SOC Goulash: Weekend Wrap-Up
31/10/2022 - 06/11/2022
This is an extended newsletter, so it may be truncated towards the end of the email. To read the full post, just select the View entire message hyperlink at the bottom of the email or Open in Browser!

Welcome to the Emotet + IcedID Reunion tour
Emotet has returned from a four-month hiatus, unleashing a barrage of malspam that delivered the Emotet payload via malicious Excel attachments.
The maldocs attempt to convince users to help it bypass Protected View with a bit of social engineering, advising that their security policy requires them to move the file to a trusted location in order to run.
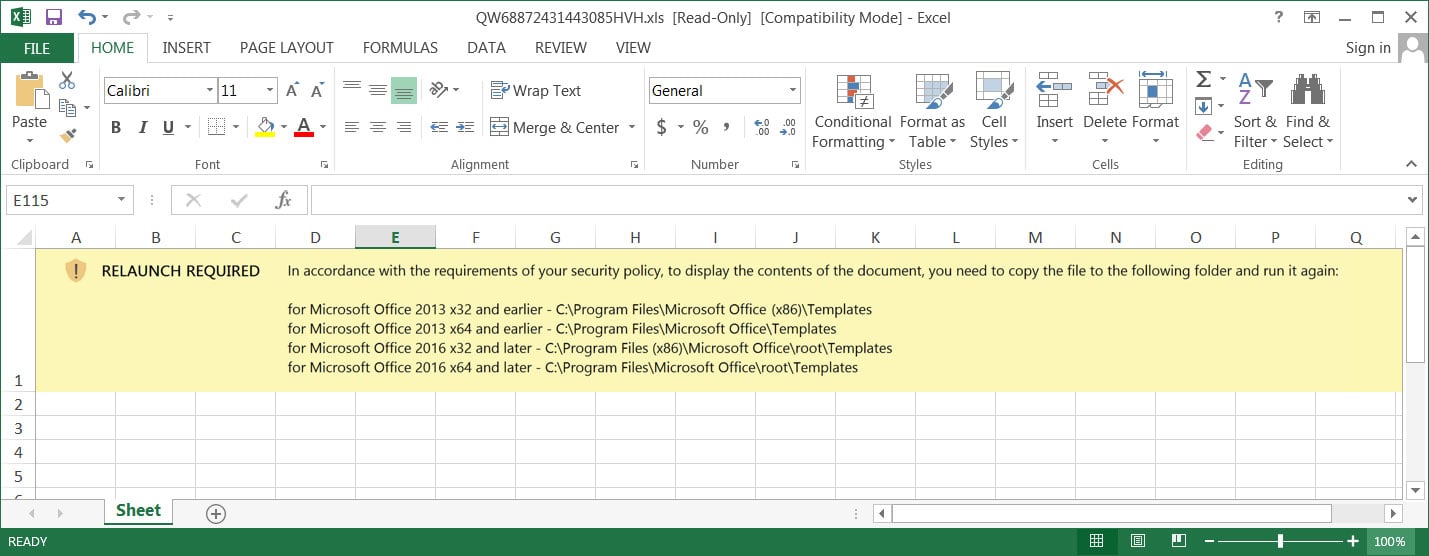
Similar to the use of iso files in payload delivery chains, the intent here is to bypass the MotW-enabled protection so the malicious macro runs as the file is opened.
Consistent with its reputation for enabling delivery of secondary malware families, Unit42 have also reported observing Emotet delivering IcedID as a secondary payload.
Note that Emotet establishes persistence through a registry Run key, while IcedID uses a Scheduled task - both use world-writeable locations such as %USERPROFILE%\AppData\Local and %APPDATA% to store their persistence binaries.
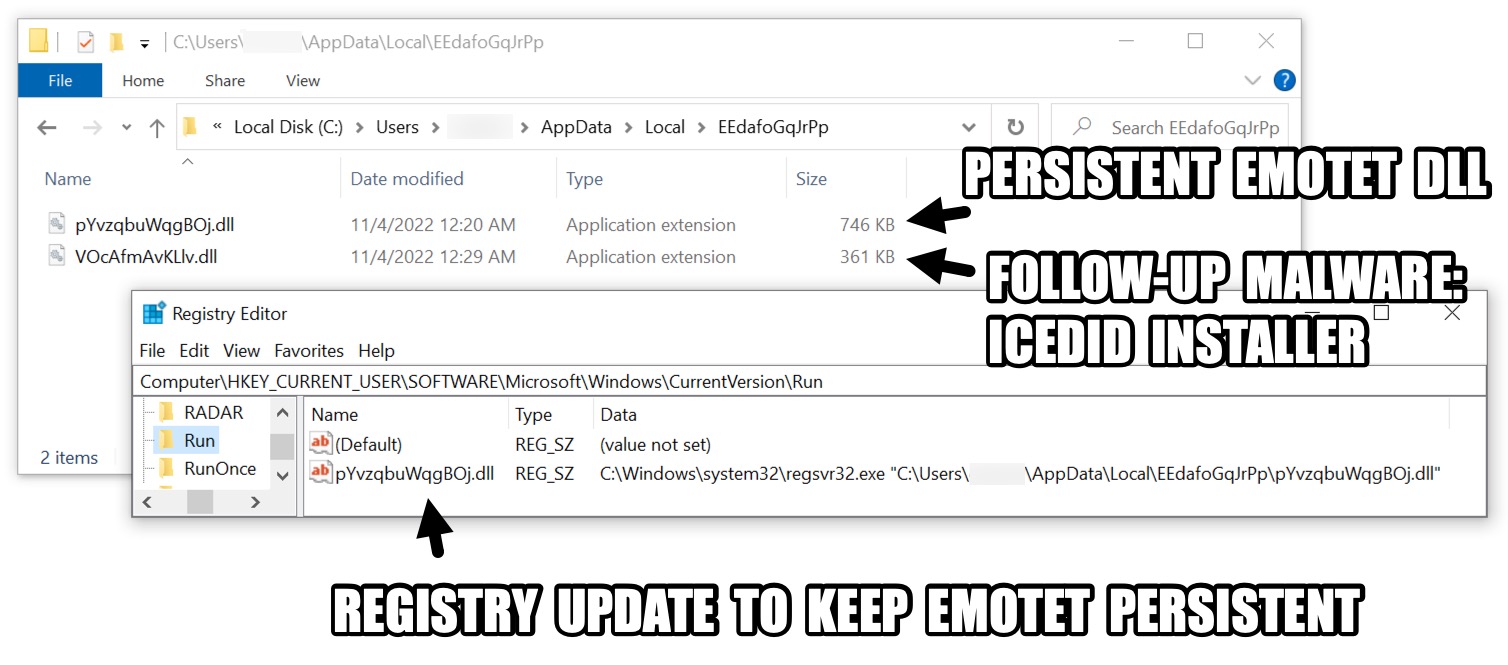
Proofpoint have also highlighted that the IcedID samples being dropped by Emotet’s Epoch 4 botnet (where they usually test new techniques later ported into the Epoch 5 botnet) appear to be development builds.
Emotet have long been considered a top threat in its class, but now shares that ranking with Qakbot, IcedID, and - debatably - Ursnif. Defenders will have to keep on top of all four, as they’re all prolific in distribution and can enable delivery of secondary malware families; post-exploitation frameworks such as Cobalt Strike, and onwards infection by ransomware actors.
Australia continues to be a target of low-sophistication cyber crime
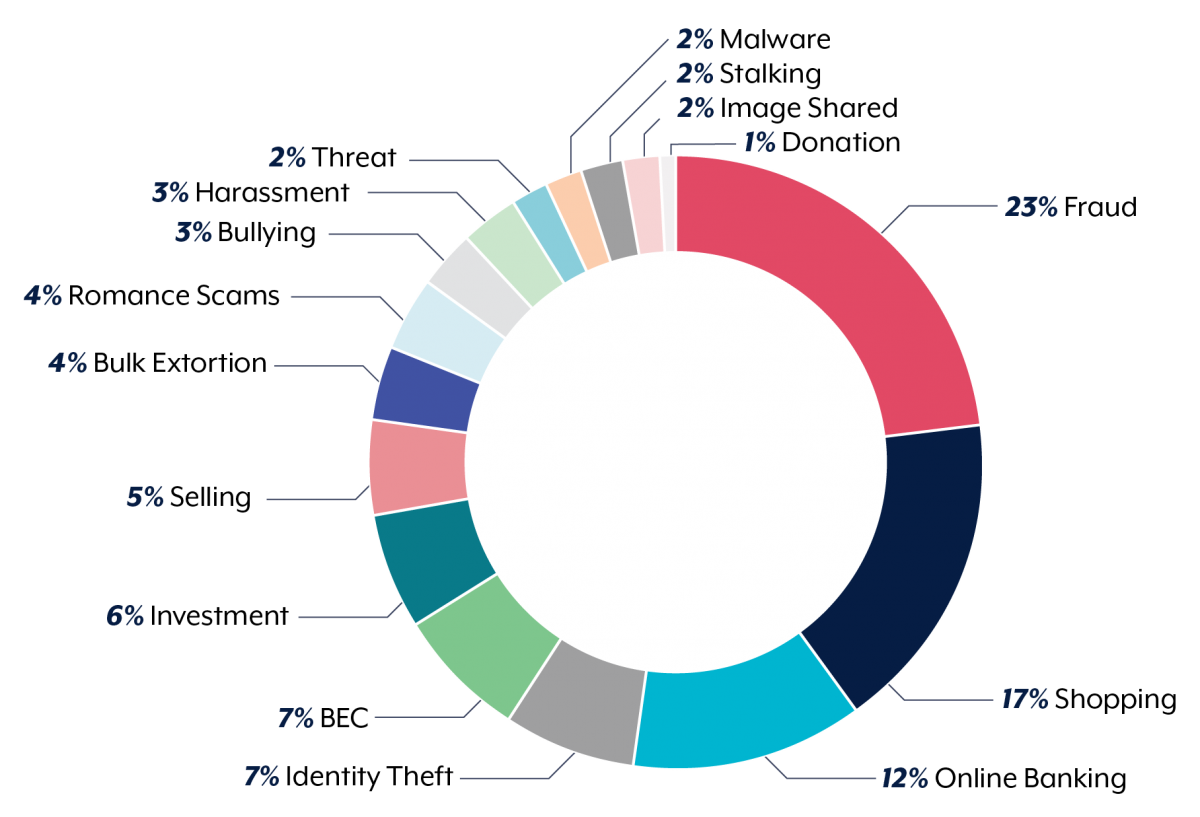
The Australian Cyber Security Center (ACSC) has released their latest annual report, highlighting an overall increase in the cost of attacks across the board, and more reports or requests for assistance over the financial year.
Cyber-espionage still a priority for Australia-focused groups
Commonwealth Government agencies were largely over-represented in the rankings of the top 10 impacted sectors, accounting for 24% of all incidents responded to. The 2nd highest sector, which was a combination of State, Territory and Local governments, only accounted for 10%.
With the combined tiers of government agencies accounting for over 1/3 of incidents responded to, it’s worth considering whether this could be attributed to the increased oversight and priority monitoring by the ACSC of their infrastructure, or a greater focus by malicious actors in targeting our government agencies instead of private industry.
When considering the latter, it’s more consistent with what we’ve seen in recent years - network breaches are primarily seen in Government entities, whereas low-skilled cyber crime actors will target individuals and small businesses with BEC, scams, and infostealers.
What happened to ransomware?
Interestingly, the ACSC actually experienced a 15% decrease in ransomware incidents responded to (135) compared to last year (160), which accounted for a little over 12% of the more than 1,100 incidents they responded to during the reporting period.
It remains to be seen whether Imperva’s reports of increased targeting of Australian entities will see a spike in extortion attacks over this reporting period, but if the attacks on Optus and Medibank are anything to go by - the ACSC will have no trouble padding out next year’s report.
Opalsec is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.
Microsoft shine a spotlight on Nation-State activity, increase in 0-days
Microsoft have published a certified-thicc annual threat report, coming in at 144 pages - all of which were needed to adequately explain the trends extracted from the ~43 trillion “signals” they ingested to generate the report.
Critical infrastructure is a clear target for Nation-States
Due largely on the Ukraine conflict, Microsoft noted a 100% increase in nation-state attacks on critical infrastructure, which was comprised of destructive attacks on Ukrainian infrastructure and espionage targeting their allies, in particular the US.
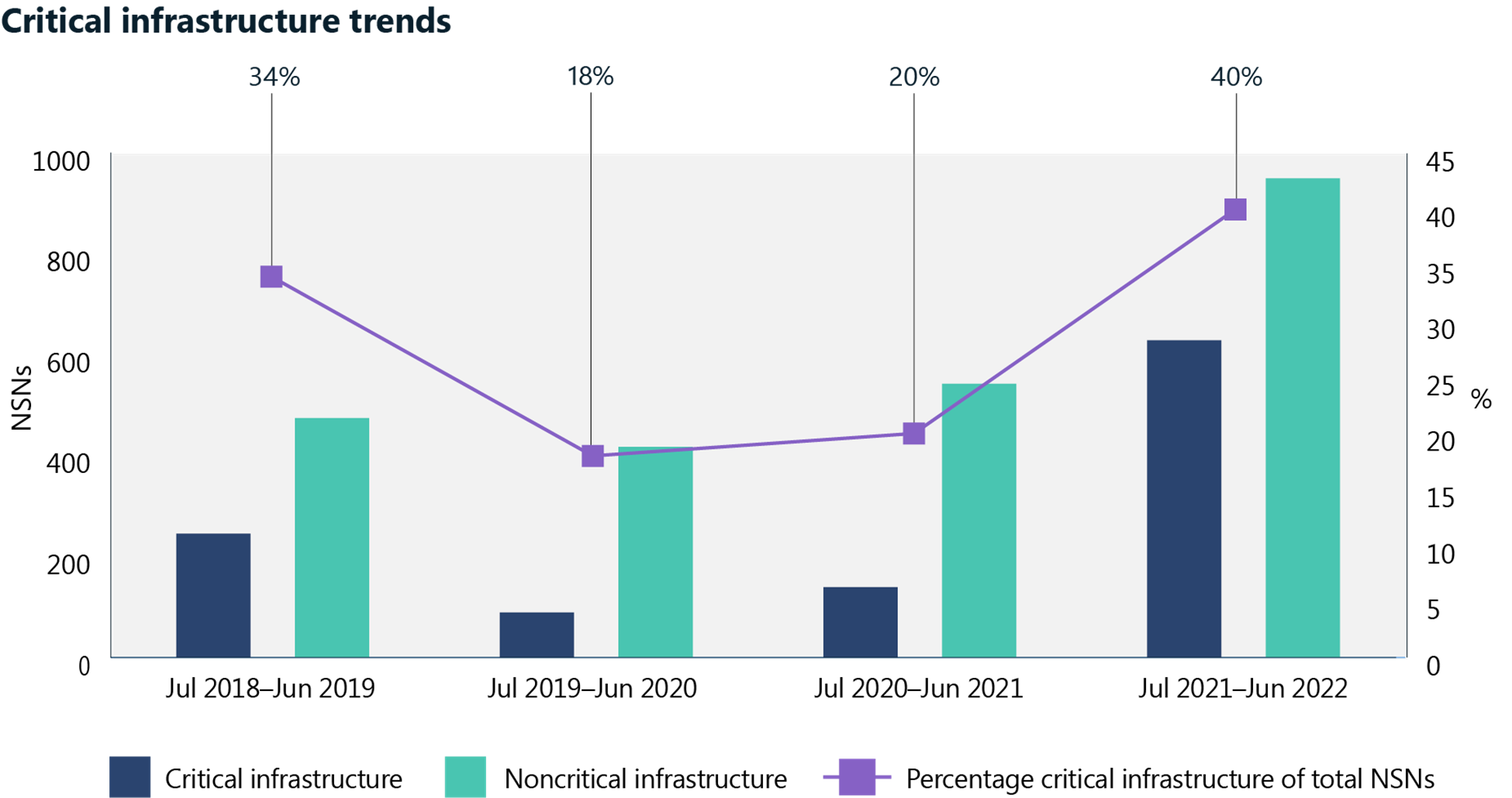
The Russian invasion of Ukraine further justifies the recent focus of lawmakers on introducing additional security and reporting requirements for critical infrastructure companies. It’s not just about disruptions to your supply of pork or oil as a result of ransomware, but in times of war, critical infrastructure is a target no adversary can - or will - ignore.
More 0-days, faster exploitation
The report also highlighted the continuing importance of quick patching cycles, with 41 0-day vulnerabilities patched during the reporting period, and in-the-wild exploitation observed on average just 14 days after disclosure.
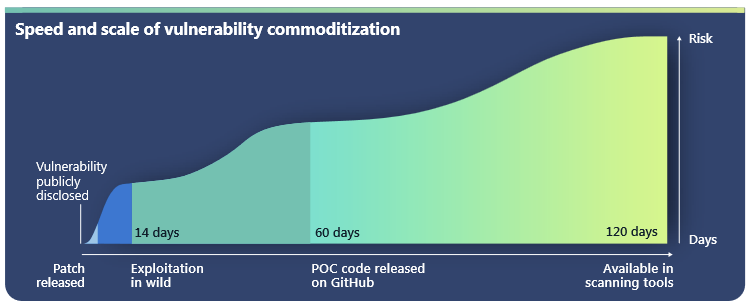
Microsoft also warn against organisations with vulnerability management programs being lured into a false sense of security, noting that 0-day exploits are abused “broadly in a short period of time”.
While it’s a much more significant ask to detect an 0-day being exploited, an actor’s post-exploit actions are much more predictable and easier to detect, and should be the focus of Hunt & Threat Detection teams seeking to mitigate this threat.
China exploit their home-court advantage
In a spicy take, Microsoft have essentially accused the Chinese government of abusing their new vulnerability reporting rules to get the jump on weaponising and exploiting 0-days before they can be patched.
Introduced in September last year, Chinese vendors and security researchers have since been required to share vulnerability reports with Chinese government authorities before providing them to the product or service owner.
Microsoft note this has enabled Chinese state-sponsored actors to be “particularly proficient” at weaponising 0-days, pointing to a set of five CVSS 9.8+ vulnerabilities that Chinese actors were spotted exploiting before anyone else.
This spate of 0-days being seized on by Chinese actors coincides neatly with the mandatory vulnerability reporting requirements taking effect, and appears to be evidence of what many thought would happen, taking place.
It shouldn’t surprise anyone that China is taking any advantage it can gain, but must be acknowledged as another tangible risk that makes it imperative for organisations to have quick patching and comprehensive monitoring for post-exploitation activities.

Robin Banks improves evasion, bypasses MFA with open-source tools
Researchers from IronNet have followed up on their original exposé of the Robin Banks Phishing-as-a-Service (PhaaS), highlighting a series of new features added to the Dark Web offering aimed at hindering analysis and bypassing MFA protections.
The phishing kit used by the service is now obfuscated by the open-source obfuscation script PHP Obfuscator;
A “commercial” Cloaker/Bot filter/Ad tracker offering, Adspect, is being used as a Traffic Direction System that shunts victims to the intended malicious site while redirecting any potential automated scanning tools or security researchers attempting to analyse it to benign websites;
Customers can now bypass MFA prompts by using an adaptation of evilginx2 to intercept login session cookies, as part of the Phishing attack flow;
Users of this feature also benefit from a static blacklist of IPs of known online scanners or bots, and acts as another measure to filter out attempts to identify and analyse campaigns conducted through this service.
The continued development of this PhaaS offering highlights the degree to which the cyber crime ecosystem has evolved into a marketplace of specialised service providers. This lowers the barrier to entry for aspiring cyber crims, providing automation, obfuscation, and even the ability to bypass MFA protections - the highest form of authentication security many organisations and the majority of individuals are able/willing to adopt.
While not unique in its ability to bypass MFA, the fact this feature is becoming more commonplace in Phishing kits and PhaaS offerings is concerning.
Organisations need to remain conscious of the fact that MFA can be readily bypassed by open-source projects such as evilginx2, making the ability to identify and investigate anomalies an essential function for any SOC.
Found this useful? Why not share it!
Other Reporting
The RomCom RAT - a backdoor that’s been heavily distributed within Ukraine - has recently been observed being distributed from typo-squatted and cloned download portals purporting to deliver SolarWinds Network Performance Monitor (NPM), the Veeam Backup & Recovery software, KeePass password manager, and PDF Reader Pro installers;
Kaspersky have released a pair of reports looking at a campaign conducted by China’s APT10, who used spear-phishing to deliver a legitimate K7Security Suite software binary. Thanks to search-order hijacking, this loads the group’s LODEINFO backdoor when executed, as it’s in the same folder under the name of a legitimate dll the binary expects to load.
Group-IB have a report on OPERA1ER, a.k.a. Common Raven, a rarely reported on threat group that is one of the few left targeting SWIFT - the interbank payments processing platform. In the embodiment of the adage “using a cannon to kill a mosquito”, they were observed investing 12 months in order to gain enough network access to programmatically dispense money from ATMs;
We’ve been blessed this week with two reports analysing intrusions enabled by Qakbot infections:
DFIR Report have analysed an intrusion from June this year where a maldoc abusing the Follina vulnerability dropped Qakbot malware, followed by the interactive installation of Remote Management Tools and Cobalt Strike. The attackers pilfered sensitive documents from a file server, then bailed;
Cynet’s Orion Threat Research Team have published a report that examines recent Qakbot TTPs and its relationship to the Black Basta ransomware;
This is a great report by Elastic that looks at IcedID TTPs and shares a config extractor and tips for how to track their infrastructure;
SentinelOne have speculated at ties between the FIN7 cyber crime actor and the operators of the Black Basta ransomware. While plausible, the links appear to be primarily based on overlaps in tooling or development resources, so should be taken with a grain of salt;
Proofpoint have identified a SocGholish campaign that was distributed through the supply chain compromise of a media company delivering video content and advertising for major news outlets in the US;
Team Cymru have shared a piece looking at RaccoonStealer v1, and potential links to the CC2BTC marketplace as part of the group’s monetisation strategy;
Sekoia have profiled BlueFox, a new infostealer sold as a subscription and marketed on the Dark Web to traffers;
Cyber Intel firm KELA’s Q3 2022 ransomware report found IABs were making a killing, fetching an average selling price of $2800 with the “average time to sell corporate access was just 1.6 days, while most were of RDP and VPN types”;

Jupyter Notebooks opened Azure Cosmos DB to enumeration, RCE attacks
Researchers from Orca Security have reported on a now-fixed critical vulnerability in Azure’s Cosmos DB that would allow an attacker to remotely enumerate, view and modify containers - including to the point of enabling code execution on vulnerable instances.
Cosmos DB comes with in-built Jupyter Notebooks that can be used to query and visualise the database contents, and it’s a lack of authentication checks around the access of these Notebooks that provides unauthenticated users full permissions to them.
This flaw would allow an attacker to use simple HTTP PUT requests with JSON payloads to modify, overwrite, or delete the contents of a given Notebook. Orca Security researchers demonstrated the full impact of this by injecting Python code to the file that builds the Explorer Dashboard, resulting in a reverse shell being provided when the Data Explorer is loaded.
Microsoft pointed out that 99.8% of Cosmos DB users aren’t impacted as they don’t use Jupyter Notebooks, and that the bug was fixed within two days of it being reported.
Other Vulnerabilities
A much-hyped OpenSSL vulnerability is downgraded and limited in scope
Despite the advanced warning, a much-anticipated disclosure of a vulnerability in OpenSSL turned out to be a fizzer.
The RCE bug was downgraded from Critical to High on release; impacts a tiny subset of deployments using 3.0 minor versions released from September 2021 onwards, and is challenging to exploit - to say the least.
Organisations running OpenSSL v3 are still encouraged to update to the latest version to patch the flaw, but other main version branches of the project remain unaffected.
Opalsec is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.
ConnectWise scramble to patch after sleeping on a researcher’s report for 90 days
Both ConnectWise and Huntress have elaborated on last week’s rushed patch for a potentially wormable vulnerability in ConnectWise kit, which appears to have stemmed from the product’s use of an old version of the ZK Java library that was vulnerable to an authentication bypass bug (CVE-2022-36537).
While it’s bad enough that ConnectWise appear to have been unaware of this software supply chain vulnerability in their product, it also shouldn’t be overlooked that they ignored an initial report from a researcher for more than 90 days, prompting them to tease details of the vulnerability on Twitter.
Organisations are reliant on vendors identifying and quickly remediating vulnerabilities in the products they provide.
In this case, ConnectWise was completely reliant on Huntress having gone out of their way to identify and demonstrate the vulnerability. Without it, it’s anyone’s guess as to whether it would’ve been picked up by them, or worse - a malicious actor.
ConnectWise need to learn from and improve on this, because with nearly 5000 vulnerable instances exposed to the internet prior to the patch being shared - this all could have turned out very differently.

Offensive
- Impersonate - A collection of tools that abuses Windows token manipulation to elevate privileges without needing to touch lsass. See how it was used to get DA in this accompanying blog post;
- Need more Impacket scripts to add to your arsenal, or just want a few more for reference when building your own? Check out this repo that features four home-made scripts to help you on your way;
- Subdomain takeovers are an underrated bug class - check out this post with learnings from 217 bug reports on how to enumerate them with minimal fuss.
Defensive
- Legitify – an open-source security tool for GitHub users to automatically discover and remediate insecure GitHub configurations, at scale;
- SuperMem - A python script developed to process Windows memory images using volatility, based on triage type;
- Essential reading for anyone on an Ops team that automates analysis with urlscan.io - researchers at Positive Security have highlighted the potential for automated scans to inadvertently run on and leak sensitive documents. This is similar to the risk posed by automating scanning of documents using VirusTotal, and in this case the searchable results in urlscan revealed API Keys, account setup/reset links, Government Zoom invites, and more;
- VMWare’s Threat Analysis Unit have shared detailed analysis of the ShadowPad backdoor - used by Chinese Threat Actors and an apparent successor to the notorious PlugX malware;
- Palo Alto’s Unit42 have done a deep dive on GuLoader, and shared their write-up on how to work around its anti-analysis measures;
- Windows Registry is abused by all manner of threat actor and across multiple vertices in the ATT&CK Matrix. SpecterOps have shared this handy primer to how it works, how it’s secured, and how you can monitor it as a Defender;
- Stephan Berger has shared another great thread on hunting for Cobalt Strike’s use of named pipes;
- For those using the Wazuh agent in your environments, SOCFortress have shared several “advanced” detection rules for free;
- Here are a few samples and a YARA rule for Hive ransomware - if that’s your thing.

- US Treasury's Financial Crimes Enforcement Network (FinCEN) have reported that ransomware cost US banks ~$1.2bn last year, with the 188% increase likely influenced by OFAC encouraging more reporting in the 2nd half of 2021. 84 variants were reported, with ~58% of those connected to Russian Threat Actors;
- The EU’s peak Cybersecurity agency, ENISA, have shared their latest Threat Landscape report. One key finding that’s as noteworthy as it is disappointing is that they believe ~60% of ransomware victims have paid ransom demands;
- BEC scams are alive and well, with a group dubbed Crimson Kingsnake impersonating a variety of law firms and debt collectors in the US, Europe, Australia and Middle East, using 92 lookalike domains and social engineering to scam businesses into paying bogus overdue invoices;
- DropBox reported that the contents of 130 of their private Github repos were swiped by an attacker that successfully Phished their way past their OTP-based MFA controls. The contents stolen appear to be largely internal dev tools and content, with no core apps or customer data compromised as a result of the breach;
- Solarwinds have caved to a law suit lodged by investors over the 2020 breach by Russia’s APT29 that resulted in the downstream compromise of ~100 private and government customer networks. It wasn’t without a fight, and despite agreeing to a $26 million settlement, they haven’t admitted any wrongdoing;
- Speaking of Solarwinds, the NSA have shared guidance for software suppliers to secure their supply chain;
- Not to be outdone, CISA have shared guidance on implementing Phishing-resistant MFA, and Number Matching in MFA applications - two measure that can supplement soft-token MFA measures to protect against social engineering;
- Check out this recording and the full paper looking at six 0-click exploits chains abused by NSO Group’s Pegasus malware.
Opalsec is going on holiday!
I’ll be taking a break from writing newsletters for a few weeks, and will be back on deck in December.

If you find yourself struggling to keep up with the news, feel free to ping me at opalsec@substack.com and I can send you an invite link to my Discord server that I use to keep track of noteworthy reporting throughout the week!
Opalsec is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.





