SOC Goulash: Weekend Wrap-Up
16/01/2023 - 22/01/2023

Bypassing user training & enterprise protections with malicious Ads & SEO-Poisoning
Threat actors are capitalising on legitimate search engine features such as paid advertisements and Search Engine Optimisation (SEO) to deliver malware direct to the unwitting user.
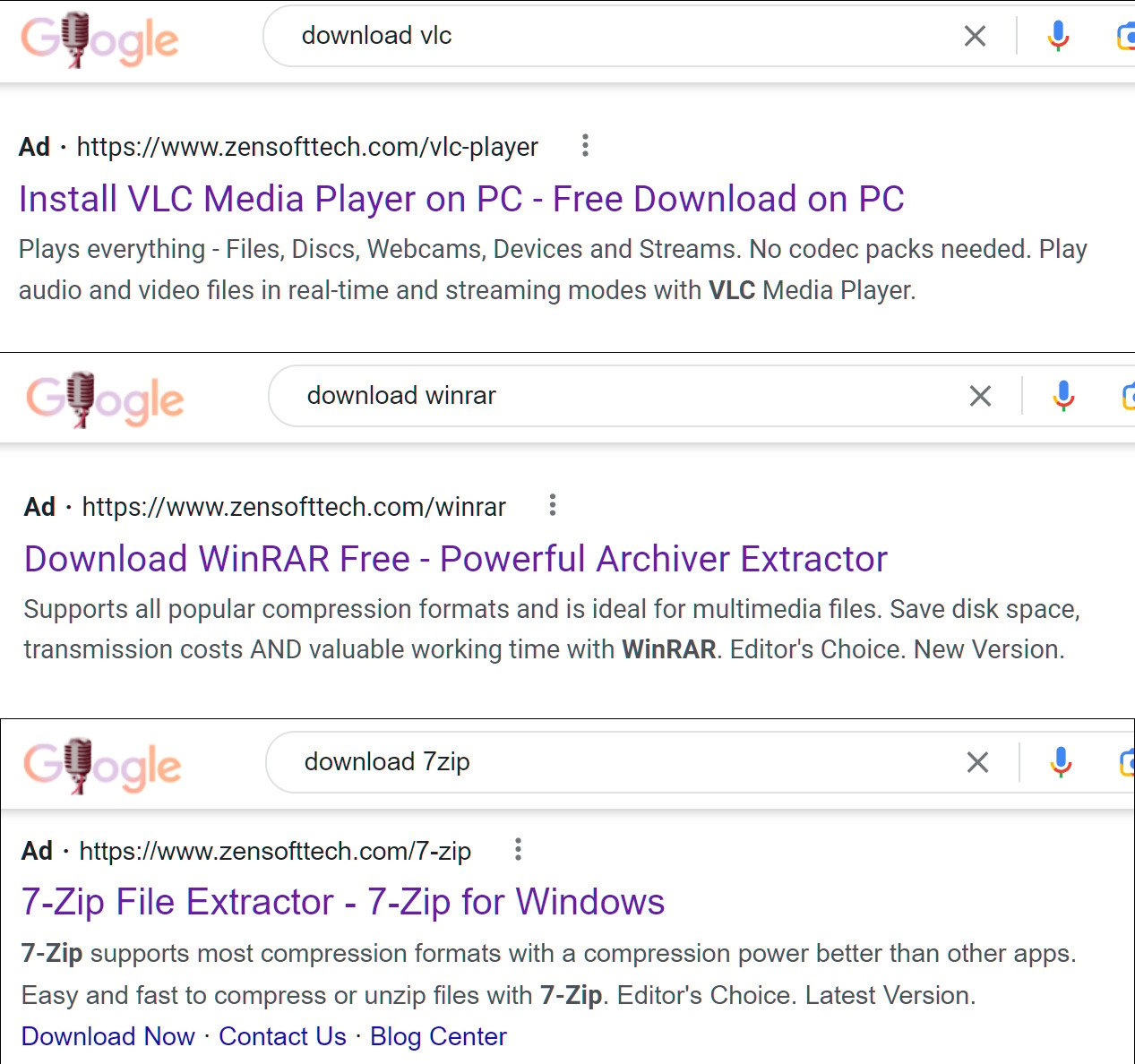
The first method is through the malicious use of Google Ads, a.k.a. “Malvertising”. By running a Google Ads campaign purporting to offer downloads for popular software such as VLC Media Player or 7-zip, actors are able to get links to their sites hosting malicious executables bumped to the top of the Google search results - right where the average user (or sysadmin in a rush) would expect the legitimate site would be.
SEO-Poisoning is the other method that’s recently risen in prominence, where attackers abuse SEO scoring to boost their malicious site in the search results ranking, making them more likely to be clicked on by users looking to download a particular program.
Clicking through the link will land the user on a cloned copy of the legitimate site, offering a fake, malicious executable for download that pretends to be the software they’re after.
Attackers have gotten crafty with this, adding multiple redirects and/or checks to ensure you’ve bounced through from a Google Ad click through before serving up the malware, in order to mitigate automated scanners and investigation by security researchers.
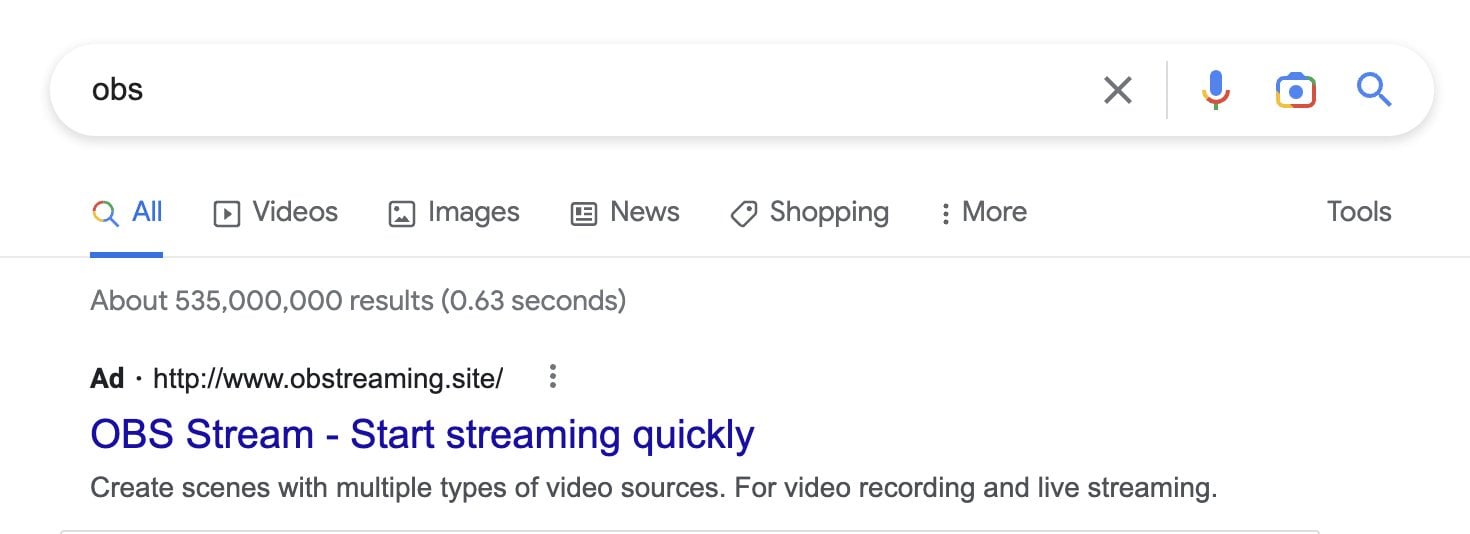
These campaigns have already proven to be successful, with a “crypto-influencer” (🤮) going by the name NFT God (🤮🤮) reporting he lost control of all his crypto assets and social media channels after clicking through a Google Ad link and installing a fake executable that purported to be the popular streaming software OBS (Open Broadcaster Software).
A large range of malware families have been observed being spread via Malvertising and SEO-Poisoning, including InfoStealers such as Raccoon, Vidar, Rhadamanthys, Aurora and RedLine; and IcedID, a wide-spread and highly capable 1st-stage malware which has been leveraged in the past to enable ransomware attacks.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber!
Impact
Payloads delivered via these methods have the added benefit of bypassing Email protections - an area which organisations have focused heavily on in recent years both in terms of improving the filtering and sandbox technologies, as well as end-user awareness of Phishing attacks.
This technique abuses a different attack surface which users are much less cautious of, which explains the high success rate the attack method.
It’s worth noting that even once malicious Ads are removed, the cloned site hosting the attackers malware will remain active without further intervention. These sites will continue serving malware to anyone unfortunate enough to stumble upon it, and can be integrated with Phishing campaigns for continued utility even once the Ad is taken down.
Defence
Ad blockers are your best defence against Malvertising, as they will prevent them from even appearing to the user in the first place.
It would be worth baking this into your enterprise SOE to ensure all workstations are built with one enabled, and enforcing it in policy via your Mobile Device Management (MDM) Platform - if you have one - to prevent BYOVD devices from being susceptible to this attack.
Both Malvertising and SEO-Poisoning can be mitigated by ensuring you’ve got some high-quality threat feeds plumbed into your SIEM alerting process, as well as by blocking - or at least monitoring for - attempted installations of binaries from obvious locations like the user’s Downloads folder.

LockBit primed for disruption
LockBit is the most active and arguably most notorious ransomware operation today; lead by an individual known as LockBitSupp, they’ve racked up affiliates almost as fast as they have victims.
This ambition, however, seems to have gotten the better of them, with LockBitSupp apparently unable to prevent an affiliate from violating their rules of engagement by attacking and ransoming the Hospital for Sick Children in Canada, and seemingly unaware of an affiliate compromising the UK’s Royal Mail less than two weeks later.
These missteps are indicative of a ransomware enterprise that grew too fast, with too few safeguards on the quality and conduct of recruits, and the authority seemingly centered in one person with limited reach.
The view from the inside
Jon DiMaggio of the Threat Intel outfit Analyst1 adds to this picture with a detailed account of several months worth of interactions he had with the LockBit group while undercover with the gang, highlighting the toxic nature of LockBitSupp’s leadership and the rivalry he cultivated with other ransomware gangs.
DiMaggio further claims that the developer of LockBit 3.0, or LockBit “Black”, has left the group after a falling out with LockBitSupp - leaving the LockBit 3.0 ransomware without any support for almost one year. The developer alleges that LockBitSupp repeatedly made false promises in how the ransomware would be used and how much compensation he would receive for his work, and stole $50k from him to pay for a “bug bounty”.
LockBit’s aggressive growth has also been fueled by their leadership’s showboating on dark web forums and public comments insulting the competence of rival operations. DiMaggio also notes LockBitSupp “uses the ‘smear campaign’ tactic often against any ransomware gang they feel threatens its dominance in the criminal community”. While these tactics may have helped grow the group’s “brand”, it’s also served to alienate them from other cyber criminal and ransomware actors.
Ripe for the picking
With LockBit appearing to have burned bridges with both the developer of their 2.0 and 3.0 variants, it’s likely that any deficiencies found in its encryptor will prove difficult for the group to remediate.
Furthermore, the toxic leadership of LockBitSupp has been plain for all to see, and will make it difficult for the group to recruit reputable developers or technical resources going forwards. As we’ve seen in the past, even cyber criminals will be hesitant to work with operators who have been shown to act in bad faith - now that DiMaggio’s exposé is public, we may start to see the value of the LockBit brand deteriorate amongst their peers.
As the most prolific ransomware group in operation right now, their current lack of technical resources and poor reputation within the cyber criminal ecosystem puts them in a weak position which researchers and law enforcement could - and should - capitalise on.
Found this useful? Why not share it!
Other Reporting
- Check Point’s December Malware rankings are out - Qakbot overtakes Emotet to be the most widespread, being seen on 7% of networks monitored worldwide compared to Emotet’s 4%. The blockhain-enabled Glupteba botnet has also popped into the top 10 for the first time since July 2022;
- Group-IB have produced a mammoth 206 page report looking at trends in the cyber crime ecosystem for 2022. The most notable category of trends was in Initial Access Brokers, which saw more IABs selling more corporate accesses, and for cheaper than ever;
- Sekoia’s analysis of the top trends in attacker C2 infrastructure is one to add to your reading list, with great insights into the use of Open Source Tooling and certain hosting providers by threat actors;
- Rhadamanthys is a new infostealer doing the rounds via SEO-poisoned Google Ads, first seen in late 2022. Check out this recent wrap-up thread with handy reference articles, as well as this detailed analysis by Eli Salem to see what makes it tick;
- Team Cymru have shared a very detailed and insightful post that looks at the infrastructure backing the Vidar infostealer;
- Kostas Tsale has shared a great thread summarising IcedID TTPs, to help you better understand their attack chain and how to detect it;
- Minerva Labs have picked up a new strand of Remcos RAT that has swapped function calls for direct syscalls in an attempt to evade detection based on common API calls like NtWriteVirtualMemory;
- China’s APT15 (Playful Taurus) have been spotted hitting the Iranian government in the latter half of last year, allowing Unit42 to publish this detailed report on their infrastructure, capabilities, and tradecraft;
- A new malware strain called xdr33 has been seen deployed as first-stage malware in-the-wild. Notably, it looks to have been built on the Hive malware suite, originally built by the CIA and leaked publicly by WikiLeaks in 2017.

PoC, exploitation for critical Zoho Manage Engine vulnerability
Late last week, researchers from Horizon3 released a proof-of-concept (PoC) exploit and technical analysis for a critical pre-authentication RCE vulnerability (CVE-2022-47966) in Zoho Manage Engine products.
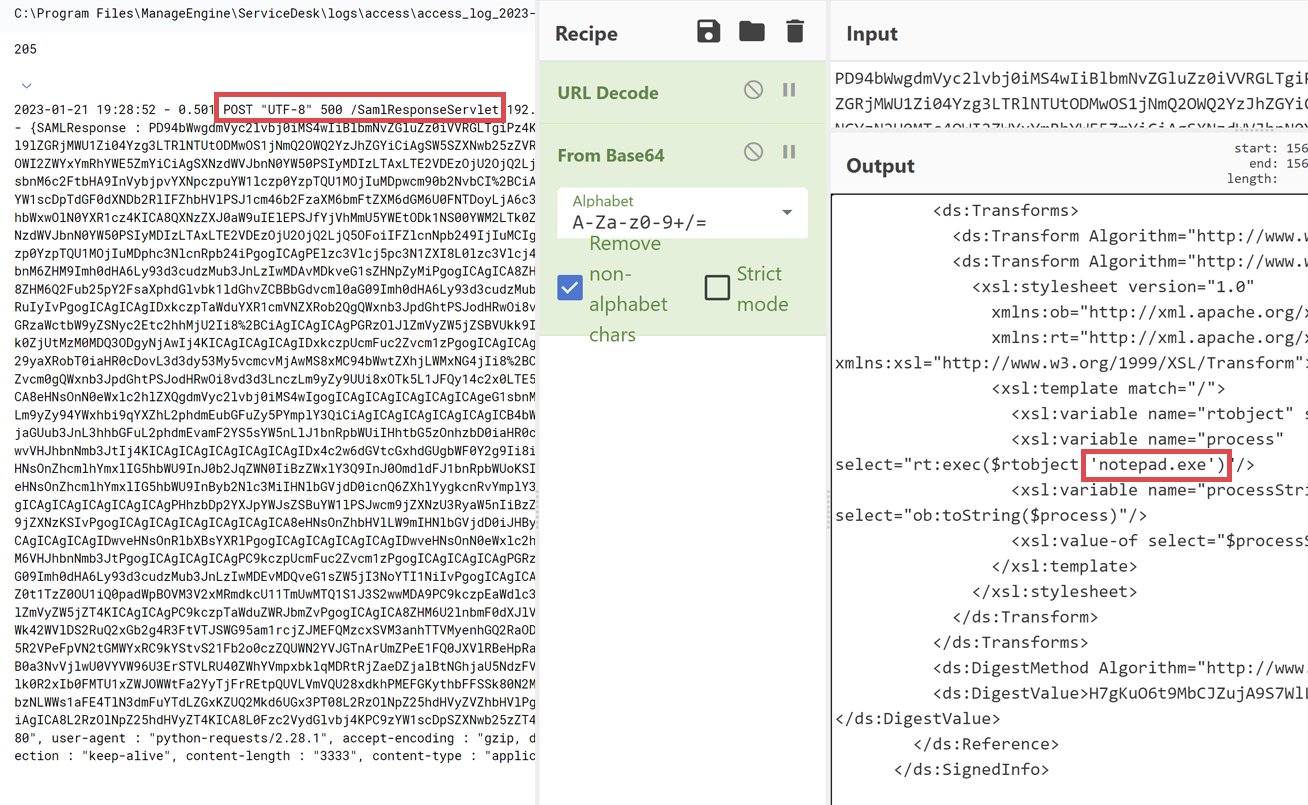
The vulnerability can be trivially exploited through issuing a crafted HTTP POST request with a malicious SAML response, with the researchers themselves noting last week that it was a “good candidate for attackers to 'spray and pray' across the Internet”, and that it provides full control of the endpoint by achieving RCE as NT AUTHORITY\SYSTEM.
While patches were released in October last year, it seems many organisations have not yet implemented them. Rapid7 have reported observing exploitation as early as January 17 - two days before the Horizon3 PoC was released - with post-exploitation activities including disabling of Defender and delivery of secondary tooling being observed.
Patch, Detect, and Hunt
If you’re one of the organisations unlucky enough to have not patched this vulnerability by now - this should be done urgently, and supplemented with performing a Hunt for exploitation and post-exploitation activity.
This Sigma rule may help, which looks for anomalous spawned processes indicative of exploitation. Note as well that the Base64-decoded payload of the POST request can indicate what the attacker payload was, which can be used to inform your internal hunts.
Other Vulnerabilities
Cacti Device Monitoring software under active exploitation
A CVSS 9.8 command injection vulnerability (CVE-2022-46169) in the Cacti device monitoring software is being actively exploited to deliver reverse shells and recruit devices into botnets such as Mirai.
The publication of a technical write-up in early January appears to have triggered the exploitation of the vulnerability by cyber criminals, with at least 1,637 unpatched instances found exposed to the internet by Censys.
Mandiant find Chinese-affiliate actor exploiting FortiOS vulnerability
Mandiant have shared a report that builds on last week’s newsletter which saw Fortinet warn of an unknown, sophisticated actor exploiting the recent 0-day vulnerability (CVE-2022-42475) in FortiOS VPN appliances.
Mandiant assess with low confidence that a China-affiliated actor is responsible for abusing this vulnerability to deploy a new backdoor they’ve dubbed BOLDMOVE on unpatched appliances.
The attribution is largely based on time-of-activity, as well as the targets chosen by the actor. Chinese threat actors also have a well-documented penchant for popping unpatched internet-facing network appliances and remote access gateways.
Over 4,000 Sophos Firewall devices vulnerable to RCE attacks
Something we missed from last week - Vulncheck researcher Jacob Baines has found that 99% of Sophos Firewalls scanned haven’t upgraded to a version with the official patch for an unauthenticated RCE vulnerability from September last year (CVE-2022-3236.)
Instead, 93% of internet-facing devices that were identified were running versions that are eligible for - and should have automatically downloaded - the hotfix for the vulnerability.
This leaves over 4,000 firewalls completely vulnerable to the exploit, and many thousands more which are relying on the hotfix being bulletproof.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber!
Aruba’s Virtual Intranet Access allows DLL Side-Loading to SYSTEM
Notorious security researcher Will Dormann has publicly shared details of a flaw in Aruba’s Virtual Intranet Access software, after being fobbed off by both HackerOne and BugCrowd who said they don’t consider it a vulnerability (debatable).
The bottom line is that the software doesn't enforce ACL's when installed to a directory off of C:\ - this results in it being possible for an attacker to drop a malicious DLL with the same name as a missing one that the agent attempts to load (i.e. DLL Side-loading) to gain execution as SYSTEM.
I mean, call it what you want - that’s something an attacker would happily take advantage of. Let’s hope Aruba are watching Will’s thread and roll out a patch, regardless.
P.S. The tool used in the demo is called Crassus - we pinged it in last week’s newsletter, and it’s definitely worth checking out!
Git patches two critical vulnerabilities
Git has issued patches for two vulnerabilities that could allow for arbitrary code execution (CVE-2022-41903 in the commit formatting mechanism and CVE-2022-23521 in the .gitattributes parser).
These vulnerabilities can be triggered through the performing of common actions - namely the Git clone, pull, and archive operations - which makes this one worth patching sooner rather than later.
Undocumented AWS API bypasses CloudTrail logs
DataDog have shared their findings of a now-patched vulnerability in AWS’ CloudTrail logging, which would have allowed “an adversary to perform reconnaissance activities in the IAM service after gaining a foothold in an AWS account—without leaving any trace of their actions in CloudTrail.”
They also noted “this technique also makes it possible to bypass GuardDuty for findings such as IAMUser/AnomalousBehavior, because GuardDuty uses CloudTrail as a data source.”
Azure bugs squashed
First up - a series of four SSRF vulnerabilities found by researchers at Orca have been remediated. The bugs impact a number of Azure products, specifically:
- Azure API Management;
- Azure Functions;
- Azure Machine Learning, and
- Azure Digital Twins
The impact of the bugs range from enabling limited reconnaissance to leaking data from arbitrary endpoints, and received severity ratings ranging from Low to Important.
Separately, cloud security firm Ermetic have reported on a new RCE vulnerability they’ve dubbed EmojiDeploy, which stems from the Kudu back-end to the Azure App Service.
The vulnerability - which doesn’t appear to have been issued a CVE number - is a Cross-Site Request Forgery vulnerability that would allow an attacker to “deploy malicious ZIP files containing a payload to the victim’s Azure application.”

Offensive
LinWinPwn - a bash script that automates a number of Active Directory Enumeration and Vulnerability checks performed by tools such as impacket, bloodhound, crackmapexec, kerbrute, and more;
Mangle - a tool to help you dodge signaturing and scanners by manipulating payload attributes and strings;
DumpThatLSASS - an (allegedly) “fully undetectable” credential dumper;
Open Source Surveillance - an OSINT framework that specialises in assisting in geo-based OSINT projects;
I found this a pretty cool write-up for a Bug Bounty submission that found a flaw in Google’s Cloud Compute Engine, allowing injection of SSH keys to victim environments by simply sending a crafted malicious link.
Found this useful? Why not share it!
Defensive
- HardeningKitty - a script to assist in auditing the security configuration of Windows system in accordance with guidelines such as CIS, DoD’s STIG, and Microsoft baselines;
- DumpBTM - a tool that helps programmatically parse the proprietary BackgroundItems-v4.btm file on MacOS, which contains records of all persistently installed items;
- Researchers at Trend Micro have demonstrated the potential for abuse of Github Codespaces, which could be serve as another trusted site to deliver secondary payloads;
- Wiz.io has shared a very handy guide with queries to run and artefacts to look for in AWS, Azure and GCP, which could help surface attempts by actors to persist in your cloud environment;
- This post by Microsoft is a great resource for investigations, providing guidance for how to hunt for malicious activity in Microsoft’s Unified Audit Log;
- SpecterOps continue to pump out great content, this time a detailed look at Windows Services - how they work, are abused, and how to detect it;
- Cisco Talos has shared a comprehensive analysis of the use of .lnk files by a range of threat groups, including details of how to cluster related activity using file metadata and how .lnk files vary based on the tools used to generate them;
- PwnDefend has published two posts, one looking at hunting for Malicious Scheduled Tasks, and for Scheduled Tasks enabled via Group Policy;
- Using PowerShell v7? Make sure you’ve accounted for the change in logging locations when performing IR or interactive log retrieval;
- @nas_bench has also highlighted EID 201 in the Microsoft-Windows-AppModel-Runtime/Admin logs which can help identify execution events for AppX applications;
- For anyone investigating a WSL-enabled Windows machine - ext4.vhdx file is a useful log source, e.g. for bash history of the Linux subsystem;
- The Windows Program Compatibility Assistant has been observed creating new artefacts as of the 22H2 version of Windows 11 Pro. PcaAppLaunchDic.txt appears to be the primary artefact of use, providing another reliable source of evidence of execution, similar to Prefetch and Amcache;
- Check out this post on identifying PsExec, something every Defender will have encountered at some point and should get familiar with recognising;
- Take the pain out of running Plaso/Log2Timeline by setting these aliases;
- One for my fellow Threat Intel nerds - Navigating the Trade-Offs of Cyber Attribution, by Mandiant.

- Chalk one up for the good guys - Avast has released a decryptor for a strand of BianLian ransomware they’ve seen in-the-wild;
- TrustedSec have shared an interesting post which wraps up the key trends from conferences held throughout 2022 - a handy way to get a feel for where the industry might head as we make our way through the new year;
- Another milestone has been reached in the evolution of ChatGPT - researchers at CyberArk figured out a clever way to circumvent guardrails put on user interactions with ChatGPT, successfully building a polymorphic malware based on the AI bot’s answers;
- MailChimp have suffered their third breach in 12 months, with an employee falling for a social engineering attack that enabled the subsequent theft of data for 133 customers;
- Not to be outdone, T-Mobile have succumbed to their eighth breach in under 5 years, with an insecure API enabling the theft of personal data for 37 million customers;
- Datadog have notified customers that they were impacted by the breach of CircleCI, with an RPM GPG signing key and passphrase being stolen. This means that while attackers could sign an RPM package with the stolen key to make it look legitimate, customers have been notified it should no longer be trusted, and the attackers wouldn’t be able to insert the malicious package into the supply chain without additional access to the Datadog repos;
- Credential Stuffing might be a low-skill attack, but it still works - 35,000 PayPal users can attest to that.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber!





