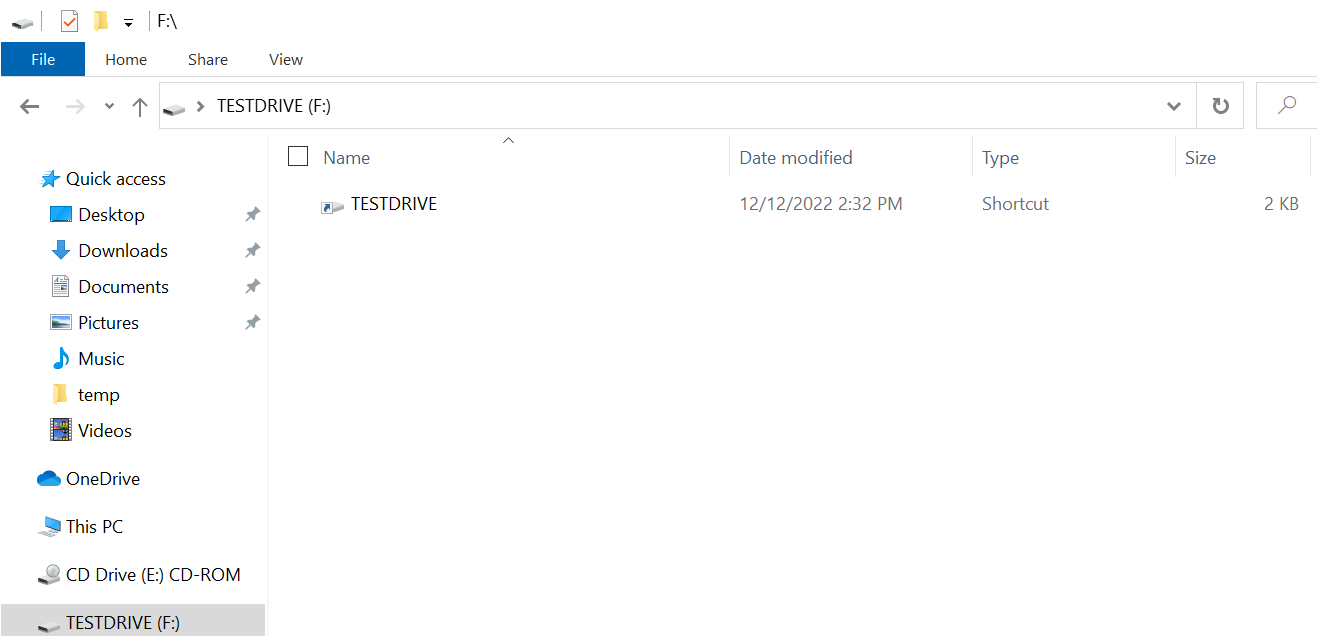
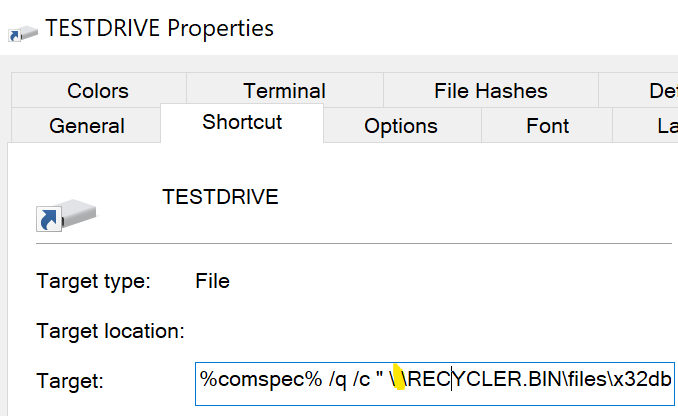
The above is a crafted .lnk file, which is configured to execute x32dbg.exe and kick off the infection chain:
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber.
The files being referenced are hidden using the Unicode “no-break space” character, which is 0x00A0 in hex code.
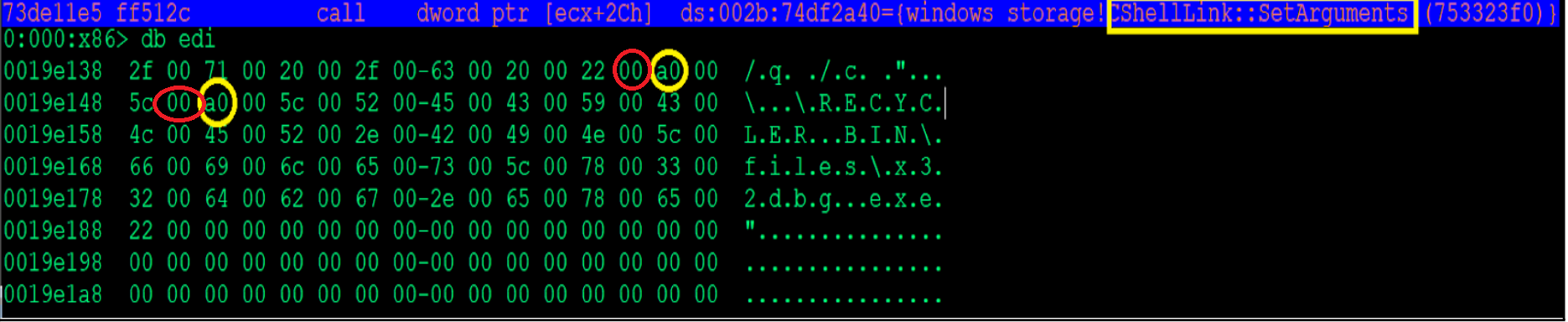
These can’t be rendered in Windows Explorer or cmd.exe, allowing the attacker to hide their payload files while only presenting the malicious .lnk file at the root directory of the infected USB.
Propagating infections
As part of the infection chain that kicks off once x32db.exe is run - x32bridge.dat is loaded, which is a separate file responsible for infecting any connected removable media; creating the hidden directories and copying the malicious files over.
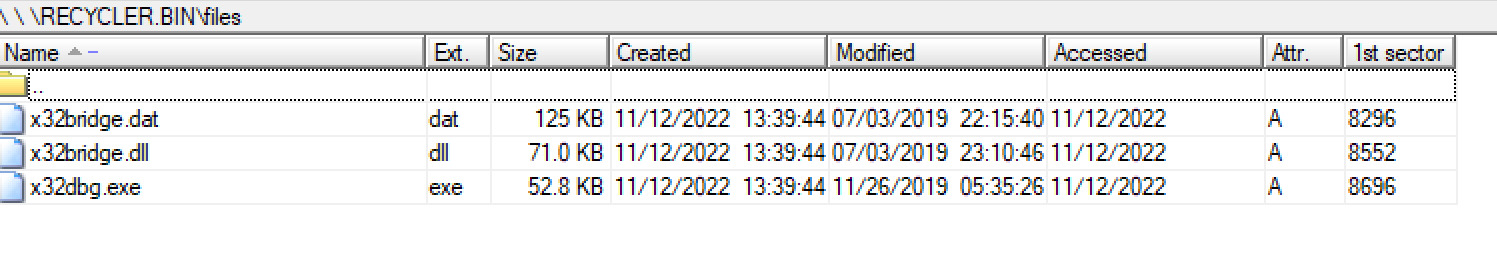
PlugX Development Ongoing
Unit42 also flagged additional, related variants of the PlugX malware - one which appeared configured to also identify and delete old versions of PlugX installed, and another capable of copying all Adobe PDF and Microsoft Word documents from the infected host to the USB device's hidden folder created by the PlugX malware.
These findings indicate that the age-old malware is not only still being deployed in the wild, but that it’s continuing to be developed to meet the needs of its operators.
Furthermore, the addition of USB-spreading functionality is a worrying addition that provides the malware worm-like abilities, putting it in the same class as the Raspberry Robin malware which has spread significantly since its discover last year and been used to enable the delivery of second-stage malware and conduct of pre-ransomware activities.

Other Vulnerabilities
2021 flaw in Realtek SDK exploited en masse to grow botnets
Palo Alto’s Unit42 have reported 134 million attempts to exploit CVE-2021-35394 between August 2021 to December 2022 - though 97% of this volume occurred post-August last year.
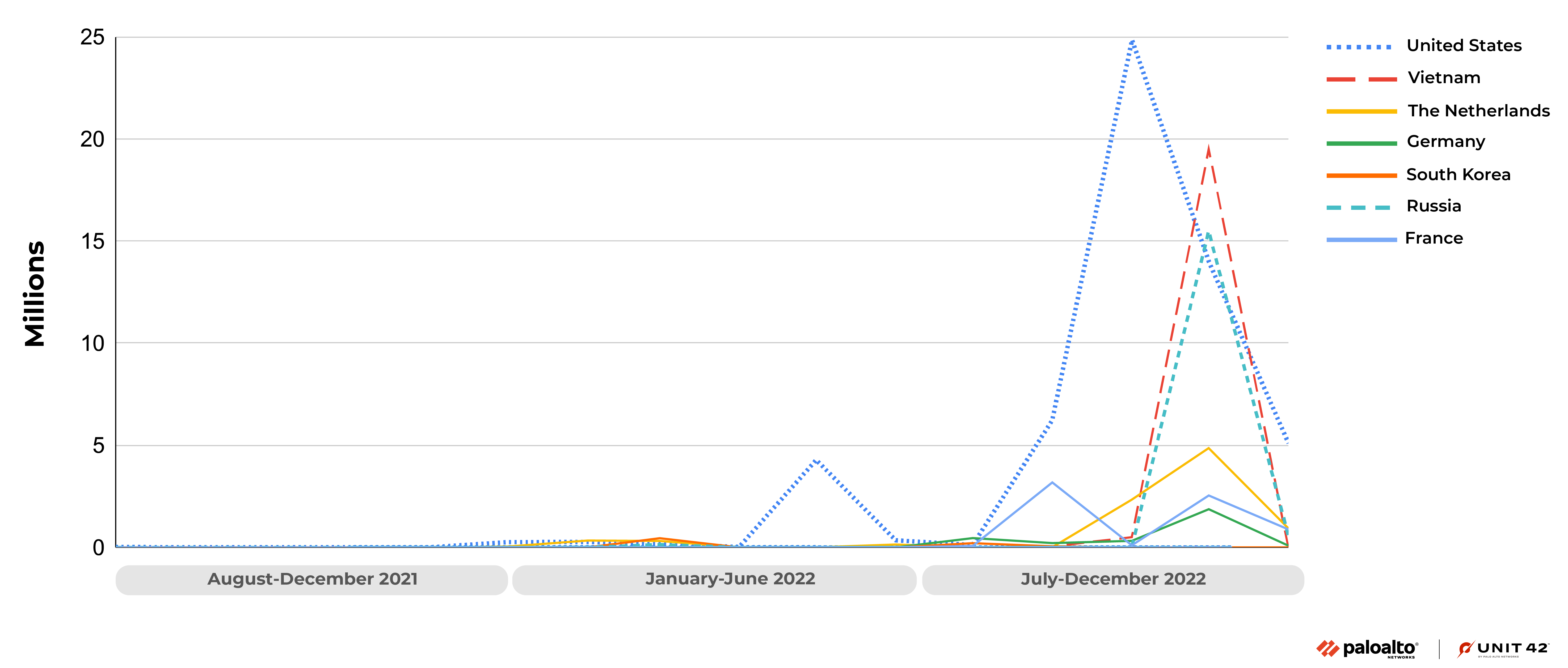
The majority of these attacks are conducted by Mirai, Gafgyt and Mozi botnets - or variants thereof.
The report also highlights that 95% of attacks originating from Russia - which accounted for 14.6% of the total attack volume (~19.564 million attempts) were directed at organisations in Australia.
Given that CVE-2021-35394 affects almost 190 models of devices from 66 different manufacturers, the patching of which is almost entirely dependent on individual users - exploitation of this vulnerability is likely to continue, and will see the attacking botnets further build their numbers.
Patches for four bugs in VMWare’s vRealise Log Insight product
Patches - and scripts to implement workarounds for those who can’t patch - have been released for four vulnerabilities found in VMWare’s log management & analysis product:
- CVE-2022-31706 (CVSS 9.8) - RCE via directory traversal;
- CVE-2022-31704 (CVSS 9.8) - RCE via file injection;
- CVE-2022-31710 (CVSS 7.5) - DoS bug;
- CVE-2022-31711 (CVSS 5.3) - Unauthenticated data leak;
The bugs impact all versions of vRealise Log Insight prior to 8.10.2. Make sure you’re patched against this, as security research company Horizon3 has flagged an imminent release of a PoC exploit that will likely enable in-the-wild exploitation of this vulnerability.
Exploitation of multiple vulnerabilities affecting #VMware vRealize Log Insight leads to unauth RCE
— Horizon3 Attack Team (@Horizon3Attack) 7:44 PM ∙ Jan 26, 2023
🔺 CVE-2022-31704, CVE-2022-31706, CVE-2022-31711
🔺 IOC Blog tomorrow
🔺 POC / Deep-Dive Blog next week
See VMware Security Advisory: vmware.com/security/advis…
Apple WebKit RCE patches backported for older mobile devices
Apple has back-ported patches for an actively exploited WebKit vulnerability (CVE-2022-42856) to older iPhones and iPads.
The CVSS 8.8 RCE vulnerability can be exploited by simply redirecting victims to a maliciously crafted website, and was added to the CISA KEV in December last year for mandatory patching by US Federal Civilian agencies.

Offensive
- ADModule - A Microsoft-signed ActiveDirectory PowerShell module. You can copy this DLL to your machine and use it to enumerate Active Directory without installing RSAT and without having administrative privileges;
- Inline-Execute-PE - load unmanaged Windows executables (e.g. Mimikatz, Dsquery) into Cobalt Strike Beacon memory and execute them without touching disk, retrieving the output and rendering it in the Beacon console.
- Gato - The Github Attack Toolkit that can help search for and enumerate public repos using self-hosted Github runners;
- Cloudtopolis - Crack hashes using free, graphics-card-equipped VMs in Google Cloud;
- Quick Network Scanner - As per the name - a quick network scanner, built on Rust;
- Getting bored of Cobalt Strike on every engagement? Take a look at Meterpreter’s BOFLoader to see if it’s worth adding to your arsenal;
- Nestori Syynimaa has shared a walkthrough for a potential PrivEsc from Local Admin to a Group Managed Service Account;
- @nas_bench points out a simple persistence opportunity using VSCode Terminal Profiles.
Defensive
- LogSlash - a framework that summarises Log data in transit to your SIEM to reduce ingest volume. While it might prove useful to organisations short on cash, keep in mind that some fields are lost or compressed (e.g. timestamps for related events are culled to a simple first and last seen value) which may impact their utility in an investigation;
- Kali-Purple - a SOC-in-a-box project that aims to help with all use cases Blue, Purple, and Red Team;
- The DFIR Report have shared a report looking at Invoke-ShareFinder - a tool used in 40% of their reported cases to enumerate network shares as they look to move laterally and pilfer information of value;
- This repo is called “Awesome-BEC”, but contains links to resources that would be useful for anyone looking to upskill in cloud-based investigations in Azure or GCP;
- The next time you’re faced with Bat-Crypter encrypted payloads, e.g. for ASyncRAT samples - give this tool a crack to decrypt it;
- While we’re on the topic of decryptors - here’s one for IcedID payloads;
- Bookmark this repo for tools useful in analysis of LODEINFO malware and C2 comms;
- Didier Stevens has shared his approach to analysing OneNote maldocs;
- Check out this write-up of some analysis of a BATLoader payload that went on to drop Ursnif and the Redline infostealer on target;
- Elad Shamir of SpecterOps looks at Read-Only Domain Controllers - typically deployed in less secure environments to provide DC functionality, but not treated as a Tier 0 asset like their full-featured counterparts. Should they be? Spoilers - yes.

- An international ransomware-fighting group comprised of 37 members has officially begun operations, with Australia as the first chair. The group will focus on information sharing, best practice policy and legal authority frameworks, and collaboration between law enforcement and cyber authorities;
- Microsoft is aiming to mitigate abuse of malicious XLL add-ins, by blocking execution of such files downloaded from the internet. The change will be rolled out to Office 365 customers in March this year;
- Infosec veteran Lina Lau has created her own training course that looks at attacking & defending Azure & Office 365. As a highly skilled investigator herself, who’s put out plenty of invaluable content for free - this course is bound to be a banger;
- LastPass’ parent company GoTo has shared a limited advisory, notifying customers that the breach of their developer networks in November last year has resulted in the additional theft of encrypted backups containing customer information and an encryption key for a portion of that data;
- Google have celebrated taking down over 50,000 instances of activity that comprise a broader Pro-Chinese Influence Operation, first uncovered by Mandiant in July last year called DRAGONBRIDGE;
- If you haven’t had your fill of attacker trend reports yet - here’s one from Cisco and another from Blackberry, both looking at the 2022 Q4 period;
- SentinelOne are a little late to the party with their wrap-up of 2022, but have some noteworthy findings including the splintering of ransomware groups and increasing use of drivers to disable EDR.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber.





