SOC Goulash: Weekend Wrap-Up
09/01/2023 - 15/01/2023

JsonWebToken vulnerability highlights the futile state of supply chain security
Authentication technology company Auth0 has addressed a critical flaw (CVE-2022-23529) in the input sanitisation routine of their open-source JsonWebToken package, which would have allowed arbitrary file write and remote code execution on vulnerable deployments.
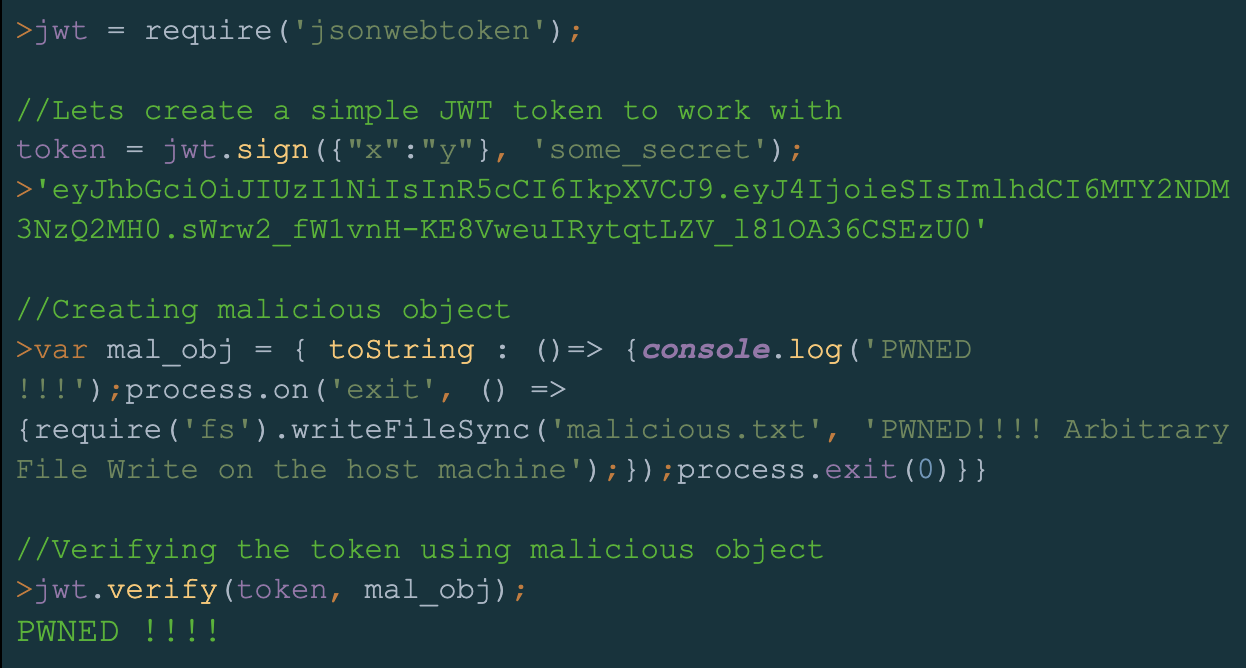
The JavaScript package, which is used to verify and sign JSON Web Tokens (JWTs) in authorisation and authentication flows, is used by over 22,000 projects created by the likes of Microsoft, Salesforce, Docusign, Slack, SAP, and more; and has over 9 million weekly downloads on npm.
Per their advisory, downstream projects must upgrade any instances below 8.5.1 to version 9.0.0 in order to mitigate the vulnerability.
What you don’t know can’t can hurt you
While it’s widely accepted that modern technology stacks are built on tangled webs of package and library dependencies, there remains no mandated standard that requires this to be listed clearly by vendors when selling their products. Without it, organisations have no choice but to rely on vendors being aware of their dependencies and patching vulnerabilities as they emerge.
As the Log4Shell saga of 2021 showed us, though - that’s much easier said than done.
In this case, the number of products which could be impacted are too many to count, from custom web apps to network appliances to 3rd-party SaaS solutions and even corporate authentication providers - they’re all potentially at risk if they use JSON Web Tokens to enable authentication and authorisation flows.
It looks like for now, the status quo will have to do.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber!
Kernel space isn’t just for the cool kids anymore
Crowdstrike have shared a report highlighting the evasive measures taken by the financially-motivated SCATTERED SPIDER (UNC3944) actor, who abused the Bring-your-own Vulnerable Driver (BYOVD) technique in a recent campaign.
The actor attempted to deploy an Intel Ethernet driver with a nearly 8 year-old vulnerability (CVE-2015-2291) that would have allowed them to load a malicious driver into kernel space. This malicious driver was designed to circumvent the EDR product deployed on the host by patching “specific routines” in the EDR agent’s driver, effectively blinding it so the attacker could continue unimpeded.
While the technique is nothing new, the use of a legitimate, 8 year-old vulnerable driver is a good reminder that even if you eliminate vulnerable drivers from your network through diligent patching - they can still be dropped silently by actors trying to get access to the kernel, and may not be detected unless you’re monitoring driver activity closely.
Don’t get caught out
Looking at the table in this article by Rapid7, you can see that the abuse of BYOVD has become much more frequent since the late 2010’s and onwards, and have been employed by a broader range of actors including cyber criminals such as BlackByte ransomware in 2022, and now SCATTERED SPIDER.
Given this, it’s worth evaluating and improving your organisation’s ability to mitigate and detect this technique - perhaps starting with these 3 points of best-practice:
- Enable Hypervisor-Protected Code Integrity (HVCI): This solution was designed to prevent users with elevated privilege from being able to read and write to kernel memory, and would therefore prevent the execution of malicious code in kernel memory via a vulnerable driver;
- Implement Microsoft’s driver block rules via Windows Defender Application Control (WDAC) - though you’d be forgiven if you didn’t trust it;
- If you have the bandwidth to implement this in your network, you could supplement the above list with this Sigma rule containing hashes of known vulnerable drivers.

Raspberry Robin infrastructure proves flexible, but vulnerable to hijacking
A collaboration between Sekoia and Team Cymru S2 analysts has shed light on the multi-tiered, growing, and highly flexible infrastructure used by the Raspberry Robin malware.
Significantly, despite its flexibility and resilience, several flaws were exposed that open it up to potential takeover by 3rd-party actors.
Multi-tiered Infrastructure
The first hop C2 of compromised QNAP devices were found to be routed back to the attackers via a cluster of Linode VPS servers, which themselves act as forward proxies to an additional (still unknown) infrastructure layer.
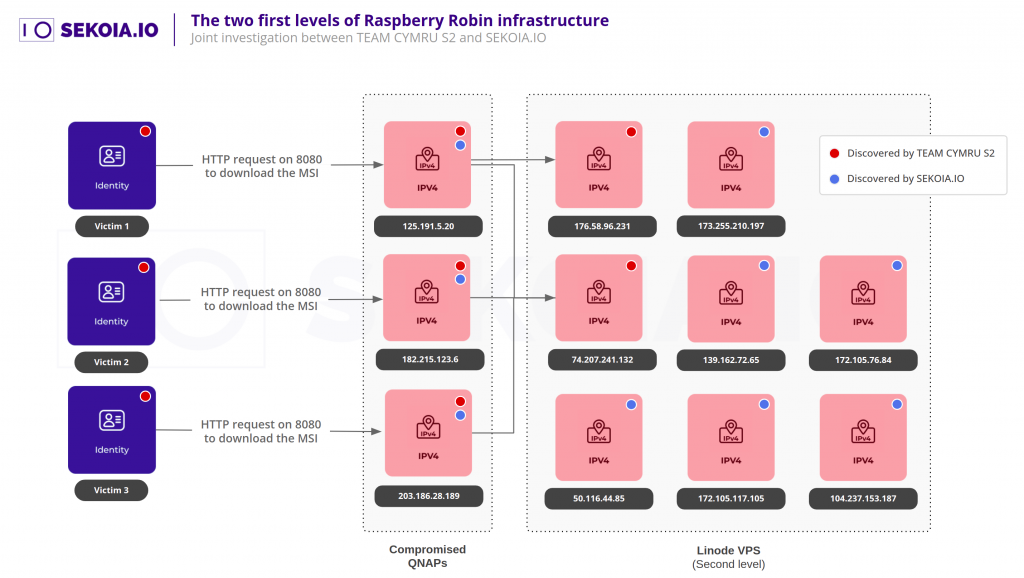
Utilising multiple tiers of C2 infrastructure is a common practice among offensive actors, as it impedes attempts to uncover the identity and origin of the operators while also allowing the infrastructure to be flexible, switching out hosts as they are identified and blocked by security researchers or taken down by law enforcement and hosting providers.
Growth & Flexibility
The operators of the Raspberry Robin network also appear to be keeping a close eye on their C2 infrastructure, with the researchers noting they abandoned an operational QNAP instance within days of it coming under scrutiny.
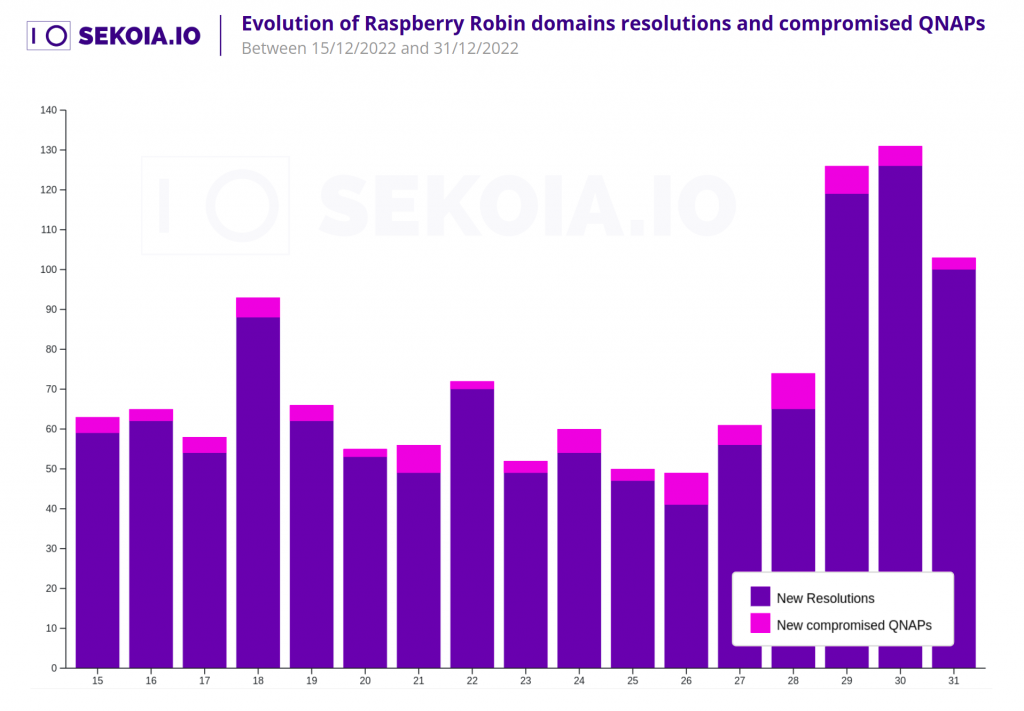
To facilitate this flexibility in C2 infrastructure, new QNAP instances are being compromised every day and the domain resolutions for the back-end infrastructure are constantly changing.
Sekoia’s analysis identified 80 new QNAP instances being compromised and 1154 changes made in DNS resolutions in the 16 days to the end of 2022:
Adaptable but insecure
The flexibility that DNS resolution affords the actors has proven to be a double-edged sword - while it provides a degree of resilience to 1st-tier C2 boxes being lost, it also relies on those domain names remaining active and under the control of the operators.
This limitation was tested in October last year, where domain registrar namecheap.com deactivated and quarantined 80 domains used by the group, representing a loss of almost 30% of the DNS records in use by active infections at the time.
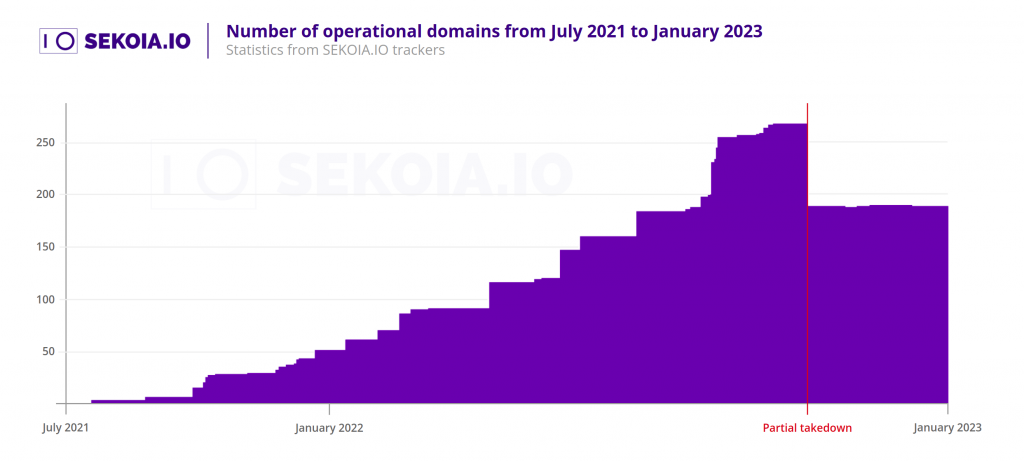
Schadenfreude aside, Sekoia analysts also pointed out that the malware’s reliance on msiexec to download the second-stage payload has meant that such requests could also be co-opted by other actors employing DNS hijacking techniques such as Quantum DNS.
Initial access, but for whom?
More significantly, they proved it was possible to re-register expired domains used by the botnet, successfully doing so and finding numerous infections from the first-wave of Raspberry Robin infections beaconing in from across the world.
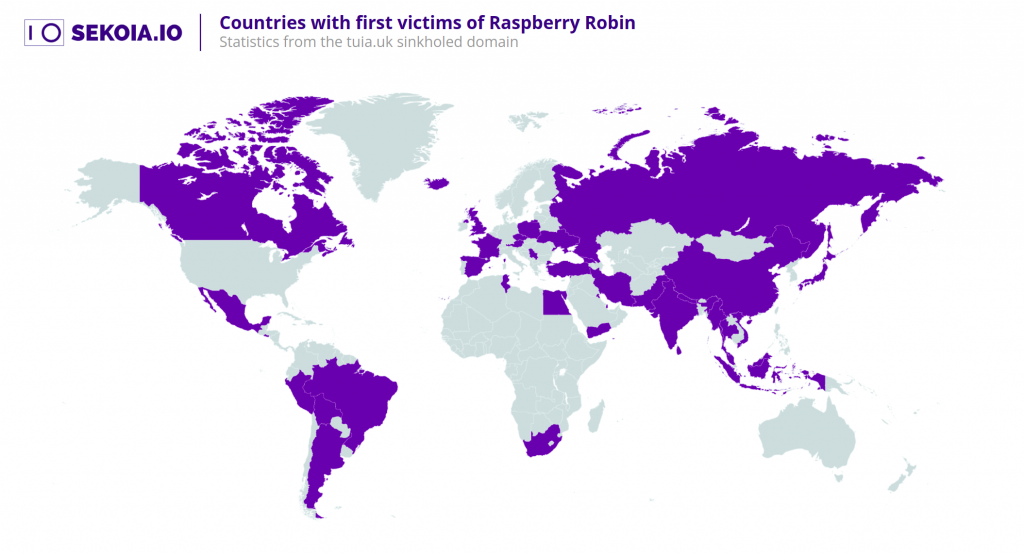
This is significant as it means that portions of the botnet could be co-opted by an unknown third-party, should Raspberry Robin’s operators allow domain registrations to lapse. It might sound far-fetched, but in fact must be viewed as a credible risk when weighing up the threat Raspberry Robin poses to your enterprise.
Just last week, Mandiant reported the Russian Turla group had leveraged this exact vulnerability, re-registering expired domains for the decade-old Andromeda botnet and cherry-picking implants of interest that they then tasked with downloading additional malware.
Like Andromeda, one of Raspberry Robin’s methods of spreading is via infected USB drives. With infections using C2 domains from the first infection still beaconing in, it’s believed that it is still spreading - and will continue to spread - via infected USBs. This makes Raspberry Robin a long-term threat, and we may not have to wait 10 years for a malicious hijacking of infrastructure to materialise.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber!
Other Reporting
- Group-IB have shared their analysis of activity by a group they call Dark Pink, believed to be a new APT group targeting military and government bodies in the APAC region, as well as Bosnia and Herzegovina;
- Cyber security consultancy S-RM have reported that actors behind an intrusion utilising Lorenz ransomware had in fact breached the network five months prior by exploiting a vulnerability in their Mitel telephony infrastructure (CVE-2022-29499). The real gotcha, though, is that the victim had patched the vulnerability…unfortunately, one week after the actors had already compromised the device and dropped a backdoor for later use. A timely reminder that hunting for evidence of exploitation is still a necessary step in the vulnerability management cycle;
- Trend Micro have warned of a shift of targeting in GootLoader campaigns, with a renewed focus on performing SEO-poisoning of search results for organisations in the Australian healthcare industry;
- Microsoft have noted an uptick in exploit attempts targeting Kubernetes clusters and misconfigured PostgreSQL containers by actors spreading the Linux Kinsing malware;
- After initially denying involvement, a spokesperson for the LockBit ransomware group has confirmed an affiliate was responsible for the compromise of the UK’s Royal Mail. What’s noteworthy is they seemed genuinely unaware an affiliate was involved, hinting at a sprawling affiliate-enabled ransomware operation that they’re struggling to coordinate effectively;
- The DFIR Report have shared their latest issue, looking at a Ursnif infection that progressed through to AD compromise and enumeration of a backup server;
- This report by Cybereason details the TTPs used and speedy progress attackers made in an intrusion enabled by IcedID malware, resulting in compromise of AD in 24 hours an exfil commencing within 48;
- Red Canary have issued a warning for eBPF malware, with a ground-up explanation of how the technology works, before delving into the ways malware can - and have - abused it to intercept network traffic and evade detection.

StrRAT and Ratty use polyglot files and junk headers to evade scanners
DeepInstinct have shared a summary of their observations of evasion techniques used in Ratty and StrRAT campaigns throughout 2022, finding a recurring penchant for preying on automated scanning tools’ reliance on file headers for file type identification.
The actors distributing these malware families consistently use JAR files to deliver the malware, but have used several different methods to circumvent file header-based signaturing:
- MSI polyglots: Because MSI files are prepended with a file header and JAR files are identified by a record at the end of the file, a file can be constructed that is both a valid MSI and JAR file. This polyglot file will be detected and scanned as an MSI file, with the JAR component left untouched and waved through the scanner;
- CAB polyglots: Similar to MSI files, CABs are identified by a file header with a known sequence of “magic bytes”. This means the attacker can use the same technique of concatenating the two files in order to evade detection of the malicious JAR payload;
- Junk hex and binary content: Appending arbitrary blobs of hex or binary content to a JAR file will similarly confuse scanners, which will instead identify the file as a “data” file type.
CAB/JAR polyglot samples were able to achieve detection rates as low as 6/59 on VirusTotal, making this a worthwhile endeavour for Ratty/StrRAT operators.
It should also be noted that JAR files don’t need an extension to be executed as one - simply the right command-line arguments - which complicates extension-based scanning as well.
The most reliable detection would be to search for the central directory record appended to the end of a JAR file, though this isn’t something that’s supported out-of-the-box for many automated scanning solutions.

Month-old FortiOS vulnerability exploited by unknown stealthy actor
Fortinet has revealed that an “advanced actor” has leveraged an 0-day vulnerability (CVE-2022-42475) in FortiOS VPN appliances, to attack government and government-related targets. The vulnerability, which was patched last month, allows an unauthenticated attacker to execute arbitrary code via crafted requests, and was abused to deploy a generic Linux implant that was modified to work on FortiOS.
This implant was used to load additional malware and execute commands on the victim host - unfortunately, Fortinet were unable to recover the secondary payloads, and have no further insight into what they were.
Moreover, the attackers took exceptional steps to hide their presence, with the malware tailored to manipulate FortiOS logs and even to patch or terminate the logging process altogether in order to remain undetected.
The actor has not been identified, but demonstrated a “deep understanding of FortiOS and the underlying hardware”, and is believed to operate in the UTC+8 timezone which captures Australia, China, Russia, Singapore, and other Eastern Asian countries.
Patches are available for impacted products, and given the sophistication and speed of exploitation of this vulnerability - it’s one worth pushing in Production, even if your organisation’s Change Freeze is still in place.
IOCs have been provided at the end of the advisory, along with investigative steps outlined in this PSIRT article.
Found this useful? Why not share it!
Unpatched CentOS Web Panel instances under active exploitation
PoC exploit code shared in early January for a critical vulnerability in the CentOS/Control Web Panel (CWP) has enabled attackers to scan for and trivially exploit internet-facing instances that had not yet been patched.
Researchers from the Shadowserver Foundation have observed scanning and exploitation attempts that have provided the attackers with an interactive terminal or reverse shell that they’ve then used for onward compromise of the system.
While patches for the CVSS 9.8 remote code execution vulnerability (CVE-2022-44877) were released back in October last year, it appears some portion of the over 400,000 internet-facing instances found on Shodan are yet to implement them and are being targeted:
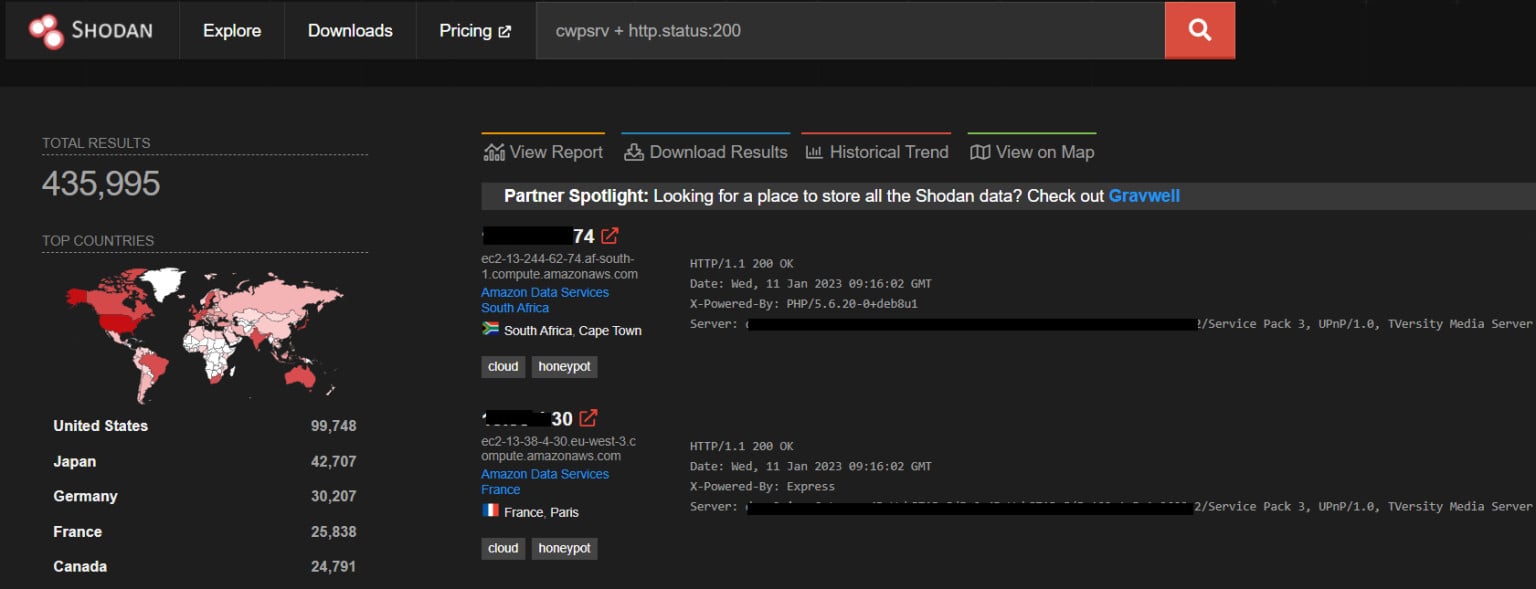
If you’re among those who haven’t addressed this vulnerability, make sure it’s one on your to-do list for Monday, along with checks for potential exploit attempts and post-exploit activity.
Other Vulnerabilities
No patches for critical auth bypass bug in Cisco’s EoL small business routers
Several of Cisco’s end-of-life (EoL) small business routers are vulnerable to a critical authentication bypass vulnerability (CVE-2023-20025), with a public exploit known to be available.
By sending a crafted malicious HTTP request to the vulnerable router’s management interface, an attacker would be able to circumvent authentication checks and gain root access on the appliance’s management panel. Worse still, chaining it with another vulnerability announced at the same time - CVE-2023-20026 - would allow the attacker to execute arbitrary commands on the underlying operating system
Cisco haven’t provided patches or workarounds, and have instead advised customers still intent on using the vulnerable kit to disable Remote Management and the ports required to access it.
Cuba ransomware the second to leverage Exchange OWASSRF flaw
Microsoft have reported that a threat group they track as DEV-0671 has been observed leveraging the OWASSRF vulnerability in Microsoft Exchange to deploy Cuba ransomware.
This makes them the second threat actor known to abuse the flaw, following Play ransomware’s compromise of cloud computing vendor Rackspace late last year.
The vulnerability has been added to CISA’s KEV and is being actively abused by at least two actors to deploy ransomware - one of which resulted in the turfing of Rackspace’s hosted Exchange product, and the revenue it would have otherwise generated the company.
If you haven’t patched by now, do it, but assume compromise and add threat hunting to your post-patch activities.
Three WordPress Plugins with critical vulnerabilities, patches…and public PoC exploit code
Popular WordPress Plugins Paid Memberships Pro, Easy Digital Downloads, and Survey Marker were all found to have SQL-based vulnerabilities with the first two receiving CVSS scores of 9.8, and Survey Marker scored a paltry 8.8, due to the attacker’s need to be either authenticated or a subscriber to exploit it.
The security researcher who discovered them released their findings publicly yesterday, which included PoC exploits that could be repurposed by malicious actors to leverage the vulnerabilities.
Patched versions of these plugins have been made available, so make sure you’re up to date.
(Ir)responsible disclosure - Lexmark printer exploit shared publicly
A security researcher has opted to publicly share an exploit and write-up for a vulnerability in Lexmark printers, after being offended by a “laughable” bug bounty offer for payout.
This effectively means it’s an 0-day exploit, with no patch available and Lexmark - presumably - playing catch-up in developing one.

Offensive
- Secret Handshake - a C2 channel that uses x509 certificates over mTLS. One for Defenders to be aware of too, as it doesn’t appear as straightforward to detect as you’d hope;
- Crassus - A tool for hunting PrivEsc vulnerabilities. It uses ProcMon Boot logs to highlight potential privilege escalation paths;
- Blaze Infosec have shared a straightforward AMSI bypass, enabled by simply replacing an TEST RDX, RDX instruction with XOR RAX, RAX in the AmsiOpenSession function of amsi.dll.
Defensive
- This post by Stairwell security is a great resource for anyone looking to get more proactive in detecting and mitigating Cobalt Strike stagers, and they’ve also kindly shared a stager decoder that they’re continuing to work on;
- Get under the hood of the Sliver C2 framework with this write-up of some static and dynamic analysis performed on an implant caught in-the-wild;
- Old mate Florian has shared a regex YARA rule looking for files in commonly abused world-writeable folder, referenced via environment variables. It looks to be pretty effective, so would be worth evaluating for use in your environment;
- JPCert have shared a cracker - how to automate Malware Analysis processes using AWS Lambda and Terraform;
- The good folks at TrustedSec have shared a comprehensive guide to credential dumping from LAPS - how to configure logging, what it looks like, and how to detect it happening;
- @inversecos walks us through how to identify a proverbial smoke-bomb attackers can use against Azure AD - generating fake events in Azure Sign-in Logs;
- Something I missed from last week but is definitely still worth flagging - Invictus’ write-up on how to investigate an incident in AWS using CloudTrail logs; manually parsing them with jq and picking them apart in Splunk;
- Found a malicious file in your IR case but don’t know how it got there or if a compromised user account created it? The $SDS artefact in NTFS file systems can show who owns and can access the file, indicating the likely creator of said file;
- @nas_bench has this thread looking at using the Microsoft-Windows-AppXDeploymentServer/Operational log to surface malicious AppX installations.

- On the lighter side of ChatGPT discourse, here’s a positive example of how you can use it to speed up your initial high-level assessment of a technical problem;
- For those looking to brush up on their DFIR skills in their spare time, check out this resource which provides several examples cases you can work through. If like me and you like having someone to compare your notes against as you go, here’s a write-up for #7;
- Another training resource for Windows Forensicators - check out the course materials for the Practical Windows Forensics course, hosted here for free. The course itself is just $29.99, for those who prefer to be guided through it;
- EmergingThreats have shared a Lab environment and notes that’ll help you get familiar with writing Suricata signatures, you can check out a recording of their talk presented at BSidesSLC here.
Opalsec is a reader-supported publication. To receive new posts and support my work, please consider becoming a paid subscriber!





