SOC Goulash: Weekend Wrap-Up (Part 1)
12/09/2022 - 18/09/2022
This is Part 1 of the Weekend Wrap-Up, detailing significant Threat Actor Activity and noteworthy TTP changes to be aware of.
Part 2 will cover significant vulnerabilities from the past week, in addition to the latest tools & techniques for offense and defence alike, and some additional reporting that you might find relevant and useful.
Headline Items
- The Uber hack is indicative of a growing trend involving stolen credentials, socially-engineered MFA bypasses, and a lack of internal controls to detect or prevent onwards compromise;
- Despite changing TTPs throughout the week, Qakbot’s campaigns provide plenty of detection opportunities, while IcedID persists in using rtf maldocs and simple iso > lnk execution chains in their distribution;
- Teams stores plaintext authentication tokens on disk, and Microsoft have no plans to fix it - make sure you’re not caught out!

Uber Compromise reinforces the risks of relying on MFA
References: @vx-underground | @BillDemirkapi | El Reg | Dark Reading
Unless you’ve been living under a rock for the past few days, you’ve probably heard about the hack of Uber. I’m sure you’ve gasped at the sheer scale and depth of compromise; chuckled at many a meme, and exhaled sharply out of your nose as you waded through the many hot takes and ambulance-chasers taking to Twitter and LinkedIn.
So let’s not waste too much time flogging that dead horse, shall we?
For the rock-dwellers - a TL;DR:
What happened: The hacker is reportedly an 18 year-old, who managed to gain access to Uber’s AWS, Google G Suite, Slack workspace, VMWare vSphere environment, and internal finance data. A worst case scenario, if there ever were one;
How they did it: They were able to access the network by socially engineering an employee into approving an MFA prompt and gaining VPN access. From there they found a PowerShell script sitting on an exposed network share that contained creds for the admin user of the Thycotic Priviliged Access Management tool, granting them the ability to authenticate to Uber’s other production systems;
Security Company Group-IB have made the interesting observation that stolen OneLogin creds - potentially obtained through RaccoonStealer/Vidar infostealer infections on employee devices - could have facilitated initial access. It’s unconfirmed at this stage, but definitely plausible given the volume of creds up for sale on dark web marketplaces;
Where it’s up to: Uber’s response is - unsurprisingly - ongoing. Their latest update states they’re working with law enforcement, and no evidence of “sensitive information” being compromised has been identified (side note: “sensitive” is subjective).
If you’re after more, check out the initial coverage from vx-underground, and this thread that provides a pretty detailed wrap-up of the attack chain.
Key Takeaways:
This breach is just the latest in an emerging trend of compromised credentials, MFA fatigue (spamming an employee with MFA requests until they approve them) and Call-back Phishing/Vishing being abused to bypass MFA protections and gain a foothold in victim networks.
Don’t forget about Infostealers - Initial Access Brokers have gotten a lot of attention lately, but are just one way to crack the perimeter. Infostealers are ubiquitous, and provide valid credentials that can achieve the same effect with a bit of social engineering and weak Conditional Access Policies in place;
MFA is not enough on its own - The recent 0ktapus campaign has already demonstrated how simple phone-based social engineering can coerce users into approving MFA prompts; while simply spamming an employee with MFA requests until they approved them (MFA fatigue) enabled hackers to gain access to Cisco’s networks. Don’t despair though, here are a couple of steps to help mitigate this:
Enable number matching for Azure AD MFA prompts, and give them context on where the login attempt is coming from so they can judge if it’s a dropped VPN trying to re-authenticate, or a hacker in Argentina trying to mess with them. These measures, combined, can help mitigate MFA fatigue and social engineering attempts;
Implement layered Conditional Access Policies, in addition to MFA. E.g. user must be on an MDM-enrolled device with EDR installed; connected to the corporate VPN, and have approved a number-matching MFA prompt to authenticate;
Use physical FIDO tokens as your MFA factor - remote attackers can’t easily spoof or socially-engineer this, so they’re much more resilient than both soft and hard tokens;
Reduce session-token validity to 24-hours to minimise the time an attacker can maintain access before needing to again bypass MFA;
Anticipate compromise - closely monitor Privileged Accounts to compensate for gaps in policy or visibility. Prevention is always ideal, but never a sure thing. Make sure you’re set-up to detect anomalous and unapproved activity by privileged accounts
Found this useful? Why not share it!

Summary of Qakbot, IcedID TTPs
Qakbot and IcedID distribution has continued this week, with TA570 (Obama botnet) joining TA577 (BB botnet) in distributing Qakbot, and IcedID spread using two separate execution chains.
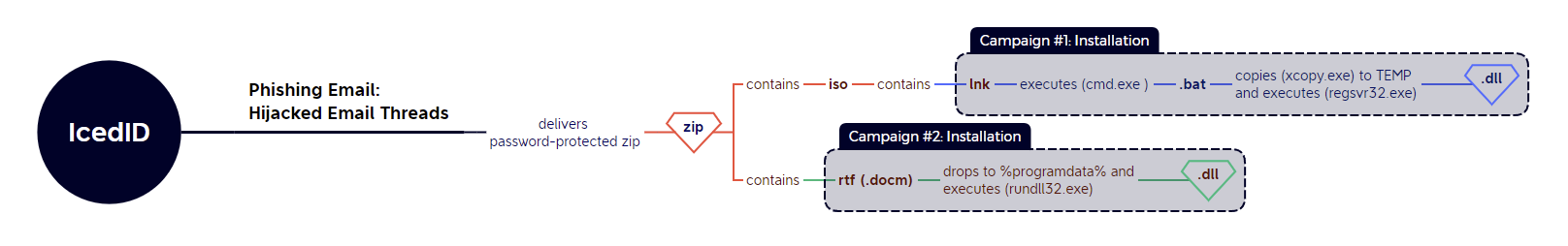
IcedID
Two distinct campaigns were seen this week, using TTPs that were largely unchanged from what we observed in late August.
Campaign #1 - zip > iso > lnk > bat > dll
Reference: @0xToxin
- Distribution begins with hijacked email threads using Invoice and “Stolen Images Evidence” themes;
- This delivers a password-protected zip archive containing an iso which in turn contains .lnk and .bat files as well as a .dll payload;
- Clicking the lnk file executes the obfuscated .bat file, which uses xcopy to copy the IcedID payload to a directory called TEMP and executes it using rundll32.exe.
Campaign #2 - zip > rtf (docm) > dll
References: @0xToxin | Tria.ge
- This campaign also uses hijacked email threads, delivering a malicious rtf document, stuffed into a password-protected zip.
- The rtf document is actually a .docm maldoc, which drops a .dll payload to %programdata% and executes it with rundll32.exe.
Qakbot
Qakbot was being distributed through both the BB (TA577) and Obama (TA570) botnets, with significant overlap in behaviours between campaigns as well as the two botnets themselves.
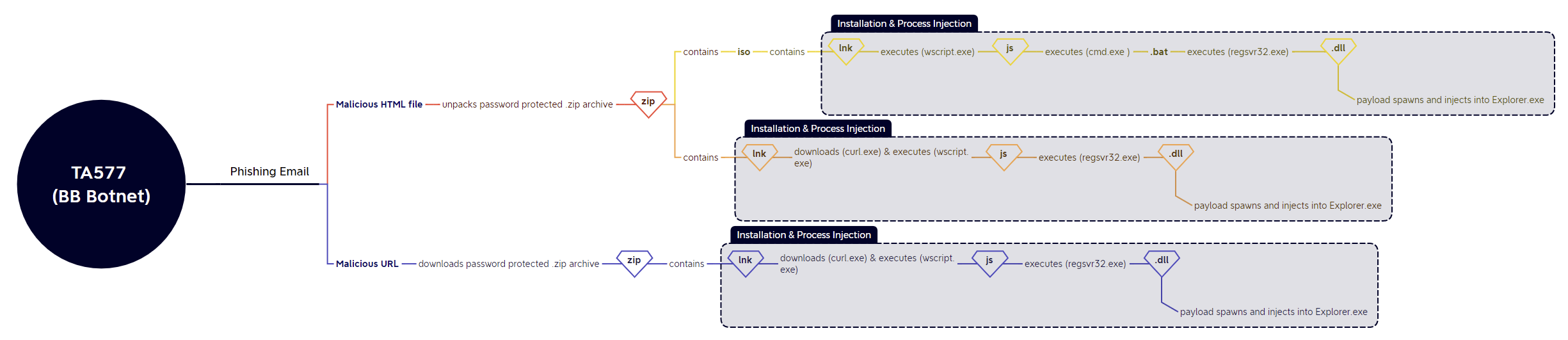
BB Botnet
The BB botnet (TA577) changed its payload delivery sequence several times throughout the week:
13/09: html > zip > lnk > curl > wscript > dll
References: @pr0xylife | Malware Bazaar | Joe’s Sandbox
14/09 - 15/09: url > zip > lnk > curl > wscript > dll
References: @pr0xylife | Malware Bazaar | Tria.ge
16/09: html > .zip > .iso > .lnk > .js > .bat > .dll
References: @pr0xylife | Malware Bazaar | Joe’s Sandbox
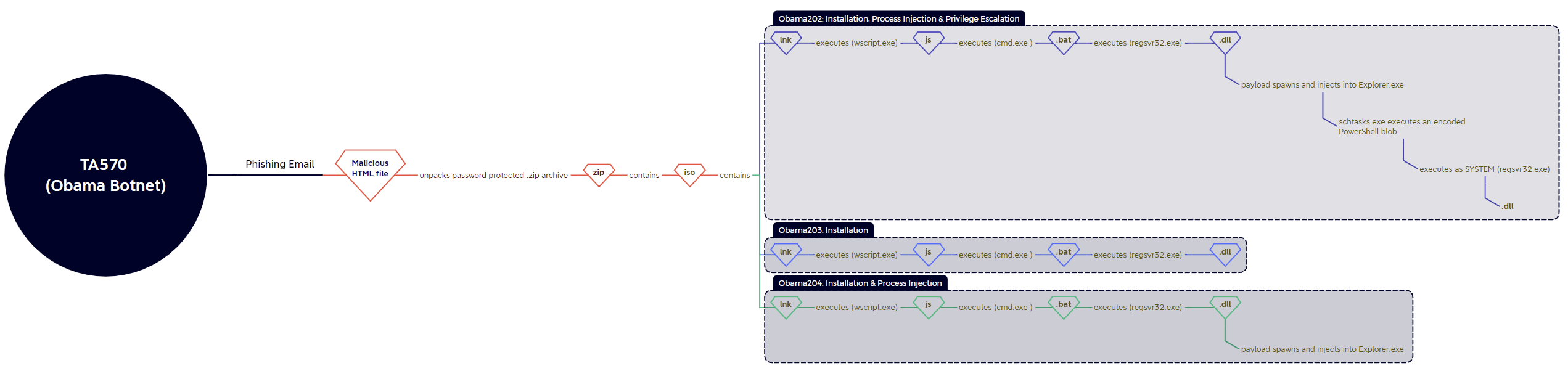
Obama Botnet
The Obama botnet (TA570) used the same initial installation chain, with varying results in process injection & privilege escalation:
14/09 (Obama202): html > .zip > .iso > .lnk > .js > .bat > (regsvr32) .dll > explorer > schtasks > powershell > regsvr32 .dll (as SYSTEM)
References: @pr0xylife | Tria.ge
15/09 (Obama203): html > .zip > .iso > .lnk > .js > .bat > (regsvr32) .dll
Reference: @pr0xylife
16/09 (Obama204): html > .zip > .iso > .lnk > .js > .bat > .dll > explorer
References: @pr0xylife | Tria.ge
Detection Opportunities
The overlaps present opportunities that we can detect on. Specifically:
- Use of malicious html files with trailing embedded JavaScript code that unpacks a password-protected zip file;
- Use of lnk > js > bat > dll execution chains;
- Process injection into explorer.exe.
@Max_Mal_ also did some deep dives into a TA577 sample, finding other potential targets the malware could use for process injection: msra.exe, explorer.exe, OneDriveSetup.exe. Separately, @Kostastsale found samples injecting into wermgr.exe - another one to add to the watchlist!
Thanks for reading! If you liked this, please subscribe for free to receive new posts and support my work!





