SOC Goulash: Weekend Wrap-Up (Part 1)
05/09/2022 - 11/09/2022
This is Part 1 of the Weekend Wrap-Up, detailing significant Threat Actor Activity and noteworthy TTP changes to be aware of.
Part 2 will cover significant vulnerabilities from the past week, in addition to the latest tools & techniques for offense and defence alike, and some additional reporting that you might find relevant and useful.
Headline Items
- The “cyber war” we’ve all been waiting for has been unfolding in the Middle East, highlighted this week through Iran’s politically-motivated attacks on Albania’s government and essential services, and series of reports looking at Iran’s state-sponsored threat groups;
- Qakbot have returned from summer break, distributing two distinct botnets that use either the Smokeloader malware or a Javascript loader for delivery and Scheduled Tasks for privilege escalation.

Spotlight on Iranian Threat Actors
References: Microsoft | Mandiant | Microsoft
A series of reports released this week by Mandiant and Microsoft have put the spotlight squarely on Iran’s offensive cyber activities and threat groups. Mandiant officially revealed their newly promoted APT42 threat group, while Microsoft released a detailed profile of DEV-0270 - better known as Iran’s Nemesis Kitten.
Microsoft’s report attributing attacks on the Albanian government to a set of Iranian threat groups set the scene for a severing of diplomatic relations by the Albanian government, and sanctions being levied by the US against Iran’s Intelligence Ministry and Minister. The conflict is ongoing, with Albania accusing Iran of having since launched another retaliatory cyber attack that’s impacted their seaports, airports and border posts.
The grugq published a great piece on this, noting the potential “cyber war” many pundits have been hyping up has actually been unfolding in the Middle East for some time now, and this is just the latest skirmish that’s made it into the news.
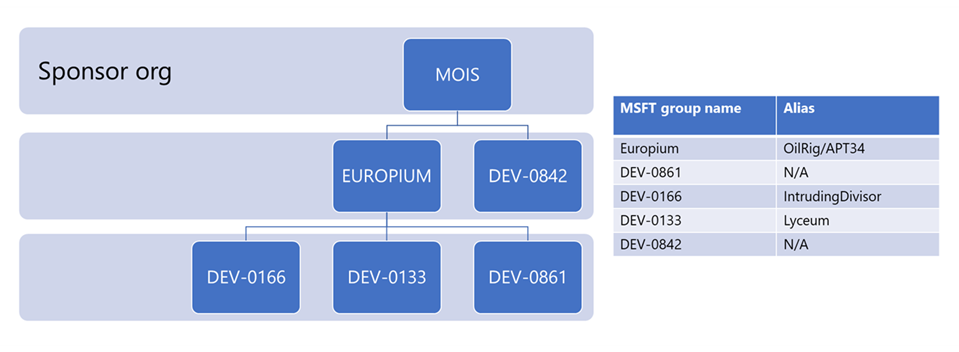
EUROPIUM sub-groups and DEV-0842 conduct destructive attack on Albanian government
Microsoft allege that several Iranian state-sponsored threat groups collaborated to deploy ransomware and wiper malware on Albanian government systems. Specifically:
- DEV-0133 probed victim infrastructure;
- DEV-0861 gained initial access & exfiltrated data;
- DEV-0166 exfiltrated data;
- DEV-0842 deployed the ransomware and wiper malware.
Like many industrialised threat groups, each participant appeared to have their own specialisation. The most noteworthy of these are DEV-0861, which acted as an effective Initial Access Broker for the group, and DEV-0842, who performed the final destructive attacks against the infected network.
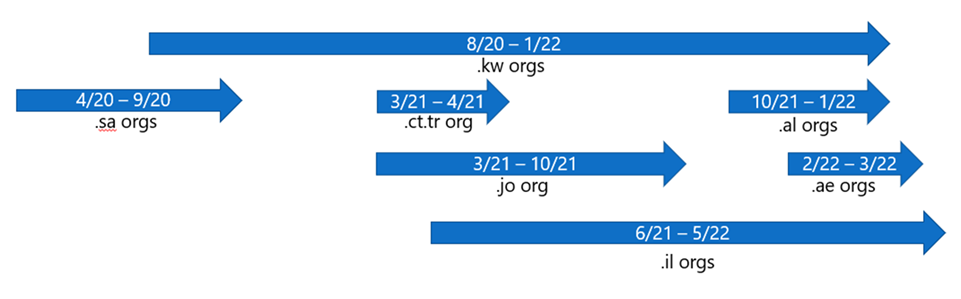
Initial access is believed to have been gained by DEV-0861 in May 2021 through exploiting CVE-2019-0604 on an unpatched Sharepoint server, with .aspx web shells being dropped to maintain persistence and mail exfiltrated via the Exchange web services APIs between October 2021 and January 2022.
Microsoft were able to correlate historical activity by DEV-0861 based on IPs used to exfiltrate mail, dating back to April 2020 and spanning six countries:
DEV-0842 was responsible for deploying ransomware on target systems, before following it with the ZeroCleare wiper. The ransomware was signed with an invalid digital certificate from “Kuwait Telecommunications Company KSC”, while the wiper contained a hex string which was a license key for the EldoS RawDisk driver, used to execute the wiper.
Key Takeaways
The protracted timeline leading up to the destructive attacks - more than one year from initial intrusion - are a good reminder that state-sponsored actors often act on long-term priorities which allow them to weaponise their accesses at a time that suits them and their taskmasters. A series of cyber attacks conducted against Iran provided that trigger, prompting the actors to repurpose what appears to have originally been an information-gathering operation to deploy destructive malware, crippling essential services in Albania as retaliation.
The use of cyber operations to further Nation-State objectives is nothing new. China wants to advance their aircraft design? They steal design schematics for the F-35. DPRK wants to steal some 0-days to give their hackers a competitive advantage? They target infosec researchers. Iran’s pissed a separatist hacktivist collective operating out of Albania has been hacking their networks? They get back at Albania to make a point about it.
Understanding a threat actor’s motivations are key to understanding the threat they pose to your organisation. In the case of state-sponsored actors, it’s essential to know where you stand in the world’s political and economic environment, and to be aware of events that might cause you to become a lightning rod for politically-motivated cyber attacks. Past targeting isn’t necessarily indicative of their current or future objectives, so it’s essential that security teams think outside of cyber reporting to keep ahead of the game.
APT42 targets Iran’s political opponents and enemies
Earlier this week Mandiant unveiled APT42 - a threat group they attribute to the Iranian Revolutionary Guard Corp Intelligence Organisation (IRGC-IO), that targets enemies and dissidents that oppose or are critical of the Iranian regime. The group target personal accounts and mobile devices, consistently targeting “Western think tanks, researchers, journalists, current Western government officials, former Iranian government officials, and the Iranian diaspora abroad.”
Their tradecraft relies heavily on targeted spear-phishing & social engineering techniques, which they use to build rapport with targets before attempting to deliver malware or gain access to their personal accounts. The report notes they specialise in credential harvesting and surveillance operations, deploying “mobile malware capable of tracking victim locations, recording phone conversations, accessing videos and images, and extracting entire SMS inboxes.”
Full details on the threat group’s tradecraft and tooling can be found in the official report, found here.
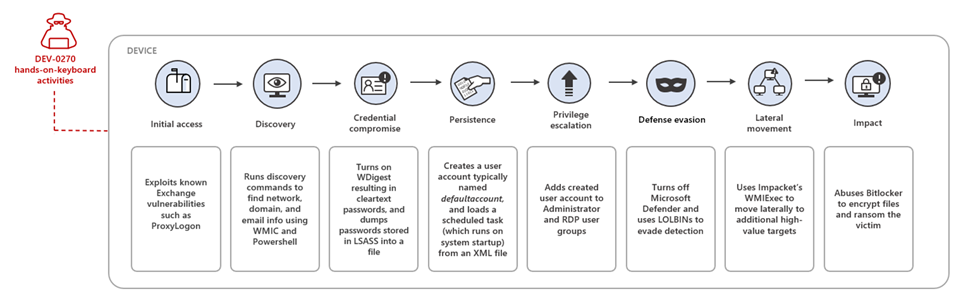
DEV-0270 - Iranian recon ops and ransomware
Microsoft believe that DEV-0270 may be dabbling in ransomware for personal gain, based on activities that they assess didn’t represent “strategic value” for the regime. This broadens their scope of targeting, and has prompted Microsoft to share a detailed profile on the threat group to aid in mitigating this threat.
Actor Summary
Better known as Nemesis Kitten, Microsoft believe this actor operates as a subset of the PHOSPHOROUS actor and maintains two public aliases - Secnerd (secnerd[.]ir) and Lifeweb (lifeweb[.]ir).
They are opportunistic in their targeting, and have historically been an early adopter of high-severity vulnerabilities such as ProxyLogon and Log4Shell - quickly scanning for and exploiting vulnerable devices to enable their offensive operations.
The group also make heavy use of LOLBINs for internal reconnaissance, credential access, and persistence. They typically disable Defender AV, and use PowerShell to load a custom root certificate into the local certificate database in order to encrypt and obfuscate their network traffic.
Lateral movement typically entails abusing RDP and Impacket’s WMIExec to pivot through the network. BitLocker is abused as a form of living-off-the-land ransomware, while the legitimate open source DiskCryptor software is deployed on workstations to encrypt entire hard drives.
Found this useful? Why not share it!

School’s back, and so is Qakbot
Qakbot have been on hiatus for six weeks, returning in force this week with multiple botnets, campaigns and execution chains observed in the wild.
Botnet #1 - snow01
References: @ffforward | Tria.ge | @pr0xylife
- The first wave of Qakbot appeared to be delivered via SmokeLoader, a common dropper for other malware;
- The payload masquerades as a png with a double extension (png[.]dll) and launches another instance of explorer.exe;
- It creates a scheduled task (schtasks.exe) that runs once, executing the Qakbot payload as SYSTEM using regsvr32.exe.
Botnet #2 - BB
References: @pr0xylife | Tria.ge | @phage_nz
Infections begin with the delivery of a malicious link which downloads a .zip archive that contains an lnk file;
When executed, it launches cmd.exe which:
creates the directory %appdata%\[A-Z]{2}\[a-z0-9]{3};
uses curl.exe to retrieve the contents of a html page, dumping it to a .js file in the previously created directory and executing it with wscript.exe;
This downloads and executes the qakbot .dll using regsvr32.exe;
The remaining execution chain is similar to the snow01 botnet - creating a scheduled task that launches the payload as SYSTEM.
Qakbot continue to use .lnk files to initiate their delivery chain, with the payload dropped as a .dll in world-writeable directories like %temp% and %appdata%. Monitoring for curl.exe outputting .js files will help in detecting delivery, while schtasks.exe has been used consistently this week to elevate the privileges the Qakbot payload runs with.
Thanks for reading! If you liked this, please subscribe for free to receive new posts and support my work!





