SOC Goulash: Weekend Wrap-Up (Part 1)
26/09/2022 - 02/10/2022
This is Part 1 of the Weekend Wrap-Up, detailing significant Threat Actor Activity and noteworthy TTP changes to be aware of.
Part 2 will cover significant vulnerabilities from the past week, in addition to the latest tools & techniques for offense and defence alike, and some additional reporting that you might find relevant and useful.
Headline Items
- Royal ransomware shows shades of Conti; the infamous Brute Ratel C4 framework gets cracked and distributed on cybercrime forums, and a China-based actor uses vSphere Installation Bundles to persist on ESXi environments;
- Qakbot distribution hits cruise control, while IcedID use 3 different delivery methods and decoy C2 configs to mess with analysis efforts;
- Microsoft scramble to address two actively exploited 0-days in Exchange; CERT coordinate discovery & remediation of vulnerabilities in Ethernet header stacking that could bypass inspection and prevention measures in enterprise network kit.

Royal Ransomware - a Conti fork continues big game hunting
Reference: Bleeping Computer
Vitali Kremez of Advanced Intel has shed light on Royal ransomware, which extorts victims for between $250k and $2 million and demonstrates overlaps with the defunct Conti ransomware operation. While the group has been in operation since January 2022, its activities are beginning to surface as more victims come out of the woodwork.
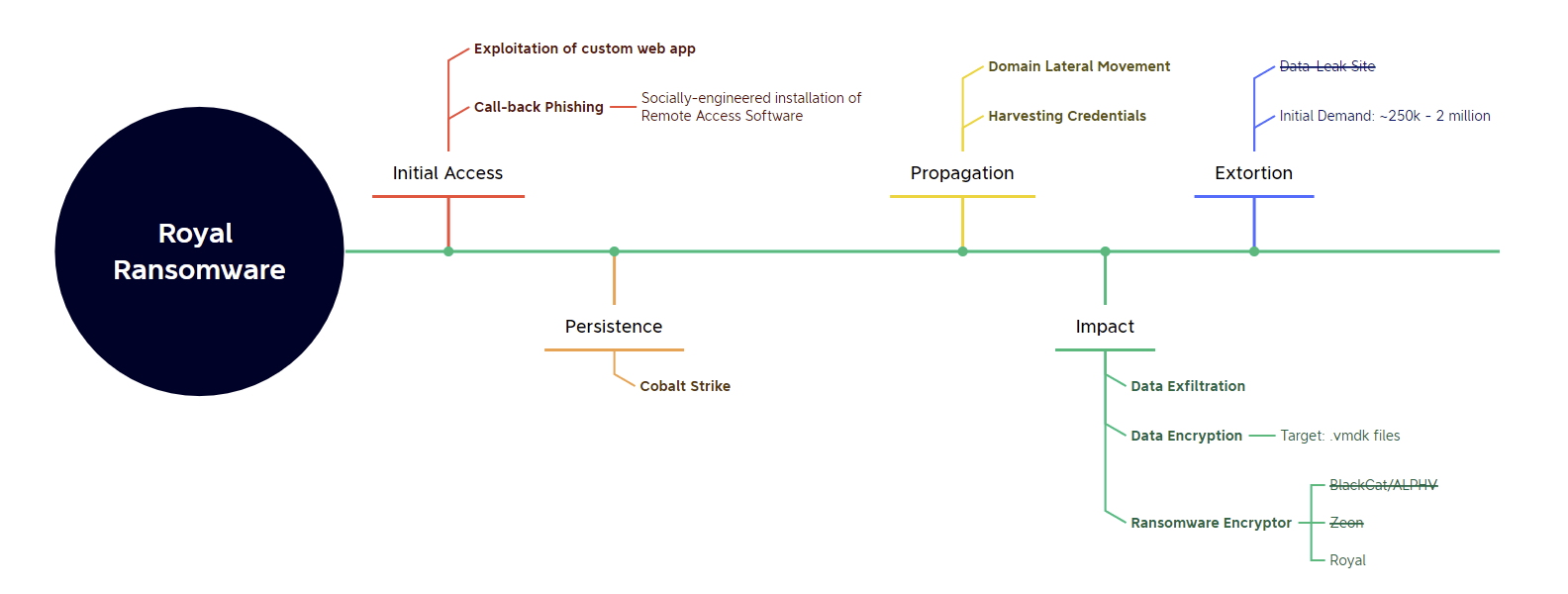
It’s noteworthy that the Royal operations share some cross-over with historical Conti activity, specifically:
- The ransom note generated through their previous Zeon encryptor was very similar to Conti’s ransom notes;
- They make use of Callback Phishing to manipulate users into installing Remote Access Software - a technique best known implemented through “BazaCall”, which often featured in Conti intrusions;
- Their consistently high ransom demands are indicative of “big game hunting”, and they operate as an exclusive collective - two traits exhibited by Conti during the life of the group.
While there’s little known about the group’s standard modus operandi, their overlaps with Conti and preference for high-value targets make this group one to watch.
As with the other Conti splinters, we can expect Royal ransomware operators to have a more mature and organised approach to operations than most.
In order to mitigate the initial access techniques employed by this group, consider incorporating Callback Phishing as an attack vector into user awareness training, and continue monitoring for and investigating installation of unapproved Remote Access Software on your network.
BruteRatel goes (involuntarily) mainstream
References: Bleeping Computer | BushidoToken
A cracked version of the highly capable and commercially-sold Brute Ratel C2 framework has been widely circulated on many “of the most populated cybercrime forums where data brokers, malware developers, initial access brokers, and ransomware affiliates all hang out.” This leak has sparked concerns that we may see an acceleration in the shift by threat actors away from Cobalt Strike, towards lesser-known and more evasive alternative C2 frameworks such as this.
First reported on in July this year by Unit 42, Brute Ratel’s use was much more limited with license-checking mechanisms restricting actors to the use of leaked legitimate copies - or in the case of several ex-Conti ransomware members - setting up fake US companies to purchase a license.
Unfortunately, given the license check was removed in the release of a cracked version, license revocation isn’t going to help here. The cat is well and truly out of the bag.
While initial, identified uses of Brute Ratel in-the-wild was limited to mature, organised actors such as APT29 and former Conti affiliates, the widespread dispersal of this cracked version means its adoption is likely to increase across the spectrum of cyber actors.
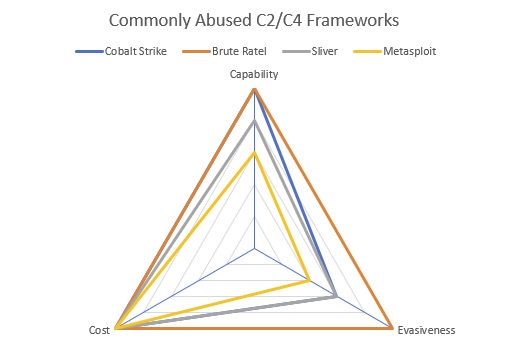
For Defenders
- MdSec published a detailed analysis piece on Brute Ratel when it first surfaced, so while it’s a good reference, some details may have changed in subsequent releases;
- @Kostastsale has some good hunting tips based on observable C2 traffic;
- Splunk have pulled together a collection of rules that align with Brute Ratel TTPs and behaviours.
Found this useful? Why not share it!
China-Linked Actor deploys VIB-packaged Backdoors, Dropper to ESXi
References: Mandiant (Part 1) | Mandiant (Part 2)
Mandiant have reported their discovery of two ESXi backdoors deployed via a novel method - vSphere Installation Bundles (VIB). VIB files are typically used by administrators to distribute software and manage ESXi systems, and are capable of creating “startup tasks, custom firewall rules, or deploy[ing] custom binaries upon the restart of an ESXi machine” - perfect for the discerning Threat Actor.
The actor, which Mandiant tracks as UNC3886 and is believed to have ties to China, modified the package to appear to be from an approved partner, and installed the VIB package using the —force flag. This technique was used to deliver VIRTUALPITA - a basic backdoor that listens on a hard-coded port, and VIRTUALPIE - a Python-based backdoor that listens on a hard-coded port for a connection over IPv6 .
While the impact of this attack was significant in its ability to grant attackers control of the ESXi environment and virtual machines it hosts, this is not a remotely executable attack, and requires administrative privileges to conduct.
VMWare ESXi has long been a valuable target for attackers due to it being used to host virtualised servers and workstations. Compromising it will - as was the case in this intrusion - enable execution of code on the server’s hosted VMs. Ransomware actors in particular have created tools and encryptors specifically targeted at ESXi environments, with household names like Black Basta, REvil, Lockbit, and Conti among them.
Mandiant have shared detailed guidance of system hardening and detection opportunities. The TL;DR is to make sure you’re ingesting ESXi logs and looking for the indicators flagged in the report, and set up a playbook for running Yara over SSHFS, or through a locally-installed instance to bypass potential latency issues.
Bonus round: VMWare have published a blog post looking at the many ways actors will look to delete Volume Shadow Copies, including a newly discovered method that abuses the Volume Shadow Copy Coordinator (VssCoordinator). Check it out.

Qakbot TTP Summary
Qakbot hit cruise control this week, with distribution across both botnets only varying in the initial delivery mechanism being either a malicious link or malicious html file. All other TTPs remained unchanged.
One noteworthy mention is two new process injection targets - msra.exe and iexplorer.exe, identified by @Max_Mal_ in their analysis of a Qakbot dll sample.
BB Botnet
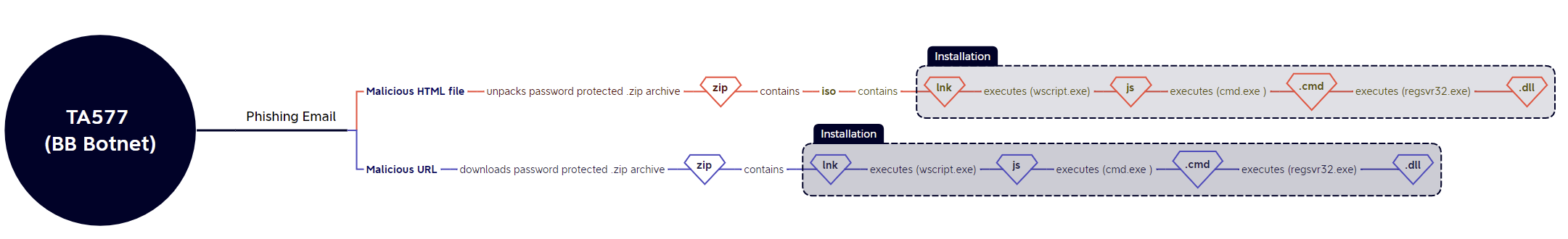
The TA577 was the most active distributor this week, and appeared to opt for malicious links as lures on all but one occasion at the start of the week. No changes over last week’s TTPs - I guess if it aint broke, don’t fix it?
26/09 (CampaignID: 1664184863, Distro #1): url > zip > iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | Malware Bazaar | Tria.ge
26/09 (CampaignID: 1664184863, Distro #2): html > zip > iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @0xToxin | Malware Bazaar | Tria.ge
27/09: url > zip > iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | @ExecuteMalware | Malware Bazaar | Tria.ge
28/09: url > zip > iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | Malware Bazaar | Tria.ge
30/09: url > zip > iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @pr0xylife | Malware Bazaar | Tria.ge
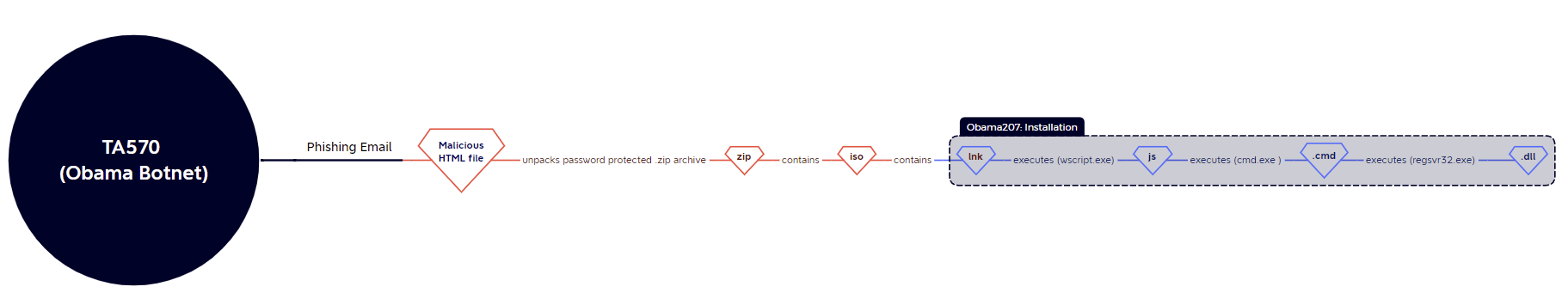
Obama Botnet
Not much was observed from the Obama botnet (TA570) this week, with the only analysed sample originating from a malicious HTML file and following the same execution chain as last week:
28/09 (Obama207): html > .zip > .iso > cmd.exe (.lnk) > wscript.exe (.js) > cmd.exe (.cmd) > regsvr32.exe (.dll)
References: @ExecuteMalware | Malware Bazaar | Tria.ge
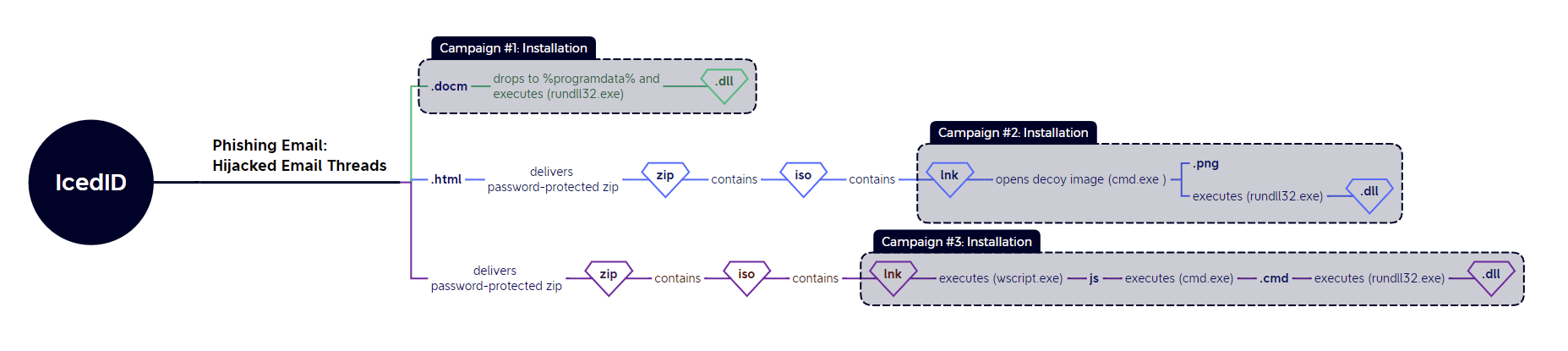
IcedID TTP Summary
IcedID was distributed through three distinct methods - either a macro-enabled .doc file; through a malicious html file that downloaded further stages, or in an execution chain nearly identical to Qakbot’s.
References:
- Campaign #1 - Tria.ge
- Campaign #2 - @pr0xylife
- Campaign #3 - @pr0xylife
Decoy C2 Configs
Another interesting tidbit to emerge this week came from Team Cymru, who noticed that samples they detonated appeared to contain dummy configs with domains that pointed to the same IPs of the C2s they retrieved.
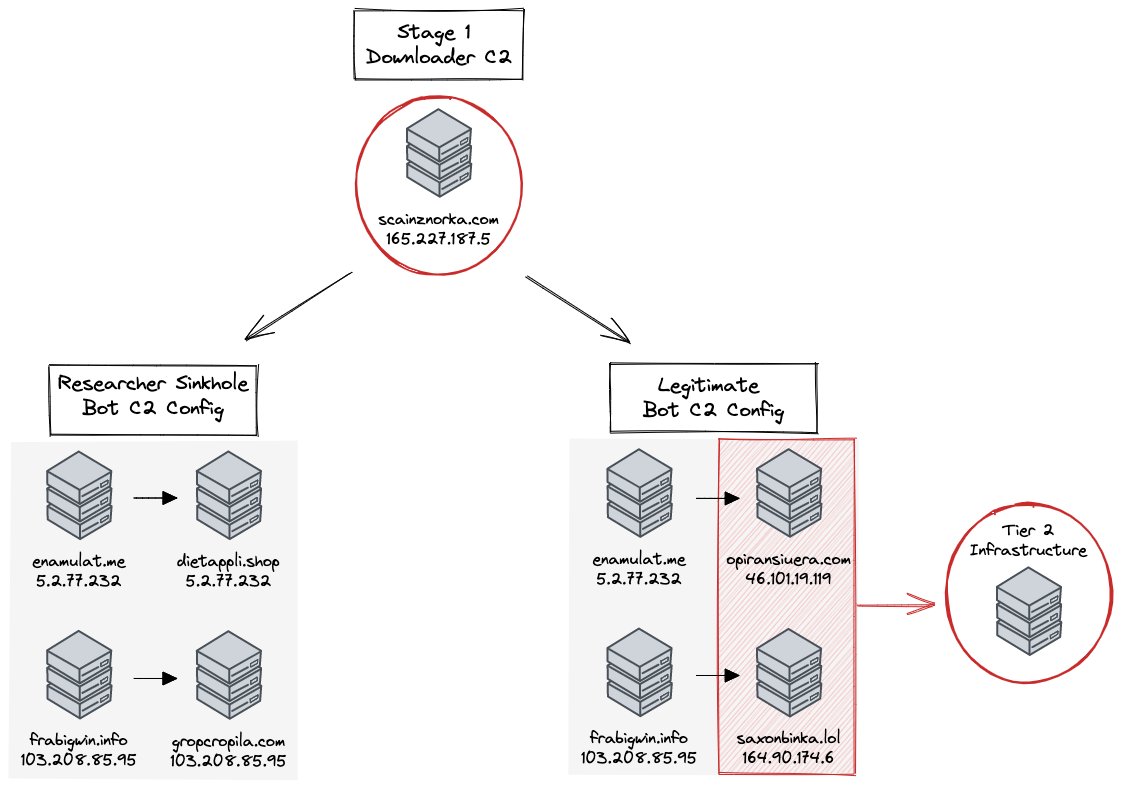
Configs for samples they detonated would update to the “true” config one day later, allowing for identification of the actual Tier 2 infrastructure used by the malware.
At this stage it’s unclear if timing is the only factor influencing the configs delivered to the detonated sample, but regardless it’s worth noting the network connections and DNS resolutions you see in sandbox results should be scrutinised carefully before deploying block rules and calling it a day!
Thanks for reading! If you liked this, please subscribe to receive new posts and support my work!





